Recent News & Events
2022.03.25 Big Sale for WFH VPN User with Thales SAS (Cloud) 2-Factor Authentication
Good News!! As WFH becomes normal due to the presence of COVID-19. However, it does not secure enough to access the company's IT infrastructure without using 2-Factor Authentication. Therefore, UDS is now having a promotion program for token of Thales OTP 110 + SAS software license for 2FA of SSL VPN / VPN. This solution can support different VPNs that contains RADUIS settings including Sangfor, Hillstone, Paloalto, Checkpoint, Pulse Secure, Sophos, SonicWall, WatchGuard, etc. And Sangfor has provided a great support to our program.
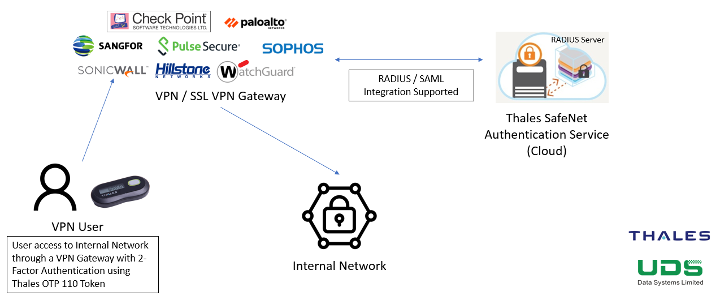
Question:
1.) What are Thales OTP 110 and SAS Software Subscription licenses?
ANS: For Thales OTP 110, it is a One Time Password authentication device with LCD display, battery, and OTP generation button.
For Thales SafeNet Authentication Service (SAS) is a cloud-based authentication platform making authentication easy and cost-effective to implement and manage. Our approach has been to design a solution that takes away many of the traditional pain points in authentication.
2.) Why do I need the OTP?
ANS: It provides a Two-Factor Authentication to enhance the VPN Security to access the company's IT infrastructure and prevent hacking from Man-in-Middle-Attack.
3.) How secure is the SAS?
ANS: Only Admin can login the Console Using OTP Token to generate 6-digit code. Or Using Mobile Token to generate 6-digit code in 'Mobile Pass' Application.
From now, customers can enjoy a special price as shown below.
| Order Quantity |
Price for OTP 110 +
SAS for 3 Years(HKD per unit) (Included remote SAS installation) [Original price: HKD1,500.00 per OTP 110 + 3 Years SAS license + 3 Years Limited Hardware Maintenance without installation] |
| 25-49 |
HKD 1,000 (1
unit OTP 110 + 3 Years SAS license
+ 3 Years Limited Hardware
Maintenance + remote
installation), Average HKD333.33
per user per year |
| 50+ |
HKD 900 (1
unit OTP 110 + 3 Years SAS license
+ 3 Years Limited Hardware
Maintenance + remote
installation), Average HKD300.00
per user per year |
The promotion is valid to Jul 31, 2022. If you have any inquiries about the program, please contact Daniel Tai (email: danieltai@udshk.com; Tel: 2851 0271)
2022.03.15 Work From Home Cause Data Leakage?

Data Leakage?
Due to the COVID 19 situation, more and more company will have their staff to work from home (WFH). Most of the companies have already applied protection on their confidential data in their whole enterprise network and working environment but not for WFH situation. Staffs are using Remote Desktop, VPN, VDI method to access the corporation network, However, what they pain for is the content showing on the screen. It’s a plain text without any encryption. Sensitive Data may be easy to be leaked by screen capture, or even using a mobile device to take a photo. More and more company is asking for solution to enhance the security of the content on the screen.
  |
To solve this, Screen Watermark become an important part to enhance the data protection. xSecuritas Screen Watermark is designed to protect screen content and to claim ownership of an asset. With the xSecuritas product, you can enjoy below features.
- Display ScreenWatermark on target machine with traceable information
- Display Watermark depending on the location, Like Office or Out of Office?
- Display on the participant's screen when sharing the screen or only sharing content in video conferencing
- Supports Screen Watermark in VDI and RemoteApp of Microsoft, Citrix, VMWare Horizon, AWS Stream, Nutanix
- Support Screen Capture Blocking
- Compatible with Windows 7, 10,11, Windows Server 2012 R2, 2016, 2019 or above OS
Real Case Sharing
One of the Bank in Hong Kong deployed the solution before the COVID 19 to enhance their internal security on those VDI server. Recently, caused by the extreme condition of COVID 19. Most of their staffs are work from home with company laptop. They are aware that this may have a risk to spread out some confidential information or even bank customer information. They then start to implement the screen watermark solution to their staff’s laptop. The solution is running smooth with their expected result. For now, they have more than 1,000 users already using the solution to work from home.
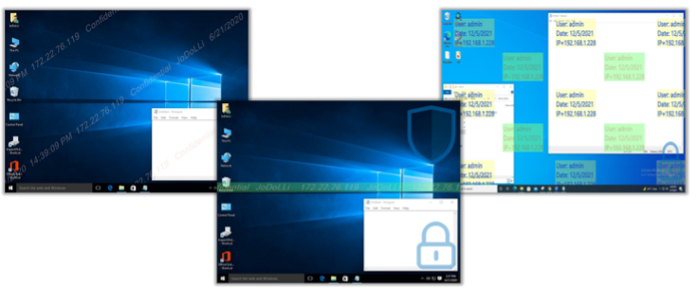
Questions
Q. Can the watermarks display only when the user out of office?
A. Yes, We can apply based on the agent network location to display the watermark.
Q. Do I need to install any software in my environment?
A. Yes, you will need to install our agent on each machine. But no policy server is required, as our policy server is cloud based.
2022.02.25 UDS Data Systems is on Sub-Contractor of Standing Offer Agreement for Quality Professional Services 5 (SOA-QPS5)

OGCIO’s The Standing Offer Agreement for Quality Professional Services 5 (SOA-QPS5) enlarges the Government's delivery capacity for IT services and accelerates the delivery of IT solutions to support the increasing demand of digital government services. The contract period of SOA-QPS5 is from 31 January 2022 to 30 January 2026 covering three Categories of services:
● Category A: Pre-implementation, programme/project management services, ongoing services, implementation and combined system development services;
● Category B: Information security, privacy assessment and independent testing services; and
● Category C: Deployment and maintenance of common services.
Categories A and C are further divided into Major and Minor Group. Minor Group covers work assignments of contract value not exceeding HK$3 million, while Major Group covers work assignments of contract value over HK$3 million but not exceeding HK$20 million. For Categories B, there is no subdivision into Groups and the contract value of each work assignment shall not exceed HK$20 million.
UDS Data Systems Limited is now on the sub-contractor list of QPS-5 Cat A, Cat B and Cat C.
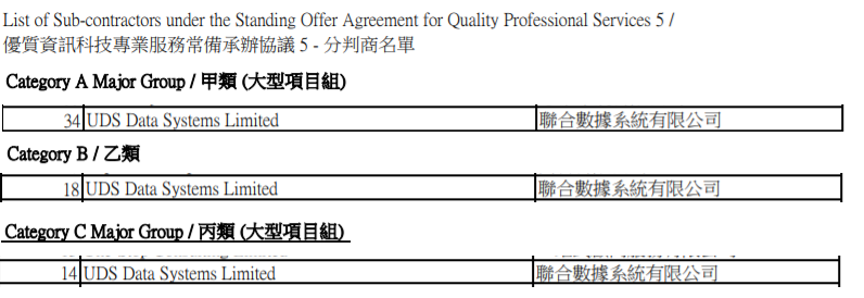
For details, please refer to the below link
https://www.ogcio.gov.hk/en/our_work/business/business_window/doc/SOA-QPS5_subcontractors.pdf
2021.02.01 UDS represents SecIron products in Hong Kong

UDS welcomes SecIron (www.seciron.com) joins our product family to enhance UDS’s mobile Mobile Application Security solutions.
SecIron is founded in 2010 by a team of specialist and experts in the field of Mobile Application Security across Asia. SecIron committed to creating a secured mobile future through innovation and development of Mobile Application Security technologies in safeguarding business and communities from cybercriminals and mobile threats.
From SecIron’s research & development center headquartered in Tokyo, Japan, her specialists continuously develop future-proof mobile application security solutions that are easy to implement through a code-less holistic approach, making mobile threats a thing of the past.
Product families
SecIRON Solutions For
➢ Financial Industry
➢ Retail & E-Commerce
➢ Mobile Gaming
➢ IoT Industry
➢ Public Services
➢ SaaS Industry
➢ Healthcare Industry
2021.12.21 Log4j Vulnerability and IT Security Vendors' Responses
What is the Log4j Vulnerability?
A flaw in widely used internet software known as Log4j has left companies and government officials scrambling to respond to a glaring cybersecurity threat to global computer networks.
The bug disclosed last week could enable potentially devastating cyberattacks that span economic sectors and international borders, according to security experts.
U.S. officials say that hundreds of millions of devices are at risk, while researchers and major technology companies warn that hackers linked to foreign governments and criminal ransomware groups are already probing how to exploit the vulnerability within targets’ computer systems.
CISA (Cybersecurity and Infrastructure Security Agency) published an open-sourced log4j-scanner derived from scanners created by other members of the open-source community on 12/22/2021. This tool is intended to help organizations identify potentially vulnerable web services affected by the log4j vulnerabilities. This repository provides a scanning solution for the log4j Remote Code Execution vulnerabilities (CVE-2021-44228 & CVE-2021-45046).
CISA Log4j Scanner Download:
https://github.com/cisagov/log4j-scanner
What is Log4j?

Software developers use the Log4j framework to record user activity and the behavior of applications for subsequent review. Distributed free by the nonprofit Apache Software Foundation, Log4j has been downloaded millions of times and is among the most widely used tools to collect information across corporate computer networks, websites and applications. The software is maintained by Apache volunteers.
How can hackers take advantage of Log4j's vulnerability?
The Log4j flaw, disclosed by Apache on , allows attackers to execute code remotely on a target computer, meaning that they can steal data, install malware or take control. Some cybercriminals have installed software that uses a hacked system to mine cryptocurrency, while others have developed malware that allows attackers to hijack computers for large-scale assaults on internet infrastructure.
Security experts are particularly concerned that the vulnerability may give hackers enough of a foothold within a system to install ransomware, a type of computer virus that locks up data and systems until the attackers are paid by victims. Security company F-Secure Oyisaid its analysts have observed some ransomware variants being deployed via the flaw already, along with malware that is often deployed as a precursor to a ransomware strike.
The above information is retrieved from the WALL STREET JOUNRNAL. For further information, please go to https://www.wsj.com/articles/what-is-the-log4j-vulnerability-11639446180
2 CVEs for the Log4j vulnerabilities disclosed by Apache
| SECURITY VULNERABILITY CVE-2021-44228 | SECURITY VULNERABILITY CVE-2021-45046 | |
| Addressed in | Log4j 2.12.2 and Log4j 2.16.0 | Log4j 2.12.2 for Java 7 and 2.16.0 for Java 8 and up |
| Summary | Log4j’s JNDI support has not restricted what names could be resolved. Some protocols are unsafe or can allow remote code execution. | Apache Log4j2 Thread Context Message Pattern and Context Lookup Pattern vulnerable to a denial of service attack. |
The above information is retrieved from Apache official website. For further information, please go to https://logging.apache.org/log4j/2.x/security.html
How IT Security Vendors handle the Log4j Vulnerabilities?
Many IT Security Vendors have traced attempted attacks that exploit the this vulnerabilities. Each has released the security patch or signatures and provide the recommendation on how to against this attack to protect their customer business.
Please click on the Vendors’ logo for further information on their responses.
 |
||
2021.12.03 Congratulations to our staff achieving the CSPA 2021 award
Congratulations to our Director, Mr. Frankie Leung, Director of Security Services, Mr. Paul Chow, and Technical Manager, Mr. Eric Moy for achieving the CSPA (Cyber Security Professionals Award) 2021 award.
Mr. Frankie Leung, Mr. Paul Chow and Mr. Eric Moy were nominated to Cyber Security Professionals Awards (CSPA). They were selected by the judges for two Merit awards and one Silver award in the Government Departments & Public Bodies – Management category and the Information and Communications Technology – Practitioner category from 200 participants in each category. The organizer (Cyber Security and Technology Crime Bureau of the Hong Kong Police Force) and supporting organizations believed their contributions and practices have demonstrated the highest degree of excellence in the field of cyber security.
To recognise our excellence work, Cyber Security and Technology Crime Bureau of the Hong Kong Police Force invited our awarded members to join the awards presentation ceremony on 2 December 2021 (Thursday), at the Hong Kong Science and Technology Park, Shatin.
2021.10.25 UDS join Palo Alto Networks’s Partner Executive Luncheon and got Excellence in Cortex XSOAR FY21 Award
On Oct 12, Palo Alto Networks’s Partner invited UDS Data Systems Ltd to join the Partner Executive Luncheon start at Sushi Kuu Japanese Restaurant at Central, Hong Kong.
The top executive of Palo Alto Networks presented the topic of “We’ve got Next”. which were covering:
- Palo Alto Networks strategy and roadmap
- Award presentation to celebrate our partner success in FY21
- Social Networking how we may work together
Mr. Frankie Leung (Director of UDS) represented UDS to get the Excellence in Cortex XSOAR FY21 Award from the Top Management of Palo Alto Networks. UDS is focusing the SIEM and SOAR solution in the security market. UDS works with Palo Alto Networks to win a few cases of Palo Alto Networks’s XSOAR in Hong Kong market in 2021.
One integrated platform for security operations – Cortex XSOAR
Shift from dozens of siloed SOC tools to Cortex and unleash the power of analytics, AI and automation to secure what’s next:
- Collect all your security data in one place for full visibility and faster investigations
- Reclaim your nights and weekends by automating manual SOC tasks
- Stitch together network, endpoint, cloud and identity data to accurately detection threats
- Get a single source of truth for all your public-facing assets and synchronize findings with other tools
- Ensure all your IT and security tools play well together with hundreds of out-of-the-box integrations
2021.06.27 UDS has joined the Palo Alto Virtual Cybersummit 2021
Palo Alto organized the Virtual Cybersummit 2021 with the theme ‘Better safeguard networks from cyberattackers’ from June 21-25, 2021. UDS joined this great event by holding an online booth which presented our capabilities on providing security services and solutions, especially our capabilities on CortexTM XSOAR such as Playbook design and implementation.
SOAR (Security Orchestration, Automation, and Response) is a solution stack of compatible software programs that allow an organization to collect data about security threats from multiple sources and respond to low-level security events without human assistance. CortexTM XSOAR, a single platform that orchestrates actions across your entire security product stack for faster and more scalable incident response, has cooperated with us for several years. With this, our team has accumulated professional experiences and knowledge on handling the different situations for XSOAR. We believe that we can provide excellent services to the customers and fulfill their requirements.

If you are interested in XSOAR or other security products/services, please visit our website or contact us (email: info@udshk.com / Tel: +852 2851 0271).
2021.6.1 The latest version of DriveLock
The latest version of DriveLock is now available. It mainly provides five different services for the customer to enjoy a more comprehensive service as shown in the graph below:
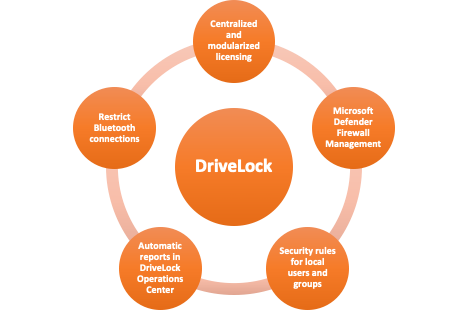
1.) Centralized and modularized licensing -> DriveLock’s new license modularisation is optimally adapted to customers’ needs.
2.) Microsoft Defender Firewall Management -> With DriveLock, you can specify precise rules for any group of people, computer or network environment, as well as the particular time of day. Our ‘fine-tuning’ is now also available for Microsoft Defender's firewall rules - simply disable port sharing for computers in home offices (it’s only required in the corporate network), or restrict communication to encrypted connections.
3.) Security rules for local users and groups -> DriveLock 2021.1 comes with extra protective features, allowing you to rename accounts and provide them with the ability to change and randomize passwords.
4.) Automatic reports in DriveLock Operations Center
5.) Restrict Bluetooth connections -> DriveLock 2021.1 now allows detailed settings for connecting devices via Bluetooth.
If you still want to figure out more about the latest version of the news, it is recommended to attend the webcast on 8th June 2021. Andreas Fuchs (Director Product Management in DriveLock) will briefly discuss the news update and will also answer your question with his expertise. The registration link will be shown below.

For more information, you can visit https://www.drivelock.com/ or content us (email: info@udshk.com / Tele: +852 2851 0271).
2021.04.10 Teramind software joined UDS Security Solution Offering as their authorized partner in Hong Kong

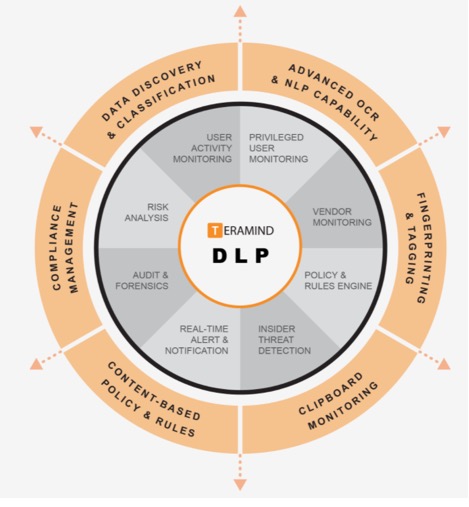
Teramind (Found in 2014) is a software solution that leading in monitoring employees, user behavior analytics, insider threat detection, forensics, and data loss prevention software solution. With the specialty in detecting, recording, and preventing malicious user behavior in addition to enhancing the productivity and efficiency of the teams. Until now, over 2,000 organizations in finance, legal, retail, manufacturing, energy, technology, healthcare, and government have cooperated with Teramind.
| Feature of
Teramind |
||
1.)
Employee Monitoring • Identify uncover potential threats in real-time |
2.)
User Behavior Analytics • Identify uncover potential threats in real-time |
3.)
Data Loss Prevention • Leverage Teramind’s industry-defining DLP feature |
4.) Forensics • Identifying and alerting the user to non-complicit action through compliance or audit |
5.)
Insider Threat Prevention • Automate risk detection and block unwanted users’ behavior. |
Teramind DLP: Data Loss Prevention, User Activity Monitoring and Insider Threats Detection in a Single Platform especially in WORK FROM HOME environment.
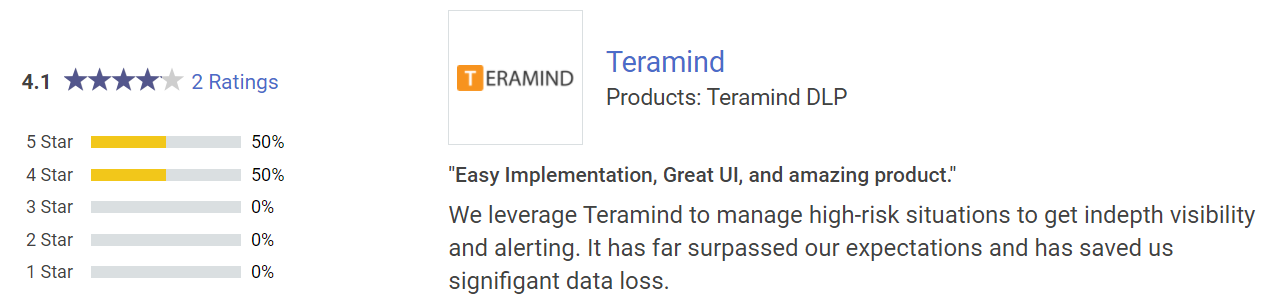
Gartner peerinsights - Enterprise Data Loss Prevention (DLP) Reviews and Ratings
Gartner had rated two products of Teramind (Termind DLP and Teramind UAM with 4.1 and 4 out of 5) to praise Teramind’s award-winning platform.
For more information, you can visit https://www.teramind.co/ or content us (email: info@udshk.com / Tele: +852 2851 0271).
2021.05.17 QI-ANXIN(奇安信) appointed UDS Data Systems as their authorized partner in Hong Kong
 |
|
QI-ANXIN Technology
Group Inc. (hereinafter referred
to as QI-ANXIN, China Main board
stock code 688561) was founded in
2014 and specializes in serving
the cybersecurity market by
offering next generation
enterprise-class cybersecurity
products and services to
government and businesses. With
its continuous commitment to
R&D innovation and security
capabilities centered on actual
offensive and defensive, the
company has grown to be a domestic
leading cybersecurity provider
with its strength built on big
data, artificial intelligence and
security operation technology.
QI-ANXIN is the Official Cyber
Security Services and Anti-Virus
Software Sponsor of the Olympic
and Paralympic Winter Games
Beijing 2022. The company has also
established business presence
outside Chinese mainland, such as
in Hongkong, Indonesia, Singapore,
Canada etc. |

QI-ANXIN is one of the largest cybersecurity enterprises in China. It is known for its groundbreaking achievements in the fields of big data and security intelligence, terminal security protection, security operation and emergency response. It has long been committed to providing business-level cybersecurity technology, products and services to governments, enterprises and education & financial institutions, and safeguarding the cybersecurity of government, corporate and individual users in an all-round manner.
Effective from Sept of 2020, UDS carries full range of QI-ANXIN cybersecurity products, solutions and services. “We believed QI-ANXIN, not only brings us the product and services, but also the Mainland China made state of art arts cybersecurity experience and end to end solutions to our value customers in Hong Kong” said by Frankie Leung, Director of UDS Data Systems Ltd.

2021.05.10 Our Director of Security Services, Mr. Paul Chow delivers a talk in Cybersec Infohub about Mobile Apps - Secure by Design
 |
|
Cybersec Infohub is going to organize an online Technical Professional Workshop on 28 May 2021 (Fri) titled "Secure and Protect Your Customer-facing Applications" to share latest attack and protection toward website and mobile apps. Cybersec Infohub Technical Professional Workshop - Secure and Protect Your Customer-facing Applications |
Organizer: The Office of the Government Chief Information Officer (OGCIO)/ Hong Kong Internet Registration Corporation Limited (HKIRC)
Date: 28 May 2021 (Fri)
Time: 15:00 - 16:00
Format: Zoom Webinar
Language: Cantonese
Target audience: Technical staff such as security professionals, application developers, application administrators, project manager etc.
| Time |
Topic |
Guest Speaker |
| 15:00 – 15:20 |
Importance of
Regular Health Check of Your Web
Application • Demo on vulnerability scanning |
HKIRC |
| 15:20 – 15:40 |
Latest Attack
Targeting Web Application - Demo on latest attack tactics / exploit vulnerabilities - Most common issues on web applications Mobile Apps - Secure by Design - Points to note on security by design - Mobile app security testing / hacking demo |
UDomain Web Hosting
Company Limited (TBC) |
| 15:40 – 16:00 | Mobile Apps -
Secure by Design - Points to note on security by design - Mobile app security testing / hacking demo |
Paul CHOW CISSP, CEH, OSWP, CDPSE Security Researcher Mobile Security Research Lab (an UDS Security Research Lab) |
About Cybersec Infohub
Cybersec Infohub is a partnership programme jointly administered by the Office of the Government Chief Information Officer (OGCIO) and the Hong Kong Internet Registration Corporation Limited (HKIRC) to promote closer collaboration among local information security stakeholders of different sectors to share cyber security information and jointly defend against cyber attacks.
2021.03.18 UDS strengthen its Mobility Portfolio by adding Zello Push-to-Talk Solution
 |
 |
The Leading Push-to-Talk App. Zello is the highest rated push-to-talk app, connecting 150 Million users globally, empowering frontline workers, teams, and communities through instant and crystal-clear voice messaging.
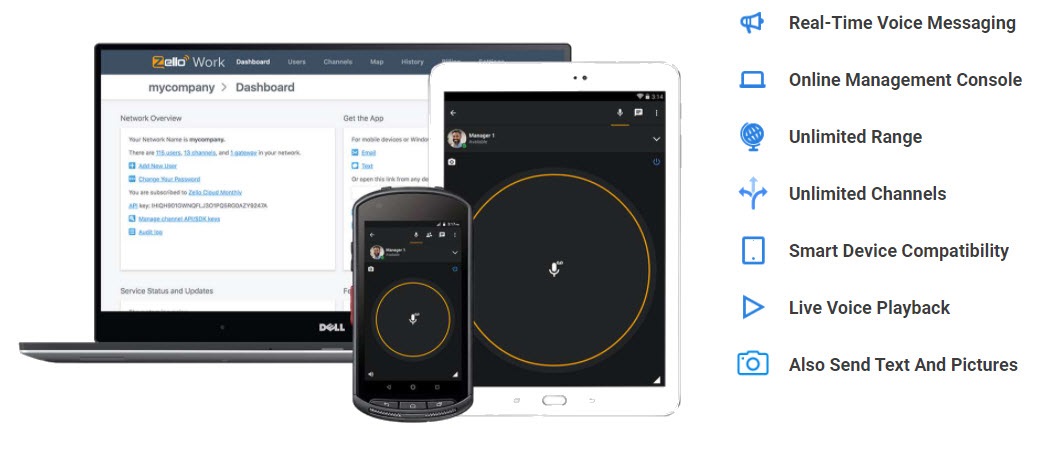
UDS Data Systems Limited (UDS) is proud to announce that we are now the Distributor of Zello Push-to-Talk (PTT) Business Solution in Hong Kong, Macau & China targeting the Government and Enterprise market. Zello PTT solution is available on both On-Premises and Cloud.
About Zello
Zello is the leading push-to-talk(PTT) voice messaging app for teams and businesses worldwide, turning iOS, Android, and Windows devices into walkie-talkies that also record messages, track location, and send emergency alerts. Account administrators add, remove, and group together teams through a centralized, web-based management console. Channels are flexible to suit the needs of each customer, especially those in the hospitality, manufacturing, construction, transportation, and retail industries. Zello is ideal for businesses with deskless workers, field workers, remote workers, and lone workers. Use cases in this category include hotels with various staff members, construction crews on noisy job sites, and retail salespeople on the sales floor. Join the millions of Zello users who communicate in real-time over any wireless or data network to share updates, connect in emergencies, and solve problems.
Zello serves thousands of businesses and has more than 150 million users worldwide. Current customers include Honda, Restoration Hardware, Starwood/Marriott Hotels, Uniqlo, Waste Management (WM), and YRC Freight. Zello is recognized as a reliable communication solution by reputable sources like the Wall Street Journal, the New York Times, CBS, CNBC, USA Today, and TechCrunch. In Hong Kong, there are more than 400K active users using Zello Push-to-Talk App to communicate especially in the Taxi Industry.
The Zello Push-to-Talk Enterprise Solution Modules
Base Service Plan with Central Management Console: Each Zello Business Customer will have a Centralize Cloud Management Console. Administrator can Manage your users, channels, setting and assign team members to channels from the web. The following are optional add-on modules:
Message Vault: Message Vault is the Zello add-on feature that saves all user and channel communication to the cloud for up to two years. If your organization requires archival and retrieval of messages, you should consider adding the Message Vault feature to the base plan. You can perform these tasks within Message Vault:
- Filter by date, recipients, individuals, channels, and type of message
- Play voice messages, open images and read text alerts
- Download voice messages/images or export metadata.
Emergency Alerts: The Emergency Alert add-on feature is meant to be used during emergency situations by users in distress. In an emergency, users can press a button to alert a group of people of their situation. All Zello contacts have this button available on each talk screen, and emergency calls will be managed from the designated emergency channel. When the emergency mode is triggered:
- The channel will automatically record 10 seconds of uninterrupted audio for the user who presses the emergency button.
- The location of the user who pressed the Emergency button will automatically be shared with the Emergency channel.
- All other messages sent to anyone placed in Emergency mode will be marked as missed and placed in History.
- Only the user who initiated the Emergency mode may end the Emergency mode.
- Other users who may also find themselves in distress can initiate Emergency mode via a different channel or Ad-hoc channel and will be transferred into the Emergency channel.
Premium Maps: Premium Maps is an optional add-on to your ZelloWork push-to-talk base plan allowing you to track your Android and iOS users from the Map in the Zello Management Console. Search for the location of specific team members by username, or select them directly from the map. Configure live location tracking update intervals to suit your needs – from five seconds to precisely track movements on foot, up to five minutes to save battery life. Quickly identify inactive team members with color-coded status indicators. Premium Maps includes:
- Live Location
- Location History with breadcrumbs
- Real-time Traffic
- Google Maps
Zello Enterprise Server: Zello PTT can work on-premise server solution operates even when Internet access is unavailable or unreliable. Zello with local intranet works well anywhere from an isolated warehouse to the outskirts of the city.
About UDS Data Systems Limited
UDS is an IT solutions provider specialized in Big Data, Value Added Cloud Services, Mobility Solutions & Information Technology Security. Our comprehensive end-to-end security solutions and professional services help enterprises to build their next-generation systems securely. Beside Information Technology Security, we are also well known by our customers and our Telecom & IT partners on our expertise on Apple iOS, Android, EMM/MDM (Mobile Device Management) products & related solutions. Since 2008, our Mobility Products/Solutions Team has successfully helped many Corporations and Government Departments in Hong Kong, Macau and China to implement Mobile Solutions on more than 100,000 Devices.
SEE Zello Push-to-Talk in Action
Please contact our Product/Solution Director Norman Chan (Mobile #: +(852)-90724718 or Email: normanchan@udshk.com) if you are interested in learning more about the Zello ways to improve your Communications, Productivity and Management.
2021.02.19 UDS provides supporting service for Courses of Cyber Range Training Centre that adopting HKGov programme – IT-Lab
We are pleased to announce that UDS Data Systems Ltd. provides consulting service on how to adopt information technology for education sectors, providing the IT-Lab courses that fulfills the requirements that are eligible to apply for funding under HKGOV initiative, “IT Innovation Lab in Secondary Schools” (IT Innovation Lab) initiative under the existing scheme "Enriched IT Programme in Secondary Schools” (EITP).
For IT-Lab courses outline that providing by Cyber Range trainer center, please check the links below:
URL: https://cyberrange.hk/IT-Innovation-Lab-IT-Lab/
· Cybersecurity Essential
· Introduction to CTF
· IOT Security
· IOT Lab
Enquiry / Registration:
Please contact us at (852) 28510271 for further details.
22020.12.18 Secure Your Everything: Recommendations on recent incident from SolarWinds

1. Reset passwords of local SolarWinds users and follow all updates released from SolarWinds as the first step
2. Make sure you have updated your software patch with the latest version, click here to learn more on our response to SolarWinds supply chain attack
3. If you want to check on the security level of your organization, contact Check Point’s Incident Response (IR) Team through UDS Data Systems Ltd. and conduct a "Compromise Assessment Service"

2020.12.03 UDS provides service that adopting several programme – D-Biz, TVP, RTTP
We are pleased to announce that UDS Data Systems Ltd. provides consulting service on how to adopt information technology for business, that fulfills the requirements that are eligible to apply for funding under the Distance Business (D-Biz) Programme, Technology Voucher Programme (TVP) . For Reindustrialisation and Technology Training Programme(RTTP), UDS registered as a qualified course provider. For more detail, please check the links below:
a) Distance Business Programme D-Biz
Each eligible enterprise may receive total funding of up to HK$300,000 to undertake a project to be implemented within six months.
b) Technology Voucher Programme TVP
Each eligible applicant may receive a cumulative funding ceiling per enterprise/organisation: HK$600,000 for a maximum of six projects.
c) Reindustrialisation and Technology Training Programme RTTP
Each eligible company may be subject to a funding ceiling of HK$500,000 in each financial year for training their staff in advanced technologies.




Enquiry / Registration:
Please contact us at (852) 28510271 for further details.
2020.11.10 Cyber Range Training Centre Training Courses and Workshops
Cyber Range Training Centre (CRTC), powered by Cyberbit Limited, the world’s leading incident response platform widely adopted by enterprises, governments, academic institutions and MSSPs around the world, is the first IT security defense training centre equipped with the latest and largest scale of simulation system in Hong Kong.
Besides hyper-realistic Blue Team training courses, CRTC regularly offers a series of IT security certification training courses and workshops at its centre. These courses can even be tailor-made to meet your business needs. Please check out our latest courses and schedule at https://cyberrange.hk/schedule/. CRTC and UDS Data Systems Limited collaborates to apply RTTP Training Programs such as Security Awareness Training – Anti Phishing Workshop. More and more courses will be under the RTTP funding in future.
Course: Business Continuity Professional Essential (BCPE)
Description: Business Continuity Planning (BCP) is critical to the success of businesses and Industry 4.0 adoption. BCP is used to create and validate a practiced plan for how an organization will recover and restore partially or completely interrupted critical function(s) within a predetermined time after a disaster or extended disruption. The Coronavirus (COVID-19) virus outbreak is impacting businesses all over the world. Whether the operations might already greatly affect, or the impacts are yet to be felt, a business continuity plan is essential to ensure that it can be as resilient as possible in this global health crisis. This course will cover this topic and will provide the method to archive Business Continuity in Industrial 4.0.
Course: Certified Ethical Hacker (CEH)
Description: A Certified Ethical Hacker (CEH) is a skilled professional who understands and knows how to look for weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system(s). The CEH credential certifies individuals in the specific network security discipline of Ethical Hacking from a vendor-neutral perspective. This course will immerse you into the hacker’s mind-set so that you will be able to defend against future attacks. The security mind-set in any organization must not be limited to the silos of a certain vendor, technologies or pieces of equipment.
Course: Certified Information Systems Auditor (CISA)
Description: The Certified Information Systems Auditor (CISA) is a globally recognized standard of achievement among information systems (IS) audit, control and security professionals. For Cyber Security professionals who are interested in the field of audit, CISA certification by ISACA is the leading credential to achieve. In order to face the dynamic requirements of meeting enterprise vulnerability management challenges, this course covers the auditing process, in-depth, to ensure that you have the ability to analyse the state of your organization and make changes where needed.
Course: Certified Information Systems Security Professional+ (CISSP+)
Description: The Certified Information Systems Security Professional (CISSP) is the most globally recognized certification in the information security market. CISSP+ validates an information security professional’s deep technical and managerial knowledge and experience to effectively design, engineer, and manage the overall security posture of an organization. After completing this course, student will be able to handle the exam of CISSP.
Course: Certified Information Security Manager (CISM)
Description: The Certified Information Security Manager (CISM) is an advanced certification that provides validation for individuals who have demonstrated they possess the knowledge and experience required to develop and manage an enterprise information security program. Recent studies consistently rank CISM as one of the highest paying and sought after IT certifications. Our course can help with your professional development and also provides executive management with assurance that you have the required experience to provide effective security management and consulting services. Our intensive training is based on the ISACA framework, which has five domain areas that relate to the role of a CISM. You will learn about each of these domains in detail, giving you the knowledge and skills to develop and manage a resilient information security program.
Workshop: Anti-Phishing Workshop
Description: This is an interactive anti-phishing workshop that helps you understand how phishing attacks work, the tactics that cyber criminals employ, how to spot and avoid a potential attack and most importantly you’ll be improve yourself and less vulnerable to phishing attacks.
With the vision of being recognised as the first choice for security training by our clients, CRTC’s professional training programmes are instructed by our elite experts in cyber security industry with various certifications, qualifications and experience.
Trainer: Mr. Eric Moy

Trainer: Mr. Frankie Leung

Trainer: Mr. Michael Chow

Trainer: Mr. Paul Chow

Enquiry / Registration:
Please contact Mr. Bread Wong at bwong@cyberrange.hk or (852) 28510271 for further details.
2020.11.09 Cyber Range Training Centre & UDS jointly support RTTP Training Program – Anti-Phishing Workshop
 |
 |
 |
Cyber Range Training Centre and UDS Data Systems Ltd. jointly support RTTP Training Program by launching Security Awareness Training – Anti Phishing Workshop. The objective of the workshop is to help candidates understand how phishing attacks work, the tactics that cyber criminals employ, how to spot and avoid a potential attack and most importantly you’ll be improving yourself and less vulnerable to phishing attacks.

Date: 9th Nov 2020
Time: 9:30am – 12:30pm
Workshop of Delivery: Online Instructor-Led deliver thru Zoom video conferencing platform
Prerequisites: Prepare your own smartphone/ laptop/ using internet / email service experience
Suggested Course Fee: HK
Quiz will be provided as a knowledge check that allows re-take if needed. Award of Certificate will be provided as a kind of qualification to enlighten a candidate's career portfolio.
Click here for download workshop detail (pdf/836KB)
Training grant
Companies interested in applying for a training grant for their employee(s) to attend registered public courses should submit the application via online system at least two weeks before course commencement. A list of registered public courses is available for reference. For tailor-made courses, companies should apply for course approval and training grants in one go.
Click here for FAQ of RTTP(pdf/19KB)
Click here for Training grant detail

2020.09.10 Next-Generation Blue Team Workshop
2020.07.02 UDS carries xSecuritas Products
About xSecuritas
 |
|
xSecuritas, Inc. is a company that develops systems related to security. Most security programs are targeted at the enterprise, but xSecuritas wants to distribute the best security programs to its small business or personal as well. |
Screen Watermarks
Display a Watermark in your PC DISPLAY and SCREEN. Your confidential documents and internal applications will have the screen watermark. Even when people taking video or photos of the screen, the Watermark is still shown up. You can display the desired watermark on the screen. This screen watermark does not affect operation of other programs.
Functions
- • Displays watermark on the monitor.
- • Dual monitor support
- • The watermark displayed on the monitor has no effect on existing programs, ie there is no restriction on operations such as mouse clicks.
- • Supports watermark font, size, colour, transparency, location, etc.
- • Watermark support
- • Up to 4 text watermarks
- • Up to 4 image watermarks
Screen Watermarks Enterprise Edition
• Policy concept add to the Screen function.
• The administrator creates screen watermark policies to be distributed to groups or users using Web Console. (You can create multiple watermark policies)
• The same policy can be applied to all users, or each policy can be applied to each group or user.
• Even if the agent program is running, the watermark may not be displayed by the policy.
• The administrator can set the policy applied when logging on to AD, SSO, or agent programs. The administrator can also set the policy applied when logging off.
For more information
You can visit https://www.xsecuritas.com/screen-watermark/ or contact CC Chau (ccchau@udshk.com) for further information.
2020.03.23 Certified EC-Council Instructor
Congratulations to Mr. Eric Moy. He received the Certified EC-Council Instructor (CEI) from EC-Council from Mar 2020.
 |
|
The Certified
EC-Council Instructor (CEI)
program is designed for
individuals who want to become
certified to deliver
EC-Council's suite of
professional certification
programs. The CEI program
provides resources for
individuals to become
industry-recognized trainers
specializing in the field of
information security.
|
 |
|
The International Council of Electronic Commerce Consultants is a professional organization that certifies individuals in various e-business and information security skills. The EC-Council is headquartered in Albuquerque, New Mexico. In 2003, EC-Council was founded by Haja Mohideen and Jay Bavisi. |
The International Council of Electronic Commerce Consultants is a professional organization that certifies individuals in various e-business and information security skills. The EC-Council is headquartered in Albuquerque, New Mexico. In 2003, EC-Council was founded by Haja Mohideen and Jay Bavisi.

2020.02.16 Ways to improve your network architecture ROI and network visibility
 |
|
A compelling ROI analysis is the difference between a successfully funded IT project, and one that gets cancelled. This is especially true for relatively new technologies that are not well understood by IT management. |
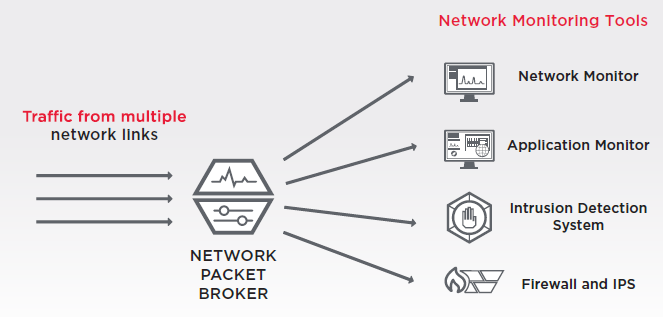
By reading the e-book, you’ll learn five different ways you can use network packet brokers (NPBs) to improve your network architecture ROI:
1. Saving total cost of ownership
2. Expedite troubleshooting
3. Detect breaches faster
4. Reduce the processing burden on your existing tools
5. Extend tool life after a network upgrade
6. Streamline regulatory compliance
IXIA Network visibility solutions are a powerful way to optimize your network monitoring architecture and strengthen your network security. There are many use cases that can be deployed to solve or enhance issues that IT monitoring and security engineers face. The key point is to implement a visibility architecture that creates the fundamental capture and sharing of the valuable data that is needed.
Use cases based upon a visibility architecture will allow you to do the following:
* Access the data you need, when you need it, across the network to properly diagnose problems
* Add/remove security, forensic, and monitoring tools at will for inline and out-of-band monitoring architectures
* Decrease mean time to repair
* Provide a rapid response to crises
* Conduct advanced threat analysis
* Eliminate most, if not all, Change Board approval processes and crash carts for monitoring effort
* Reduce the cost of a breach by connecting tools to the network faster and decreasing the associated MTTR
* Reduce your tool (and SPAN) port programming effort and costs
* Create an architecture that allows you to deploy new inline and out-of-band monitoring solution
Should you have any questions, please feel free to contact us 28510271 or Bread Wong ( breadwong@udshk.com). Thanks.
2020.02.10 Illumio, a cybersecurity leader delivering segmentation solutions, prevents the spread of breaches inside data center, container and cloud environments
 |
|
The Illumio ASP delivers segmentation to prevent the spread of breaches, and to meet regulatory compliance standards such as SWIFT, PCI, and GDPR. Because the perimeter doesn’t stop all bad actors from getting inside data center and cloud environments – or even through to your containers - segmentation from Illumio restricts access to critical systems to only authorized entities. |
Gain visibility and control of containers. Illumio’s ASP delivers a full range of segmentation for containerized hosts:
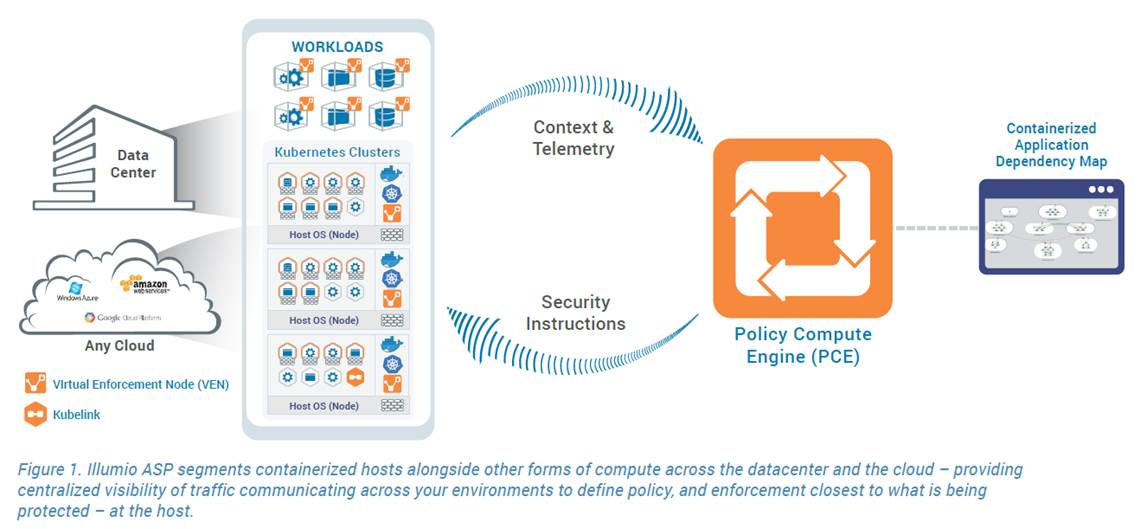
· Centralize visibility of containers alongside other compute environments – gain a single view across containerized workloads and bare metal, virtual machines, private and public cloud - because you can’t protect what you can’t see.
· Enforce uniform policy across containers – and everything else – segment containers along with the rest of your overall data estate, with unified policy, regardless of the environment.
See how to secure your containerized applications running in OpenShift or Kubernetes using Illumio's Adaptive Security Platform.
Demo video example: https://www.illumio.com/resource-center/product-demo-illumio-for-containers?hsLang=en
Should you have any questions, Please feel free to contact Bread Wong ( breadwong@udshk.com ) for more information.
2019.01.16 Thales Vormetric Transparent Encryption for Splunk Repositories, Databases, Files and Disks
With advanced persistent threats (APTs) now common, hackers are actively seeking to steal credit card data, personally identifiable information (PII), critical intellectual property (IP), and other legally protected information to sell to the highest bidder. Some of the most effective tools for fighting these attacks are the security intelligence and threat detection capabilities of SIEM solutions, such as Splunk.
Here there is a recommended solution for you to consider.
Vormetric Transparent Encryption (VTE) delivers data-at-rest encryption with centralized key management, privileged user access control, and detailed data access audit logging that helps organizations meet compliance and best practice requirements for protecting data, wherever it resides. The FIPS 140-2 level 1 validated VTE agent resides at the operating file-system or device layer on a server that has Splunk software installed, and encryption and decryption is transparent to all applications that run above it. VTE provides rich access controls, which allow organizations to determine who can access data, when they can access it, and what type of access they have.
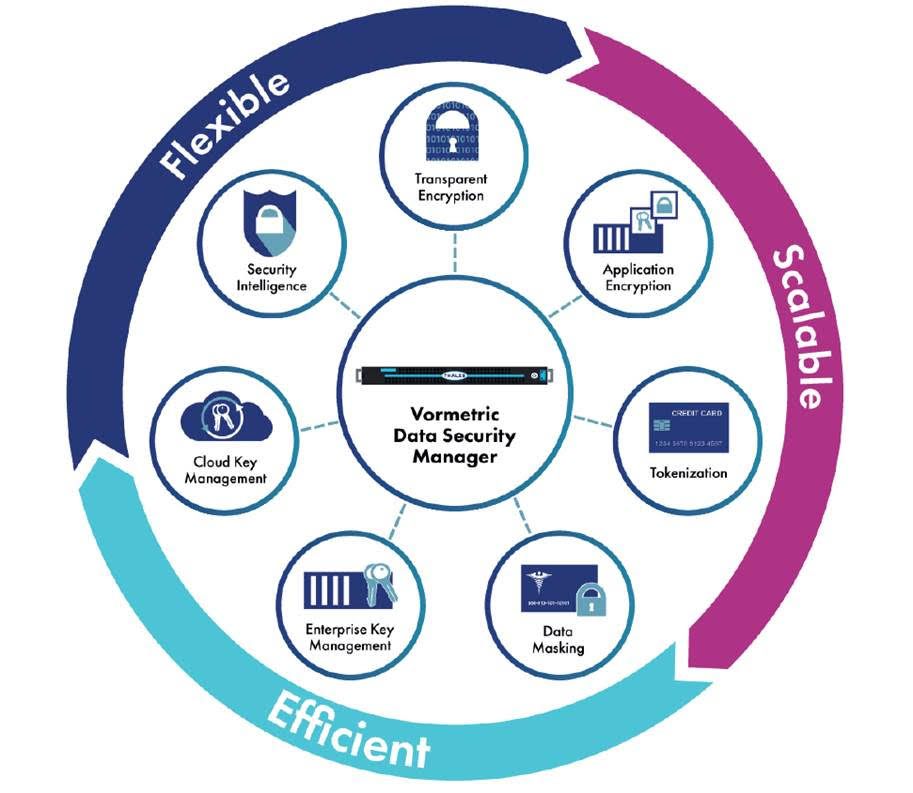
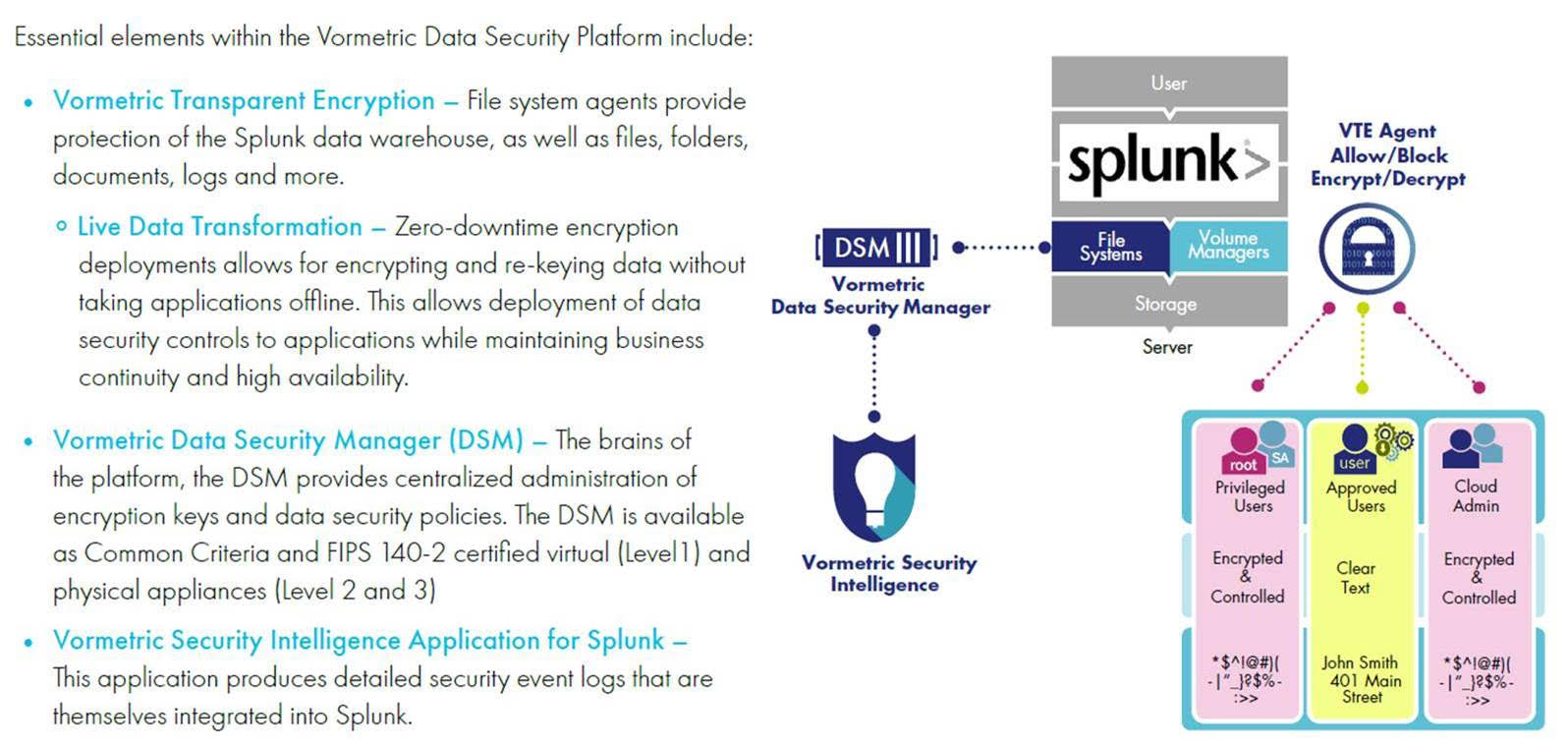
Vormetric Transparent Encryption agents are distributed and optimized for specific file system and encryption acceleration hardware across servers, resulting in very low latency and overhead. Agents employ logic and fine-grained policies defined by the DSM to evaluate attempts to access protected data, and then grant or deny access; all activities taking place around the protected data are logged. The agents have been deployed in tens of thousands of servers, making them the right solution for Splunk Enterprise Big Data requirements.
For more details, please contact UDS Data Systems Ltd at (852) 2851 0271 or email to breadwong@udshk.com
2020.01.07 Switch to Sophos Intercept X Advanced

By combining cutting-edge technologies including deep learning and endpoint detection and response, Intercept X delivers unmatched protection against unknown malware, exploits, and ransomware.
• Proven protection: Intercept X consistently receives top marks in third-party endpoint protection tests.
• Unmatched defenses: With Sophos, you get features not available with other vendors, including:
• CryptoGuard, which uses behavioral analysis to stop never-before-seen ransomware
• Exploit prevention, blocking more exploit techniques than anyone else
• Easier management: You can manage and protect all your devices through a single, cloud-native console.

Offer 2 comes with one year of Network Protection and Enhanced Support.
* Terms and Conditions of Offer 1 and 2:
> Valid from 16th December 2019 to 29th February 2020.
> Valid for a three-year subscription of Sophos Intercept X Advanced only.
> In offer 2, the free XG appliance, Network Protection, and Enhanced Support are part of a one-year license. This license will commence simultaneously with the start of the Intercept X Advanced license.
> Not applicable for renewals.
> Valid for Hong Kong and Macau only.
> ACW Distribution reserves the right to change this offer at any time without notice.
http://www.acw-group.com.hk/acw_distribution/promotions/SO_201912EPE_UDS.html
For more details, please contact UDS Data Systems Ltd at (852) 2851 0271 or email to breadwong@udshk.com
2019.12.16 Demisto - a comprehensive Security Orchestration, Automation and Response (SOAR) Platform
 |
|
Demisto, a Palo Alto Networks company, is a comprehensive Security Orchestration, Automation and Response (SOAR) Platform that combines orchestration, incident management and interactive investigation to serve security teams across the incident lifecycle with a seamless experience. With Demisto, security teams can standardize processes, automate repeatable tasks and manage incidents across their security product stack to improve response time and analyst productivity. |
Demisto's orchestration engine automates security product tasks and weaves in human analyst tasks and workflows. Demisto Enterprise, powered by its machine learning technology, acquires knowledge from the real-life analyst interactions and past investigations to help SOC teams with analyst assignment suggestions, playbook enhancements, and best next steps for investigations. The platform (and you) get smarter with every analyst action. With Demisto, security teams build future-proof security operations to reduce MTTR, create consistent incident management processes, and increase analyst productivity.

KEY BENEFITS
1.Consistent, transparent, and documented processes
• Playbook-driven response actions and investigation queries.
• Auto-documentation of all investigations and historical searches.
• Automatic detection of duplicate investigations.
• Search across investigations, indicators, and evidence.
2.Quicker resolution times and better SOC efficiency
• Customizable playbook portfolio to automate redundant and repeatable steps.
• Virtual “War Room” for joint, real-time investigations.
• Granular tracking of incident and analyst metrics.
3.Improved analyst productivity and enhanced team learning
• Visual maps of related incidents for quick detection of duplicates.
• Real-time collaboration and unstructured investigation support.
• ML-powered insights for task-analyst matching, ownership, and response actions.
• Mobile application for on-the-go case management.
4.Flexible and scalable deployment
• Solution available as cloud-hosted or on premise deployment.
• Supports full multi-tenancy with data segregation and scalable architecture.
• Engine proxy to handle segmented networks.
• Multi-tier configurations for improved load management.
For further information about Dimasto, please contact Mr Bread Wong of UDS Data Systems Ltd (BreadWong@udshk.com, Tel +852 2851 0271) for details.
2019.12.02 Android 'spoofing' bug helps targets bank accounts
 |
The loophole was found when a security firm probed how bad apps stole cash.
A "major" security weakness in Google's Android software has let cyber-thieves craft apps that can steal banking logins, a security firm has found.
The bug lets attackers create fake login screens that can be inserted into legitimate apps to harvest data.
More than 60 financial institutions have been targeted by the technique, a survey of the Play store indicated.
Google said it had taken action to close the loophole and was keen to find out more about its origins.
"It targeted several banks in several countries and the malware successfully exploited end users to steal money," said Tom Hansen, chief technology officer of Norwegian mobile security firm Promon, which found the bug.
Lurking threat
The problem emerged after Promon analysed malicious apps that had been spotted draining bank accounts.
Called Strandhogg, the vulnerability can be used to trick users into thinking they are using a legitimate app but are actually clicking on an overlay created by the attackers.
"We'd never seen this behaviour before," said Mr Hansen.
"As the operating system gets more complex it's hard to keep track of all its interactions," he said. "This looks like the kind of thing that gets lost in that complexity."
Promon worked with US security firm Lookout to scan apps in Android's Play store to see if any were being abused via the Strandhogg bug.
They found that 60 separate financial institutions were being targeted via apps that sought to exploit the loophole. Lookout said it found criminals used variants of a well-known malicious money-stealing app known as bankbot.
In a statement, Google said: "We appreciate the researchers' work, and have suspended the potentially harmful apps they identified."
It added: "Additionally, we're continuing to investigate in order to improve Google Play Protect's ability to protect users against similar issues."
Promon's chief technology officer welcomed Google's response, as he said many other apps were potentially exploitable via the spoofing bug. But he noted that it still remained possible to create fake overlay screens in Android 10 and earlier versions of the operating system.
Source: https://www.bbc.com/news/technology-50605455
2019.08.06 UDS Supporting RTTP Training Program – Anti-Phishing Workshop
 |
 |
UDS support RTTP Training Program by launching Security Awareness Training – Anti Phishing Workshop. The objective of the workshop is to help candidates understand how phishing attacks work, the tactics that cyber criminals employ, how to spot and avoid a potential attack and most importantly you’ll be improve yourself and less vulnerable to phishing attacks.

Date: 12th Sep 2019
Time: 2:30pm – 5:30pm
Venue: Theatre 2, 1/F, HKPC Building, 78 Tat Chee Avenue, Kowloon Tong
Prerequisites: Bring your own smartphone/ Using Internet / email service experience
Suggested Course Fee: HK$1200/person(By applied RTTP training grant, HK$400/person ONLY)
Quiz will be provided as knowledge check that allows re-take if needed. Award of Certificate will be provided as kind of qualification to enlighten candidate career portfolio.
Click here for download workshop detail (pdf/216KB)
Training grant
Companies interested in applying for training grant for their employee(s) to attend registered public courses should submit the application via online system at least two weeks before course commencement. A list of registered public courses is available for reference. For tailor-made courses, companies should apply for course approval and training grants in one go.
Click here for FAQ of RTTP (pdf/19KB)
Click here for Training grant detail

好消息!
中國的註冊信息安全專業人员認證課程
Certified Information Security
Professional (CISP)及註冊信息系統審計師課程China
Certified Information System
Auditor(CISP-A)將會在8月底首次在香港及深圳舉行,透過再工業化
及科技培訓計劃(RTTP),UDS Data Systems Ltd 聯同
Cyber Range Training
Centre成功取得上述課程於香港政府RTTP計劃獲資助三分二的學費,原價港
幣24,000(包含考試費用),RTTP計劃資助港幣16,000,個
別課程實際學費為港幣8,000。UDS是這課程的代理。機會難逢,萬勿錯過!
甚麽是RTTP
Reindustrialisation and Technology
Training Program (RTTP)?
再工業化及科技培訓計劃 (RTTP)
是香港創新及科技基金下的一個資助計劃,以2:1的配對形式資助本地企業人員接受
高端科技與「工業4.0」有關的培訓。每間公司每一個財政年度的資助上限
為港幣五十萬元。Cyber Range Training
Centre於2019年的課程中設有兩個課程CISP-A和CISP並獲得
RTTP資助。
甚麽是注册信息安全專業人员 (CISP)及註冊信息系統審計師
(CISP-A)?
注册信息安全專業人员Certified Information
Security Professional
(CISP)為中國信息安全測評中心(CNTISEC)依據中國編辦批准開展“信
息安全人員培訓認證”之一,
其職能為實施信息安全專業人員的資質認定。CISP是國家對信息安全人員資質最高
認可。而CISP也可以說是國內版的CISSP認證。
註冊信息系統審計師China
Certified Information System Auditor
(CISP-A)
是由中國信息安全測評中心根據中央編辦授權,於2016年推出的國家註冊信息系統
審計師認證制度。信息系統審計是國家網絡空間安全保障戰略中的重要環節,是第三道
防線。將審計崗位和控制措施崗位獨立分開,是網絡安全策略中“職責分離”的重要要
求。國家註冊信息系統審計師的職責是執行審計以判斷信息系統控制措施的設計有效性
和執行有效性,並提供審計改進意見。持有信息系統審計師證書體現了證書持有者在信
息系統審計,安全與控制等方面的綜合實際能力。而CISP-A也可以說是國內版的
CISA認證。
為甚麼我們要需要這些認證?
隨著《中華人民共和國網絡安全法》的頒布實施,要求各相關機構定期對從業人員進行
網絡安全教育、技術培訓和技能考核”的義務。作為信息安全顧問或系統集成商,在國
內必須具備的是CISP和CISP-A。兩個認證都是由中國信息安全測評中心認
證,在國內安全行業與“一帶一路”的建設還是相對有很大優勢,尤其是乙方安
全從業者,項目投標首選證書,有一些中資機構在香港的辦事處或支部也
遵從國家的信息安全的標準,要求其從業員或供應商要具備CISP或CISP-A的
認證方可參與有關的資訊安全的項目。
為了配合各機構進行信息科技風險防範“三道防線”建
設,培養信息系統審計專業技術隊伍,提高信息系統審計人員執業能力,真正建立起
“關鍵信息基礎設施第三道防線”,中國信息安全測評中心自2017年開始,正式推
出“CISP-A註冊信息系統審計師”培訓考試制度,並於同年內推出了“信息系統
審計服務機構”資質認證制度。
中國信息安全測評中心(CNITSEC)是甚麼
機構?
中國信息安全測評中心是中國專門從事信息技術安全測試和風險評估的權威智能機構。
對信息安全專業人員的資質能力進行考核,評估和認定。信息安全人員測評與資質認
定,主要包括註冊信息安全專業人員(CISP), 及註冊信息系統審計師
(CISP-A), 信息安全意識培訓。
認證對象:國家信息安全測評機構、信息安全諮詢服務機構、社會各組
織、團體、企事業單位中從事信息安全服務或高級安全管理工作的人員、企業信息安全
主管、信息安全服務提供商、IT或安全顧問人員、IT審計人員、信息安全類講師或
培訓人員、信息安全事件調查人員、其他從事與信息安全相關工作的人員(如系統管理
員、程序員等)。
講師簡介
CISP:张老师:信息安全領域資深高級講師/諮詢顧
問, 中國信息安全測評中心授權CISI講師.
為山西太原軟件協會、雲浮教育局、廣東藥監局、廣東省財政廳、南沙檢察院、深圳市
政府、深圳市網絡中心、深圳市科委、深圳信息技術學院、深圳農商銀行、東
莞電力、華南師範大學、廣州開放大學、北京師範大學珠海分校、第一創業證券、寶盈
基金、鼎和財保、國投瑞銀等多家企業、學校的信息安全管理理念、信息安全管理體
系、風險管理、信息安全意識宣貫培訓、網絡安全法解讀、業務連續性管理(BCM)
等課程設計、教材編寫和課程主講等工作。
CISP-A:廖老師:信息安全專業人員,副教授,北
京航空航天大學博士,中國信息安全測評中心特約講師,為中國人民銀行、交通部、國
家稅務總局、教育部、中國石化集團公司、國家電網公司、國家機關工委、中軟集團等
國家政府機構、大學國有企業提供各類安全諮詢服務和培訓項目。作為高級信息安全顧
問,主要負責諮詢信息安全類服務項目規劃、審計評估項目組織和執行、登記保護和信
息技術服務體系建設等。
授課語言
普通話,教材為簡體中文字。
註冊要求
1.
教育與工作經歷:碩士或研究生以上,具有1年工作經歷:或本科畢業,具有2年工作
經歷:或大專畢業,具有4年工作經歷。
2. 專業工作經歷:至少具備1年從事信息安全有關的工作經歷。
3.
培訓資格:在申請註冊前,成功地完成了CNITSEC或其授權培訓機構組織的註冊
信息安全專業人員培訓課程相應資質所需的分類課程,並取得培訓合格證書。
4.通過有CNITSEC舉行的註冊信息安全專業人員考試。
CISP考试模式
CISP及CISP-A考试题型為單選選擇題共100题,每题1分,得到70分或
以上為通過, 時間為三個小時。
培訓日程安排及教學內容(CISP)
|
序 |
日期 |
時間 |
課程 |
地點 |
|
1 |
2019年8月31日 |
09:00-12:00 14:00-18:00 |
信息安全保障 網絡安全監管 |
香港 |
|
2 |
2019年9月1日 |
0900-12:00 14:00-18:00 |
信息安全管理 信息·安全支撐技術 |
|
|
3 |
2019年9月7日 |
09:00-12:00 14:00-18:00 |
業務連續性 安全评估 |
|
|
4 |
2019年9月8日 |
09:00-12:00 14:00-18:00 |
安全工程與運營 軟件安全開發 |
|
|
5 |
2019年9月14日 |
09:00-12:00 14:00-18:00 |
計算環境安全 物理環境與網絡通信安全(模擬考試,所有考試務必出席) |
深圳南山 |
|
6 |
2019年9月16日 |
09:30-11:30 |
考試 |
深圳南山 |
|
序 |
日期 |
時間 |
課程 |
地點 |
|
1 |
2019年8月31日 |
09:00-12:00 14:00-18:00 |
信息安全管理基礎與管
理體系 信息安全風險管理 |
香港 |
|
2 |
2019年9月1日 |
0900-12:00 14:00-18:00 |
密碼學基礎 安全漏洞與惡意代碼基
礎 |
|
|
3 |
2019年9月7日 |
09:00-12:00 14:00-18:00 |
信息系統審計基礎 信息系統審計方法 |
|
|
4 |
2019年9月8日 |
09:00-12:00 14:00-18:00 |
信息系統審計實務 信息系統安全審計實務 |
|
|
5 |
2019年9月14日 |
09:00-12:00 14:00-18:00 |
信息系統審計案例(模擬考試,務必出席) |
深圳南山 |
|
6 |
2019年9月16日 |
09:30-11:30 |
考試 |
深圳南山 |
證書
由中國信息安全測評中心發出之認證
|
注册信息安全專業人员Certified
Information
Security Professional(CISP) |
註冊信息系統
審計師China
Certified
Information System
Auditor(CISP-A) |
 |
 |
請致電 2565-4638 或發電郵到 sales@cyberrange.hk
網站: https://www.cyberrange.hk/
2019.07.08 Is Your SOC Team Ready for a Cyberattack?
Eventually, your organization will be attacked.
Unfortunately, this will be the first time your SOC team will experience this attack.
Cyberbit Range prepares your security team for the attack, by providing a hyper-realistic, virtual SOC environment, in which they can train in responding to real-world, simulated cyberattacks, and dramatically improve their performance.
Enterprise Prepare your SOC team and red team with a wide range of simulated training scenarios, from entry level individual training to advanced, multi-stage attacks and team training. |
|
Higher Education Become the regional cyber hub. Increase student enrollment and retention and prepare your graduates for a career in cybersecurity with hands-on cyber range simulation labs. |
|
Service Providers and MSSPs Expand and differentiate your portfolio and increase revenues, by setting up a Cyber Security Training and simulation center and offering advanced training services. |
|
Public Sector Solve the cybersecurity skill gap by accelerating the certification of cybersecurity professionals. Train incident response teams in simulated cyber attacks. Test your IT infrastructure and security measures in a safe and controlled environment. |
Call UDS Data Systems Ltd for a Cyber Range Course Test Drive or product demonstration at 2851 0281 or email to info@udshk.com




Secure Code Warrior is a global security company that makes software development better and more secure. As stated at the outset, the time has come to evolve developer software security training and tools, so they become a constant and positive part of their everyday working routine. Writing great software means it must be secure.
Developers need to take more responsibility for security, and a significant opportunity exists for companies to build a strategic business advantage by encouraging this kind of approach. The solution not only involves building skills, but also having the right toolset to help every step of the process, from the first line of code until the last and beyond.
An innovative approach empowered by modern training and tools that we know work in alliance to improve developer security. The powerful combination of Secure Code Warrior’s training platform and the Sensei IDE plugin will assist security and development teams to collaborate constructively in building a positive security.
2019.05.24 SafeGuard LAN Crypt goes conpal – stay well protected and up-to-date
Dear LAN Crypt customer,
SafeGuard LAN Crypt is a first-class, high-performance Data Encryption Solution – today and of course in future. Your data deserves seamless protection. That is why we at conpal GmbH are delighted to continue the development of LAN Crypt for you.
We are using our extensive know-how and long term experience in the development of IT security solutions in order to ensure a smooth transition. Following, you will find the most important information with respect to the transfer of LAN Crypt.
What’s the current situation?
In July last year, Sophos has transferred the rights of SafeGuard LAN Crypt to us.You have been informed by Sophos in October 2018. At the beginning of 2019, we have received permission for the transfer from the relevant authorities (in accordance with § 57 of the German Foreign Trades and Payments Regulation). At present, we are preparing the release of the first conpal LAN Crypt Version.
What’s the next step?
We are making our "Upgrade Release" available for all customers with an active support agreement for SafeGuard LAN Crypt. The "Upgrade Release" is the first conpal version of LAN Crypt - and free for all customers with a valid maintenance contract. The "Upgrade Release" serves as the basis for all future LAN Crypt Versions released by conpal and as such builds the foundation for further development and support.
What are the system requirements for the "Upgrade Release"?
The "Upgrade Release" will be released as conpal LAN Crypt 3.97. The Version will provide an upgrade on the last Version of SafeGuard LAN Crypt Client 3.95.3, released by Sophos. In addition, the "Upgrade Release" supports the current Windows 10 Release 1809 and forms the basis for future upgrades, updates and bugfixes.
What changes regarding your administration?
Nothing, as the upgrade is primarily impacting the client. The backend infrastructure can be largely maintained. We will ensure that your existing policy settings will remain unchanged during the transition, as the Upgrade will be compatible with the current SafeGuard LAN Crypt Admin 3.90-Version.
What should you do now?
We are realizing a smooth transition in order to achieve a seamless protection of your data. To get access to the "Upgrade Release", please register at our LAN Crypt Landing Page.
From Device Security, via authentication to encryption: Our broad expertise grants a sustainable protection of our customer’s data. For this reason we will continue to develop LAN Crypt now and in future aligned on your current needs – trust in it.
Do you have questions?
Further information about the "Upgrade Release" can be found on our LAN Crypt Page.
"conpal LAN Crypt encrypts your data in an reliable and trustworthy way. We will continue to develop this powerful IT security solution to make it well prepared for the challenges of the future. With our extensive Know-how and our vast experience, we make sure that you retain complete control of who accesses your sensitive information."
Rolf Wassermann und Ralf Engers, founders and managing directors of conpal
"We are delighted that conpal is ready to release their inaugural version of conpal LAN Crypt that will continue to provide our mutual customers with great protection for their confidential information for a long time to come. As we transition existing Sophos SafeGuard LAN Crypt customers to conpal, it is of the outmost importance to us that we make sure that our customers have a smooth journey to get there and we are convinced that conpal will be a great partner for everybody going forward."
Petter Nordwall, Director of Product Management, Sophos
For the new conpal LAN Crypt price , upgrade maintenance and new deployment information, please contact Mr Bread Wong of UDS Data Systems Ltd (BreadWong@udshk.com, Tel +852 2851 0271) for details.
2019.04.09 Cyberbit Range for Computer Science Programs Case Study: Ariel University

The Need for Hands-On Academic Computer Science Programs
STEM education is evolving. With the increased demand for qualified graduates in technology and engineering roles, students expect more from their academic degree programs, while educators are more focused than ever on preparing their STEM students for their careers. This evolution calls for an increasingly hands-on approach in computer science, IT, and engineering programs. Ariel University in Israel is one of the first higher education institutions to integrate hands-on cyber range sessions into their computer science and cybersecurity degree programs, starting with undergraduate courses. This approach significantly impacted the program’s success, quality and appeal. Ariel University chose to use Cyberbit Range to run the programs.
About Cyberbit Range
Cyberbit Range is a simulation platform, originally developed for training blue and red cybersecurity teams in military organizations. Since its launch in 2013 Cyberbit Range has become the world leading simulation platform for hands-on academic degree programs in cybersecurity and computer science. In addition to Ariel University the platform is used by Regent University, Miami Dade College, Metropolitan State University, The University of Maine, and additional education institutions worldwide.
Computer Science and Cybersecurity Curriculum Leveraging Cyberbit Range
|
|
• Networking basics |
2018.09.24
跨行業安全資訊共享平台 Cybersec
Infohub啟動,聯合數據系統有限公司 (UDS)
為Cybersec Infohub成員
政府資訊科技總監辦公室(資科辦)正式啟動為期兩年的網
絡安全資訊共享夥伴試驗計劃Cybersec
Infohub,並推出全港首
個跨行業的網絡安全資訊共享協作平台,
以促進公私營機構及社區交流網絡安全資訊,提升香港整體應對網絡攻擊的防
衞及復原能力。
政府資訊科技總監林偉喬在啟動儀式
上說:「現時網絡攻擊每分每秒都在發生,網絡威脅花樣繁多。任何企業或機構單憑一
己之力應付千變萬化的網絡威脅,實在非常困難。因此,我們需要建立互信及
緊密的協作關係,共享網絡安全資訊。」 Cybersec Infohub由資
科辦管理,並獲創新及科技局的科技統籌(整體撥款)資助進行。
凡在香港有營業地址、須管理電子通
訊網絡和對網絡安全資訊有運作需要的公司及機構,不論規模大小,均可免費成為Cybersec
Infohub的成員。聯合數據系統有限公司
(UDS) 已登記為Cybersec Infohub的成
員。
 |
政府
資訊科技總監林偉喬(手持標誌)與一眾支持機構大合照。
通過Cybersec Infohub設立的協作平台(Cybersechub.hk),
成員可與不同行業的網絡安全專家共享網絡安全資訊、建議及專家見解,例如緩解措施
和良好作業模式等。而公眾也可以瀏覽平台的公眾區域,從而獲取這些專業資
訊,形成一個多向的資訊交流平台。協作平台另一個作用是促進成員之間的協作,成員
通過盡早分享最新的網絡威脅及攻擊情報,除發揮預警作用外,還可藉着互相協作更有
效地防禦網絡攻擊。
在保
安方面,平台除了嚴格遵守政府的保安政策及指引外,也會採用雙重驗證的登入方式,
以及業界在共享網絡安全資訊方面的標準。這些措施為成員提供可信賴的環境,讓他們
在專區內安全地分享資訊及情報、進行討論或與其他專家協作。此外,成員亦可從協作
平台蒐集並導出入侵指標至其營運系統,以便應用或作進一步的安全分析。
林偉
喬表示,世界各地已成立不少共享網絡安全資訊的組織,通過交流情報、知識及經驗,
令成員能在網絡威脅或攻擊初起時及時回應。他期望通過Cybersec Infohub,本港也能建立行業之間的協作文化和更緊密的夥伴關
係,從而更有效和迅速地應對網絡攻擊。
已獲81間公司登記
現時,來自81間公司和機構的229名代表已登記為 Cybersec Infohub的成
員 (包括 UDS),當中不少已率先在平台上分享不同類型的資訊,包括最
新的網絡威脅趨勢、勒索軟件的研析報告、漏洞的保安建議等。參與的公司和
機構包括網絡保安公
司、大專院校、關鍵基礎設施營運商、資訊科技業界專業協會、電訊或互聯網服務供應
商、金融及保險業機構,以及本地兩個電腦保安事故協調中心等。
林偉喬說,協作平台於明年上半年會注入人工智能元素,
使用機器學習構建和操作文本分析模型,協助成員就網絡安全資訊進行整合和分析,方
便專家更便捷地取得所需資訊和更及時地向公眾發布。
2018.09.19 Cyberbit Partners
with Cyber Range Training
Centre (CRTC) to Open First
Cybersecurity Simulator in
Hong Kong
Cyberbit Range will
provide hands-on simulations of real
cyberattack scenarios to train
professionals and organizations how
to defend against them in real time.
 |
 |
Cyberbit
Ltd.,
a world leading provider of
cybersecurity simulation and IT/OT
detection and response platforms, and
Cyber
Range Training Centre (CRTC) Ltd.,
have
collaborated to open the first IT
security defense training centre
equipped with the latest simulation
training technology in Hong Kong.
“IT
security
threats are increasingly becoming a
major risk to business and technology
alone is not sufficient to protect
organizations against these threats,”
says Joseph Yang, CEO, CRTC. “Whether
security teams are in-house or
outsourced to a managed security
service provider, it is important to
perform joint drills in a realistic
setting so that all teams can respond
in a coordinated manner when under
attack.”
The
new
CRTC is powered by the Cyberbit Range
platform and is being launched in
collaboration with the Hong Kong
Productivity Council. The Centre will
offer hyper-realistic professional
training programs instructed by elite
cybersecurity experts to enterprises
and individuals, and certifications
including CISA, CISM, CEH and ISSE.
“CRTC
will
provide a vital component of strong
cybersecurity to the Hong Kong market
- well-trained, experienced
professionals,” says Adi Dar, CEO,
Cyberbit. “Innovative simulation
and training is the best way to ensure
the highest level of cyber security to
businesses.”

To
learn
more about Cyberbit’s Cyber Range
platform and CRTC in Hong Kong, please
email to Bread
Wong
for more details.
Cyberbit Range is
the most widely deployed cybersecurity
training and simulation platform for
higher education, service providers,
governments and enterprises. The
platform has already been selected by
numerous cyber training facilities in
the US, Europe, Asia and Australia,
with dozens of classrooms operating
around the world and new training
centers continuously being launched.
In addition to simulating large-scale
virtual networks and attacks based on
real-world incidents, the platform can
also pinpoint system vulnerabilities
and help users develop countermeasures
and improved protocols for dealing
with cyber-attacks on critical network
systems. As a result, cybersecurity
practitioners benefit from receiving
real-time training for threat
detection and the response process,
enabling them to dramatically improve
the performance of all security and
SOC teams.
2018.08.0 1 UDS carries Kemp Products

Kemp Technologies, Inc. was founded in 2000 in Bethpage, New York and operates in the application delivery controller industry.[2] The company builds load balancing products which balances user traffic between multiple application servers in a physical, virtual or cloud environment.
Kemp product including the following products
1. Load Balancer - providing High Availability and Geo Load Balancing. It supports Virtual LoadMaster on Hypervisor such as VMware, Hyper-V, Xen, KVM and Virtual LoadMaster on cloud such as Microsoft Azure, AWS and VMWare vCloud Air.
2. Security - Web Application Firewall
2018.07.01 Range products Regent University
Cyberbit Ltd., a world-leading provider of cybersecurity simulation and IT/OT detection and response platforms, and Cyber Range Training Centre (CRTC) Ltd., have collaborated to open the first IT security defense training centre equipped with the latest simulation training technology in Hong Kong. www.cyberrange.hk
Regent University also conducts Cyberbit Range training to National Security Agency of United States of America (NSA) and U.S. Department of Homeland Security (DHS).

On Tuesday, 2017 October 3, Regent University took a cutting-edge leap into training students to secure those breaches as it launched its Cyber Range training center in partnership with Cyberbit Ltd., the leading provider of cybersecurity products enabling detection, response and training across IT and Operational Technology (OT) systems.
The world-class facility will provide hands-on cybersecurity training and simulation platforms with real-time attack scenarios and security breaches for Regent students seeking to fill the projected 6 million job openings in the cybersecurity field by 2019.
The Cyber Range will also serve as a training center for local businesses, government and military organizations, and features customizable capabilities to meet every industry’s data protection needs.
It’s among the first of its kind to launch in the United States at a private university.
"This facility is going to be available to train military leaders, business leaders and especially the students of Regent University in cutting-edge technology," said Regent Founder, Chancellor and CEO Dr. M.G. "Pat" Robertson to guests attending the Cyber Range’s ribbon-cutting and dedication ceremony. "We want to be leaders, and Regent University has been a leader. And I hope that those of you here in the Virginia Beach community realize how important this Cyber Range is going to be."
Robertson estimated 1 trillion dollars-worth of damage done by cybercriminals hacking into corporations. He explained that the Cyber Range will give real-world experience to executive and students alike on how to handle cyberattacks.
And according to Cyberbit CEO, Adi Dar, the most effective way to master a new skill is through simulation training.
"We are proud to partner with Regent University in their pioneering effort to advance the state of cybersecurity by developing a highly skilled workforce that can detect advanced threats and respond effectively to any kind of cyber incident across IT and OT networks," said Dar. "There is no doubt in my mind that it has tremendous potential. I would like to congratulate the university on this special day and thank Dr. Robertson for the opportunity to be a part of this vision."
Following the ribbon-cutting ceremony, Regent’s Office of Alumni Relations & Special Events hosted a luncheon event. Former United States Attorney General John Ashcroft said he’s honored as he completes his thirteenth year at Regent, sharing the privilege of preparing the next generation of Christian leaders.
"Here, no pursuit of truth – intellectual or spiritual – is off-limits, and the truth, and an understanding of it, is the greatest defense we can have," said Ashcroft. "As a result, both Americans individually and America as a defender of global liberty, are stronger, and I’m grateful to have this opportunity and for your involvement and your support of this project."
Continuing to lead the way in training cybersecurity experts, Regent University will host its inaugural Cyber Summit, featuring reformed hacker and security consultant to Fortune 500 companies and global governments, Kevin Mitnick, in February 2018.
2018.06.28 UDS new win for Drivelock case

Happy to share this nice new win. As always, the business case is very interesting:
Company Name: China Branch of a famous Germany car manufacturer
Use Case: Device Control
Number of Agents being deployed: Over 7,000
The Challenge/Solution: There were many legacy Windows systems distributed in several production plants.
Note: Drivelock can be tailor-made as a tool to help companies protect from malwares, i.e., ransomwares as well as to fulfill GDPR requirements. Please feel free to contact Bread Wong ( breadwong@udshk.com ) for more information.
2018.04.26
UDS carries Next
Generation Deep Learning End
Point - Deep instinct
Deep learning is the most advanced subset of artificial intelligence. Also known as “deep neural networks,” it takes inspiration from how the human brain works.
Namely, the more data that is fed to the machine the better it is at intuitively understanding the meaning of new data – and, therefore, does not require a (human) expert to help it understand the significance of new input.
About Deep Instinct
Deep Instinct is the first company to apply deep learning to cybersecurity. Harnessing the power of deep learning’s predictive capabilities in order to create the ultimate cyber security solution: On- device, proactive solution that protects against zero-day threats and APT attacks with unmatched accuracy.

By using advanced methodologies and deep learning, Deep Instinct protects its customers from executable-less attacks, dual-use and code-injection attack.
Advanced heuristics, which also protect against file-based attacks, quickly prevent code-injection and in-memory attacks. And finally, Deep Instinct’s unique deep learning model protects against dual-use tools utilized in living-off-the-land attacks, and against dropper files used in non-PE attacks, blocking these attacks pre-execution.
Deep Instinct do NOT need
- Signature
- Sandboxing for detection
- Traditional Machine Learning


CA Veracode, Inc., a leader in securing the world’s software, and acquired by CA Technologies (CA), today announced it has been positioned in the Leaders quadrant for the fifth consecutive time of Gartner Inc.’s 2018 “Magic Quadrant for Application Security Testing1.” In our view, CA Technologies (CA Veracode)’s position in the Leaders quadrant is a result of the company’s completeness of vision and ability to execute in the application security testing (AST) market.
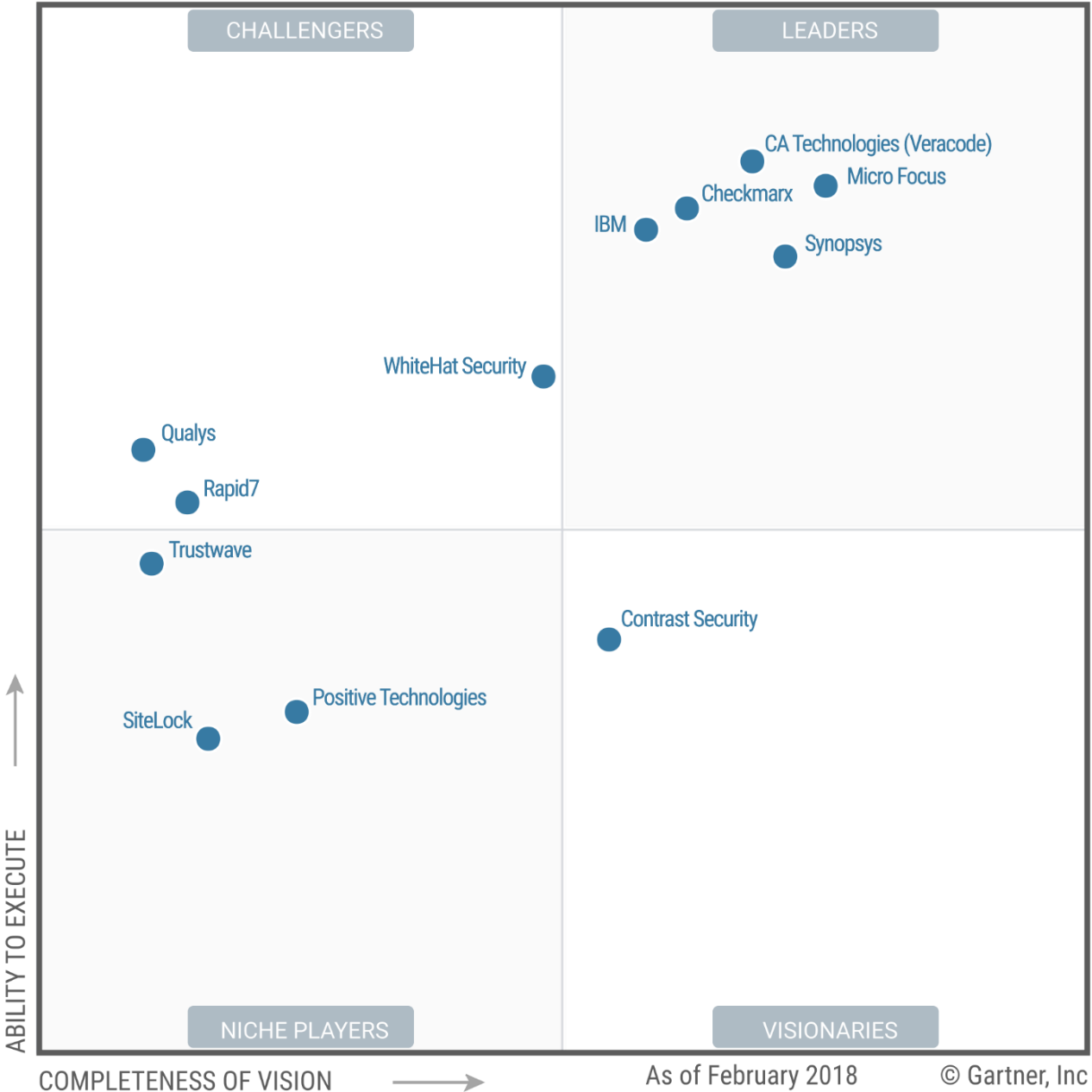
With broad language and framework coverage, the CA Veracode Application Security Platform offers a holistic, scalable way to manage security risk across your entire application portfolio. With a wide range of security testing and threat mitigation techniques, as well as support from our security program managers, organizations are given the keys to creating a strategic, repeatable way to tackle application security risk. It features integration into Software Development Life Cycle (SDLC) processes with built-in integrations with multiple IDEs, bug-tracking systems and build servers, as well as APIs for integration, CA Veracode Greenlight and Developer Sandbox.
To learn more about CA Veracode’s Application Security Platform, please visit: http://www.veracode.com/products/application-security-platform
For further information about CA Veracode, please contact Bread Wong.
Note:
1 Gartner, Inc. 2018 “Magic Quadrant for Application Security Testing” by Ayal Tirosh, Dionisio Zumerle and Mark Horvath. March 19, 2018
Cyberbit's SOC 3D is a SecOps force multiplier, increasing SOC efficiency and reducing Mean Time To Respond (MTTR) with the first SOAR platform combining security orchestration, automation, and big-data driven investigation, enabling incident responders to manage the entire incident lifecycle within a single screen, from detection to recover.
SOC 3D is the first Security Automation and Orchestration (SOAR) platform combining automation, orchestration, and big-data powered investigation into a single and comprehensive incident response platform that triples SOC efficiency, provides unprecedented visibility and reduces time-to-respond by 90%.
 |
Accelerate
Response Reduce MTTR (Mean Time To Respond) by up to 90%, and free your analysts to recapture high-priority incidents by automating manual tasks like collecting threat intelligence, sending emails, and more. |
 |
Reduce
Escalations Empower tier-1 analysts by centralizing IR management, automating manual tasks and simplifying investigations. Reduce escalations by 50% to allow tier-2 and 3 analysts to focus on critical incidents. |
 |
Investigate
Efficiently SOC 3D is a big-data platform providing visibility into all raw data, so your analysts can get any question answered, fast, and create any investigation dashboard they need, in real-time. |
 |
Focus on What's
Important Focus your incident response team on business-critical alerts with automated prioritization by business impact, ensuring that high-priority threats are managed first - always. |

Toby Musser, CEO, MNS Group (MSSP)

UDS Data Systems Limited has been accepted into the 2018 Gemalto Cipher Partner Program at the Platinum level effectively on February 1 of 2018. UDS's membership in the Gemalto Cipher Partner Program gives usaccess to exclusive benefits and resources and validates that UDS Data Systems Limited is authorized to re-sell our hardware and software products, including, authentication, encryption, and maintenance.
Introducing SafeNet Luna HSM 7.1
This 7.1 release for SafeNet Luna Network and Luna PCIe HSMs includes:
Flexible partition policies on each partition that match the use case
| • | Keys in hardware as a default, providing the strongest key security for critical use cases including PKI, Code Signing, and Blockchain |
| • | Exporting private keys to be embedded in devices for secure manufacturing, IoT, smart metering, and more |
| • | HSM and Partition Policy Templates |
| • | Ability to set consistent policies for HSMs and partitions |
| • | Support for AIX and Solaris |
The new EU General Data Protection Regulation (GDPR) represents the most significant change in global privacy law in 20 years. It introduces new and wide ranging privacy requirements for any organization handling the personal data of individuals living in the EU. The GDPR will broaden and add requirements to its predecessor, the EU Data Protection Directive or DPD, and because it is a regulation, not a directive, it will have binding legal force throughout every member state.
The GDPR was adopted in April 2016 and goes into effect on May 25, 2018. Given the complexity and detailed requirements of the regulation, organizations need to begin now to plan, budget, and implement the process and technology changes needed to meet regulatory guidelines.
What Does the GDPR Mean for Compliance and Security Professionals?
As those who have studied the details of the GDPR know, the regulation is a legal framework that does not specify many technical details as far as how to achieve compliance. However, it does clearly spell out a new set of data protection principles and procedures that must be followed.
In order to get started with GDPR requirements, organizations need to have a clear understanding of how they process, store and secure personal data. Once the organization has catalogued all personal data used for processing, it must ensure that this data is adequately secured. The GDPR mandates that "appropriate technical and organizational measures" be put in place to protect data, and it requires documentation that demonstrates this compliance. Lastly, the GDPR requires organizations to monitor and detect any breaches of personal data that occur and to notify authorities and in some cases data subjects when a breach occurs.
Identity management gives you the power to securely and confidently grow your company, enter new geographies, collaborate globally and focus on innovation.
SailPoint gives you the power of identity so you can move your business forward.
 |
Secure
the
Cloud Enterprise We are all moving to the cloud, and it changes our security footprint. |
 |
Prevent
Data
Breaches It's your new reality. Don't let breaches distract you from your business. |
 |
Collaborate
without
Boundaries Unstructured data is growing exponentially each year. Embrace it, secure it. |
 |
Operate
Internationally Global world. Global workforce. Global business. That means global regulations. |
 |
Keep
Your
Competitive Advantage Balance business enablement and security to confidently focus on your business. |
The leading insider threat management solution provider with approximately 1,700 customers around the world, today announced its third consecutive record-breaking quarter, driven by customers' need to decrease risks through advanced insider threat detection and prevention.
ObserveIT regularly releases new
product updates to meet evolving
customer needs and deliver a
cutting-edge solution with best-of-breed
capabilities. In Q4, ObserveIT added key
new features and enhancements to the
platform, including File Activity
Monitoring and Enhanced Alert Workflow.
Additional milestones achieved in 2017
include:
• Achieved more than
60+ percent year-over-year bookings
growth.
• Saw Net Promoter
Score increase to the mid-70's,
reflecting deep customer loyalty,
continued confidence and strong overall
support.
• Grew customer base
to approximately 1,700.
• Secured significant
customer wins, with a record-breaking
500 percent increase in the total number
of six-figure deals in Q4.
• Continued employee
growth, with a more than 20 percent
increase from the end of 2016.
About ObserveIT:
![]()
ObserveIT is the leading Insider Threat
Management solution with approximately
1,700 customers across 87 countries.
ObserveIT is the only solution that
empowers security teams to detect
insider threats, streamline the
investigation process, and prevent data
exfiltration. With 230+ out-of-the-box
insider threat alerts, rich metadata and
outstanding search capability and
playback of any policy violation,
ObserveIT provides comprehensive
visibility into what people -
contractors, privileged users and
high-risk users - are doing, and reduces
investigation time from days to minutes.
For a free demo, please contact Bread
Wong at (852) 28510271.
2017.7.19 Bangcle is one of the selected vendors in Gartner 2017 Market Guide for Application Shielding
ObserveIT sees 100% percent year-over-year growth fuelled by record bookings in Q2, Net Promoter Score surges past 70, wins "Best Place to Work" award, and has fastest adoption in history for newest version of product to help companies eliminate Insider Threats.
Milestones achieved in Q2 2017 by ObserveIT include:
| • | 100 percent year-over-year growth in bookings (Q2 2017 v Q2 2016) |
| • | Record bookings in Q2 2107, fuelled by a $1.4 million deal with one of the largest asset management firms in the world and the highest number of $100K-plus deals in a single quarter in company history |
| • | Net Promoter Score increased to greater than 70, reflecting deep customer loyalty and satisfaction |
| • | Signed more than 50 new customers in Q2 2017, increasing its customer base to 1,557 organizations worldwide. ObserveIT now has 5 of the top 10 financial services companies, 3 of the top 5 banking institutions, and 2 of the top 5 asset management firms as customers. |
| • | Fastest adoption of a new product version (ObserveIT 7.0 released in April) in company history |
Other achievements in Q2 2017
include:
| • • | In June, the Boston
Business Journal (BBJ) named
ObserveIT to its exclusive 2017
list of Best Places to Work. In April, the company released ObserveIT 7.0 to accelerate insider threat detection and prevention with new actionable analytics and user activity profiling to thwart threats from within. |
ObserveIT product highlights:

Interesting? Please contact Bread Wong at (852) 28510271 for more information.
2017.5.24
Splunk
- Weapon of a Security
Warrior


Are you well prepared for fighting
against the next Ransomware attack?
No matter you are being impacted by
WannaCry or not, we all know that hacker
will not stop because ransomware give
them real business, and there may be
even more attacks in the future. Splunk
has been a thought leader in providing
solutions for detection and prevention
of ransomware-type malware for a couple
of years. In response to this recent
attack, we would like to invite you to
join our webinar, which will cover:
• Splunk’s finding on WannaCry and
how to use Splunk to detect WannaCry.
• How to protect yourself from
the next ransomware attack.
2017.5.15
WannaCryptor Ransomware 3
Actions You Should Take
Immediately

WannaCryptor Ransomware hit over 40 UK
hospitals, as well as over 75,000
additional workstations in 99 countries
as of today, in what is turning to be
the most massive ransomware campaign to
date.
The ransomware, also referred to as
WannaCry and Wana Decrypt0r, is
delivered as a Trojan, which is
downloaded when the user mistakenly
clicks on a hyperlink delivered in a
phishing email, Dropbox link or banner.
Once the ransomware payload is executed,
it encrypts files on the user’s hard
drive, deletes the originals and
displays the following message,
requesting the user to pay a ransom in
order to decrypt and recover the files.
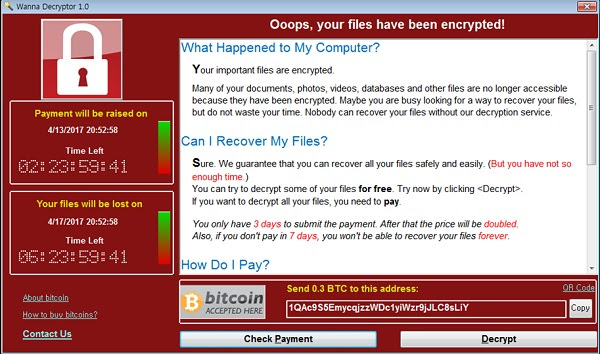
Why is WannaCryptor ransomware
spreading so quickly?
As initially reported by the Spanish
CERT, and confirmed by Cyberbit
researchers, the attack utilizes a
Windows XP vulnerability: EternalBlue/MS17-010/SMB
to spread laterally. This means that
after attacking one computer in the
organization, the ransomware can spread
independently within the network and
attack additional workstations. An
interesting fact is that this exploit
was developed by the NSA and leaked by
Shadow Brokers hacker group. Although
these vulnerabilities were patched by
Microsoft in March, large corporates,
particularly hospitals, often lag behind
in patching and therefore many of the
workstations were left vulnerable,
allowing the attack to spread.
What should your organization do now?
1. Patch Windows XP machines
immediately – while this will not
prevent the initial infection it will
prevent the ransomware from spreading
laterally and substantially slow it down
2. Re-enforce security awareness best
practices – East Kent Hospitals
Tweeted all staff and warned them from
opening the phishing email labeled
‘Clinical results’. Update your
employees on best practices and warn
them about the risk of opening
unexpected emails from untrusted or
sources
Wannacryptor Ransomware
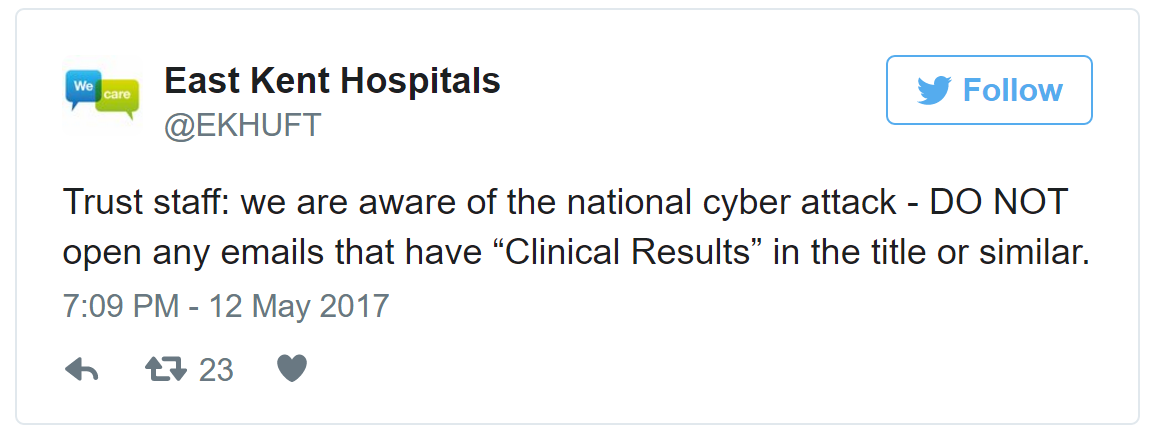
3. Deploy an Endpoint Detection and
Response Product with anti-ransomware
– only 30% of antivirus software can
identify and block WannaCryptor
ransomware, as reported by the
Mirror. It is essential to
complement antivirus with an endpoint
detection and response product that
protects against advanced malware that
bypasses traditional AV. This solution
should include inherent anti-ransomware
capabilities to block.
Cyberbit EDR anti-ransomware
Cyberbit’s
Endpoint
Detection and Response (EDR)
provides ransomware detection and
prevention that helps organizations
detect and block ransomware attacks like
WannaCryptor in real-time before
critical files were encrypted. Cyberbit
EDR identifies behavioral
characteristics that indicate an attack,
and as a result it detects threats that
often bypass antivirus solutions.
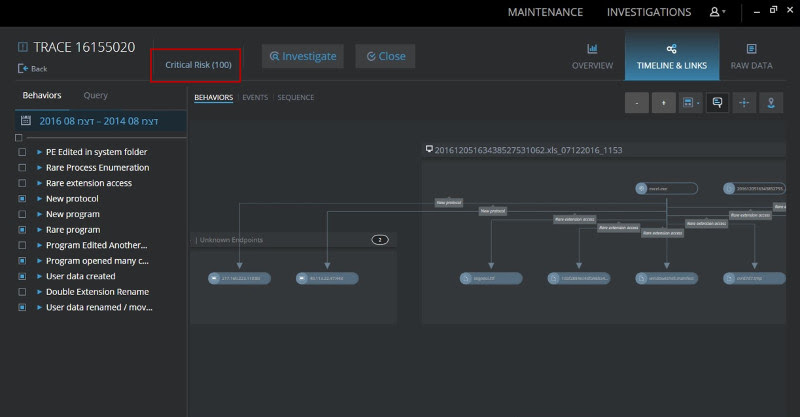
Cyberbit EDR graph view – identifying
ransomware infection
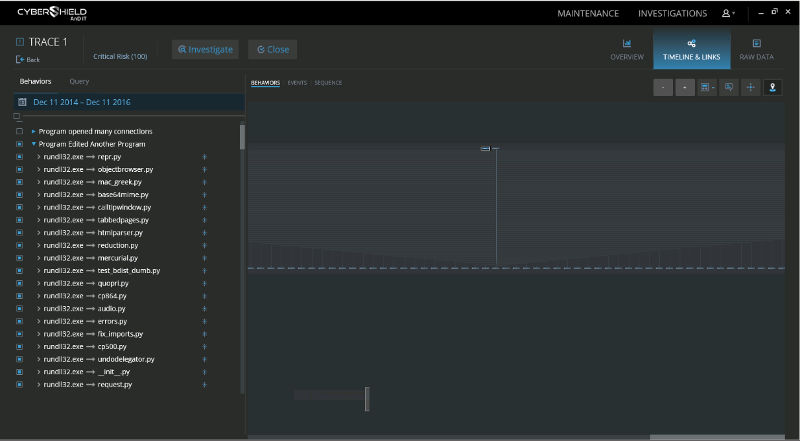
Cyberbit EDR – Identifying
ransomware encryption behavior
Read the Cyberbit blog for recent ransomware
detection
success story in a large
enterprise and visit the Cyberbit
website for more info and a demo
Tal Morgenstern is Head of R&D,
Endpoint Detection and Response Team at
Cyberbit.
Please feel free to contact us for more
information.
2017.5.15 Defend
against WannaCry/Wcry
Ransomware
Due to the WannaCry/WCRY Ransomware
attack around 150 counties, we need to
notify how our security product to
against this attack. The following
is the information for protect your
origination.
![]()
For the Forigatet product:
Update the IPS signature and anti-virus
signature
http://blog.fortinet.com/2017/05/12/protecting-your-organization-from-the-wcry-ransomware

For TippingPoint product:
Login to the TMC account
https://tmc.tippingpoint.com/
The filters in the CSW are
designed to detect the propagation of
the malware known as WannaCry/WCRY by
looking for the malware binary download.

For Sophos UTM:
Active the Advanced Threat Protection in
the firewall
https://community.sophos.com/products/unified-threat-management/f/network-protection-firewall-nat-qos-ips/91927/utm-advanced-threat-protection-blocks-kill-switch-url-for-wannacry-also-referenced-as-wcry-wannacrypt-and-wanacrypt0r

For Sophos Intercept X:
https://community.sophos.com/products/intercept/f/information/91942/intercept-x-releasing-any-new-updates-for-wannacry-ransomware/332939

For Lumension:
Apply the latest Windows Patch MS17-010
for all Windows computers by Lumension
https://www.lumension.com/vulnerability-management/patch-management-software.aspx

For Splunk:
Steering Clear of the "WannaCry" or
"Wanna Decryptor" Ransomware Attack
https://www.splunk.com/blog/20

On the 2nd Phase of the Infection
Chain, the mssecscr.exe will call back
to C&C for the key and OpenDNS will
terminate the connection between victim
the C&C. This will prevent the
exploit of the Wannacry
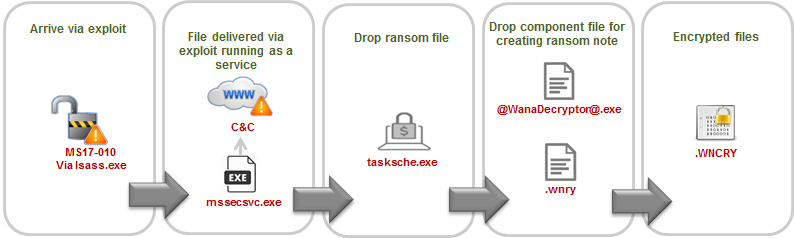
For questions or technical assistance,
please contact Bread
Wong or (852) 28510271 (Office).
2017.4.26
Cyberbit EDR Adv
Cybersecurity with Adaptive,
Automated Capabilities
Cyberattacks continue to shift
tactics, with hackers launching
fileless malware that is undetectable
by ransomware safeguards, antivirus
and other traditional endpoint
protection platforms.
Cyberbit’s adaptive Endpoint
Detection
and Response (EDR) platform, now
provides advanced and semi-automated
threat hunting, centralized response
capabilities, and an improved SDK for
detection customization.
Originally developed to meet
requirements of high-risk organizations,
Cyberbit’s new EDR enhancements help
customers decrease threat detection and
response times while minimizing false
positives, drastically improving
cyberattack countermeasures and cutting
distractions for security teams.
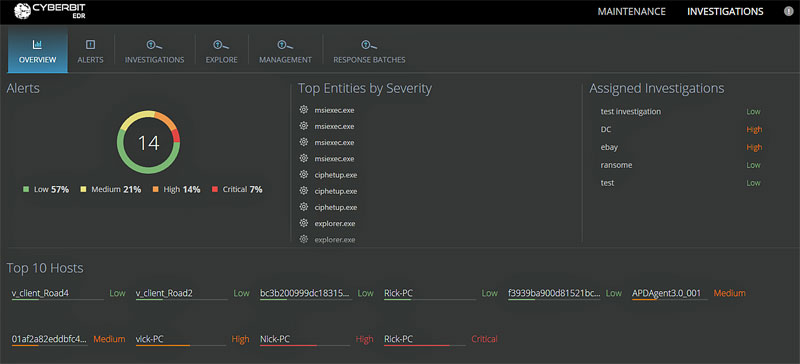
Cyberbit EDR’s approach detects a broad
range of attacks without relying on
indicators of compromise (IOCs),
including signature-less, fileless and
targeted attacks as well as ransomware.
The adaptive approach automatically
tailors a behavioral detection policy to
the customer’s organization, which
ensures the highest levels of accuracy
based on each environment.
Danielle VanZandt, research analyst at
Frost & Sullivan
"Cyberbit provides one of the most
effective solutions for detecting
unknown, signature-less and targeted
threats, including fileless attacks and
ransomware, by using machine learning
and behavioral analytics, enabling quick
identification of root cause and
response," said Danielle VanZandt,
research analyst at Frost &
Sullivan.
"Cyberbit’s approach proved to provide
its customers with substantially higher
detection and response capabilities,
while keeping low false positive
ratios."
"As a result, security teams can focus
on high priority alerts and are not
distracted and overloaded with false
alarms."
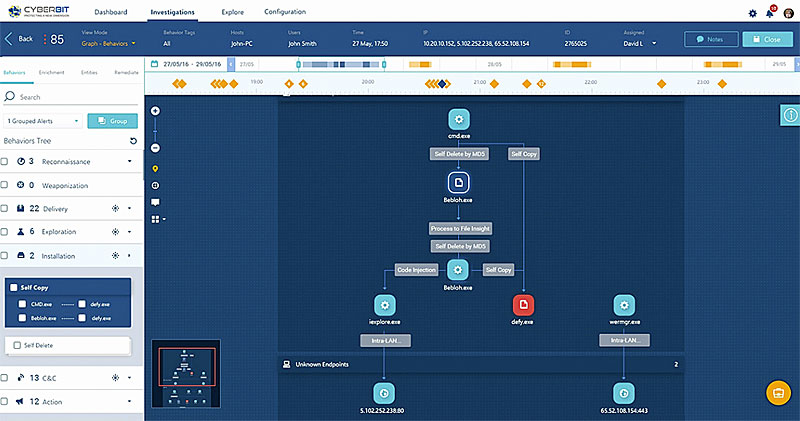
Cyberbit
The new release includes the
following key features:
Analyst in a Box
Analysts often work with fragments of
the attack story; using their knowledge
and experience, they seek traces of
attacks buried in data.
Cyberbit's EDR platform assists analysts
by automating much of the hunting
process, leveraging behavioral analytics
and machine learning, which serves as an
"analyst in a box," speeding up threat
identification and often saving weeks of
investigative effort.
SDK and customization
Advanced customers can add proprietary
detection algorithms to address their
unique security requirements. They can
also access the EDR's big-data
repository using APIs, and use their own
functions and tools to proactively
investigate and hunt threats.
Centralized response capabilities
Ideal for large, dispersed
organizations, security managers can
access any endpoint in the organization
from a central location and rapidly
investigate and respond to an incident,
which eliminates the need to be
physically present at the compromised
endpoint.
"It takes only one fileless or
signature-less attack to bring down an
organization; however, these attacks are
invisible to endpoint security systems."
"Customers now understand that this is
where they need to focus," said Adi Dar,
CEO of Cyberbit.

"Our EDR is gaining traction as one of
the most reliable means to protect
against advanced attacks, and this new
release helps customers stay ahead of
new threats and save time with
next-generation SOC technology."
Cyberbit was recently named by CRN
magazine one of 20
coolest
endpoint security vendors for 2017.
Cyberbit EDR is also the winner of the
Frost and Sullivan Technology Leadership
Award for Cybersecurity Detection and
Response, and the winner of the Network
World
Asia Reader’s Choice Rising Star award
for endpoint security.
2017.3.31
Implementing Strong
Authentication for Office
365 with Gemalto SafeNet
Authentication Service
With Microsoft Office 365, organizations
can move their familiar Office
environments to the cloud. But unlike
traditional enterprise productivity
suites, Office 365 creates a new reality
in which employees, whether in the
office, at home, or on the road, are in
effect accessing enterprise systems
remotely. Without traditional access
controls implemented via the enterprise
network, the only protection afforded
these online services are inherently
weak, static passwords.
By implementing strong authentication
for Office 365 with SafeNet
Authentication Service by Gemalto,
organizations can significantly mitigate
the risk of unauthorized access and data
breaches.
Watch
video to learn how to use
SafeNet MobilePASS+ to secure access to
Office 365!
Using SafeNet Authentication Service
with Office 365
SafeNet Authentication Service by
Gemalto can be used as the trusted
identity provider, extending Active
Directory identities, and adding strong
authentication to Office 365. Providing
a wide range of authentication methods,
including out-of-band (OOB), personal
identification pattern, and both
hardware and software-based one-time
password (OTP) form factors, SafeNet
Authentication Service provides a sound
balance between cost, convenience, and
security. Two implementation options are
available:
I. Strong
authentication using the Gemalto AD FS
Agent
Organizations want to implement unified
strong authentication policies for
client and web-based applications can
use Microsoft’s AD FS (Active Directory
Federation Services) with the Gemalto AD
FS Agent. The Gemalto AD FS Agent
enables the implementation of strong
authentication policies for cloud-based
services such as Office 365 and other
client and web-based applications. The
Gemalto AD FS Agent is available for AD
FS 3.0, which was released with Windows
Server 2012 R2.
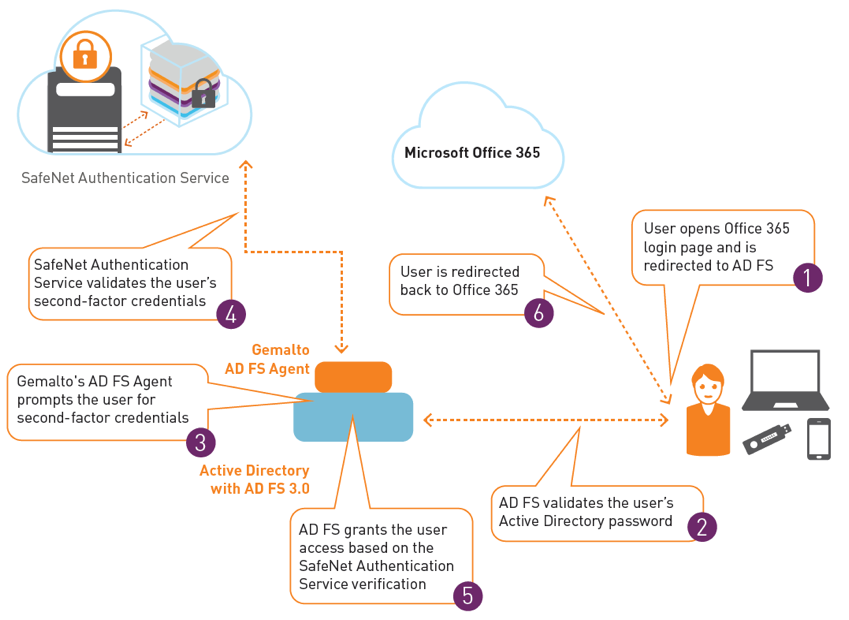
II. Strong
Authentication Using AD FS and SafeNet
Authentication Service as a SAML
Identity Provider
Organizations that want to extend strong
authentication to Office 365 and other
browser-based applications have the
option of using AD FS with SAML
(Security Assertion Markup Language).
With this option, Gemalto SafeNet
Authentication Service is configured as
a SAML 2.0 Identity Provider for AD FS
when users log in to Office 365.
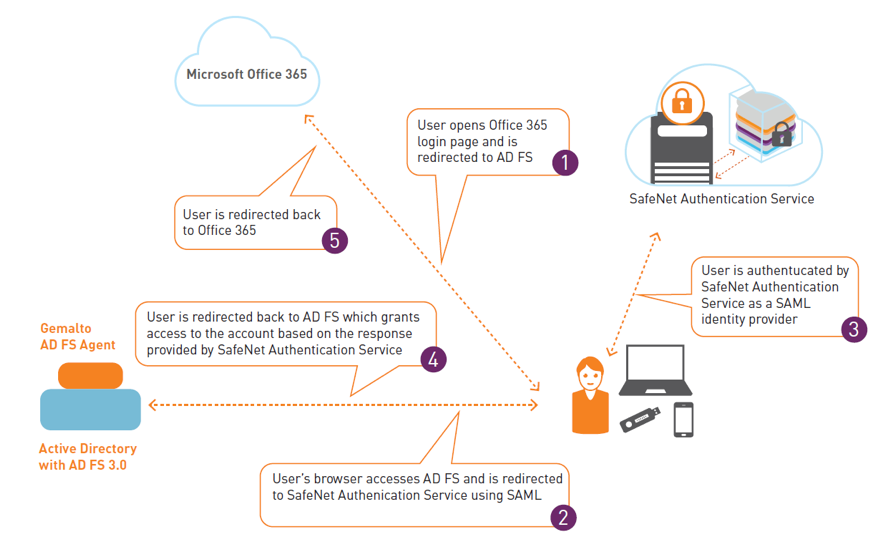
About SafeNet Authentication Service
SafeNet Authentication Service by
Gemalto delivers fully automated, highly
secure authentication-as-a-service, with
flexible token options tailored to the
unique needs of your
organization—substantially reducing the
total cost of operation. With no
infrastructure required, SafeNet
Authentication Service enables a quick
migration to a multitier and
multi-tenant cloud environment,
offering:
° Fully customizable interface
° Extensive self-service portals
° Embedded identity federation for securing access to SaaS and web-based applications
° Protection of all resources, including networks, VPNs, SaaS applications
° Numerous token options
° No infrastructure investments
° Quick deployment and setup
For further information about SafeNet
Authentication Service, please contact Bread
Wong or (852) 28510271 (Office).
2017.3.16
IT Technologies &
Solutions for Hotel Industry
On 16-March-2017, our Business
Development and Sales Manager, Norman
Chan was being invited to speak in a
Seminar on “Latest IT Technologies &
Solutions for Hotel Industry”. The
Seminar was organized by Hutchison
Telephone Macau & Macau Productivity
and Technology Transfer Center and
Supported by to major Macau Hotel
Associations: The Macau Hotel
Association & Macao Hoteliers &
Innkeepers Association. Mr. Chan Topic
was “Using SOTI MobiControl Enterprise
Mobility Management (EMM) Solution to
Manage the Mobile Device of the Hotel”
with a Peninsula Hotel case study.
 |
 |
 |
 |
2016.12.21 ObserveIT Insider Threat Video Best Practice featuring Gartner
With data breaches and data theft occurring more quickly and with more sophistication than ever before, protecting your organization against cyber security threats has likely proven increasingly difficult.Companies have commonly focused a majority of resources on protecting against malicious outsiders. And, while hacking and phishing are still a major cause for concern, it’s insiders—trusted employees, contractors and vendors—that have become the most cited culprits of cybercrime. There are myriad reasons for this, including infrequent security policy training, lack of employee ability to provide feedback to security teams, and, of course, purposeful insider attacks. For this reason, CISOs are increasingly looking for tools to identify and eliminate accidental and malicious insider activity.
As organizations evaluate user activity monitoring as a part of their plan to thwart insider threats, there are many questions that arise, including:
• Who are the insiders that put organizations at risk… and what are their motives?
• What types of organizations and data are most targeted?
• What can organizations do to mitigate the risk of insider threats?
Gartner Vice President, Anton Chuvakin, and ObserveIT’s Gaby Friedlander address these questions and discuss best practices for Insider Threat programs in the Garnter Research Video preview below.

Learn more about keeping your data safe from insider threats, please contact breadwong@udshk.com or watch the full video that provides insights on specific actions you can take to help protect your organization.
2016.10.20
UDS carries HID
Lumidigm V-Series V302
Fingerprint Sensors to
support Hong Kong Next
generation Smart ID Card
Project

Benefits
| • The industry’s
best fingerprint images • The industry’s best biometric matching performance for any person in any environment • Premium liveness detection to insure only genuine fingers can be matched • Increased throughput and user convenience: single-placement failure to enroll (FTE) and failure to acquire (FTA) errors are eliminated • Multiple integration options to enable rapid integration in a wide variety of applications |
Product Features
| |
• Images surface
and subsurface fingerprint
features using Lumidigm’s patented
multispectral imaging technology • High-contrast 500 dpi images • Multiple communication interfaces supported: USB 2.0, RS-232 • ANSI 378 / MINEX-certified biometric templates • Local verification (1:1) functions with template storage up to 1,000 users • Identification (1:N) capacity up to groups of 10,000 fingers • Small, ready-to-integrate form factor for easy mechanical integration • Operates across wide ranges of temperature, relative humidity, and ambient light • High durability glass platen with no coatings that wear out. |
If you are interested in HID Lumidigm V-Series Fingerprint Sensors, please call us at 2851 0271 or email to <info@udshk.com> for more detail.
2016.9.15 Sophos Launches Next Generation of Anti-Exploit and Anti-Ransomware Technology
On September 15, 2016 Sophos announced Sophos Intercept X, a next-generation endpoint security product that stops zero-day malware, unknown exploit variants and stealth attacks, and includes an advanced anti-ransomware feature that can detect previously unknown ransomware within seconds. Sophos Intercept X installs alongside existing endpoint security software from any vendor, immediately boosting endpoint protection by stopping malicious code before it executes.Click and watch this short video to see it in action.

Sophos Intercept X combines four critical security components that IT administrators should expect from next-generation endpoint protection.
- - Signatureless Threat and Exploit Detection: Anti-malware and anti-hacker defense that blocks zero-day, unknown and memory resident attacks and threat variants without the need for file scanning
- CryptoGuard: Anti-ransomware innovation that identifies and intercepts malicious encryption activity, blocks ransomware before it can lock and cripple systems and can roll back maliciously encrypted files to their pre-attack state
- Root Cause Analytics: A 360 degree visual analysis of attack events that shows where the attack came in, what it affected, where it may have stopped and recommended actions to prevent a similar attack in the future
- Sophos Clean: Powerful utility that hunts for and removes any trace of spyware and deeply embedded, lingering malware
 Short Video: Sophos Intercept X - Root-Cause Analysis (RCA) in Two Minutes |
If you are interested in next-generation endpoint protection, please call us at 2851 0271 or email to <info@udshk.com> for more detail.
2016.7.10 SOTI MobiControl named 2016 "Editors' Choice" in PC Magazine MDM product Review

Recently, PC Magazine awarded SOTI MobiControl the prestigious distinction of “Editors’ Choice” as part of their mobility management roundup for 2016.
SOTI brings support for all major mobile platforms, including Android, iOS, Windows, with deep remote control capabilities.
Read why SOTI MobiControl was named “Editors Choice” by PC Magazine in their review of top MDM solutions for 2016.
This article & review provides your customers with a great third-party analysis of the benefits of SOTI MobiControl, including:
“SOTI MobiControl matches up with all of the products in this roundup quite well, and stands out from the rest with the remote control feature.”
“A staging capability for corporately owned devices makes it easy to fully configure the SOTI agent before issuing it to an employee.”
SOTI brings support for all major mobile platforms, including Android, iOS, Windows, with deep remote control capabilities.
Read why SOTI MobiControl was named “Editors Choice” by PC Magazine in their review of top MDM solutions for 2016.
 The Best
Mobile Device Management (MDM) Solutions
of 2016:
The Best
Mobile Device Management (MDM) Solutions
of 2016:http://www.pcmag.com/article/342695/the-best-mobile-device-management-mdm-software-of-2016
PC Magazine Editors' Choice 2016:
http://www.soti.net/resources/white-papers/soti-mobicontrol-pc-magazine-editors-choice-2016
About SOTI Inc.
SOTI is the world's most trusted
provider of Enterprise Mobility
Management (EMM) solutions, with over
15,000 enterprise customers and millions
of devices managed worldwide. SOTI's
innovative portfolio of solutions and
services provide the tools organizations
need to truly mobilize their operations
and optimize their mobility investments.
SOTI's flagship product, MobiControl,
allows enterprises to enable, optimize
and secure their mobile workforce across
all platforms to support
corporate-liable and Bring Your Own
Device (BYOD) policies. SOTI extends
secure mobility management beyond basic
MDM to provide a total, flexible
solution for comprehensive management
and security of all mobile devices
deployed in an organization.
2016.06.24
Cisco
OpenDNS - Multi-layer
Defence against
Ransomwares
On 24 Jun 2016, Cisco, Ingram Micro and
UDS co-organised an Encryption
Ransomware seminar. In the seminar,
security experts from the market shared
weapon, strategies to handle security
incidents, such as malwares and
ransomwares, and ways to perform cyber
threats investigation in different
companies.
Why OpenDNS?
Cisco OpenDNS has the largest DNS
service built for security. Its global
network processes 80+ billion Internet
requests daily from 65 million users
with 100% uptime. Statistical models are
applied to this data to accurately
identify, predict and prevent known and
emergent threats. Every day OpenDNS
blocks 80+ million malicious requests
and gains predictive intelligence on 17+
million new domain names. Best of all:
there is no hardware to install or
software to maintain!
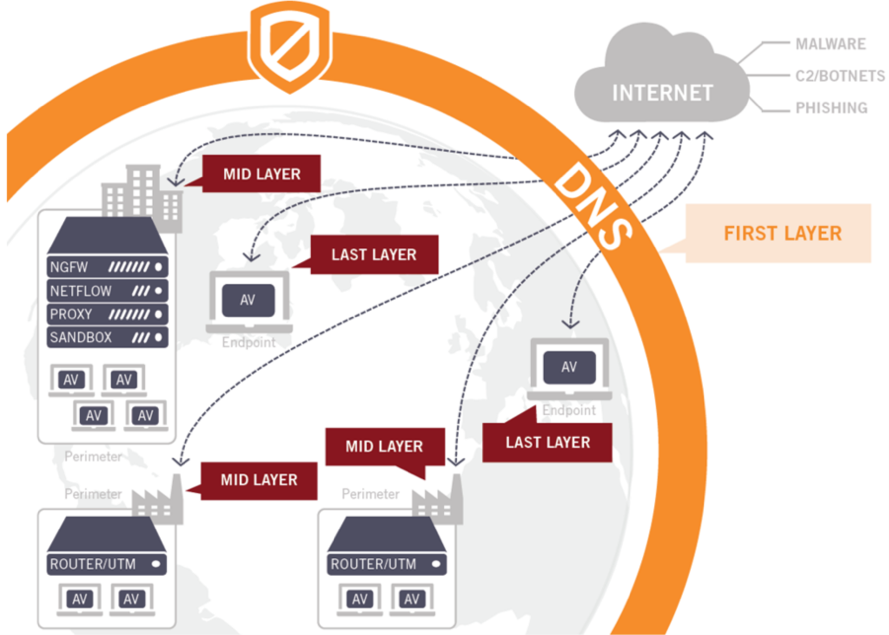

If you are interested in Cisco OpenDNS, please feel free to contact Mr Eric Moy for more details.

2016.06.17 Splunk, ObserveIT and OpenDNS in the AWS Summit HK 2016


In addition to AWS, UDS carries three cool outstanding products: Splunk, ObserveIT and OpenDNS. You just can’t miss out any one of them.
 |
Splunk is a big data monitoring and BI tool for all machine data. It offers the leading platform for Operational Intelligence. Insights from using Splunk help make your company more productive, profitable, secure and competitive. UDS is the distributor of Splunk. |
|
| ObserveIT detects insider threats and stops data loss. It provides Employee Monitoring, Behavioural Analytics, Policy Enforcement and Forensic Recording. UDS is the distributor of ObserveIT. | ||
 |
|
OpenDNS provides
cloud-delivered network security
and threat intelligence, which
safeguards you from Ransomwares
and various DNS attacks
everywhere. UDS is the first
Partner of Cisco OpenDNS in Hong
Kong. |


UDS Team: Mr. Frankie Leung, Mr. Bread Wong, Mr. Paul Chow, Mr. Johnny Lam, Mr. Eric Moy and Mr. KL To (from left to right).
If you are interested in any of the above-mentioned products, please feel free to contact us at ericmoy@udshk.com (AWS and OpenDNS) and breadwong@udshk.com (Splunk and ObserveIT).
2016.05.21 Splunk Hands-on workshop in PISA Jam event


On 21 May 2016, UDS organised a hands-on workshop, Detects Advanced Attack as the Blue Team, in the 15th Anniversary of PISA (專業資訊保安協會) event on the theme of security of everything, big data, forensic, honeynet and mobile.


Mr. Charles Mok (left photo above), Legislative Councilor (Information Technology), delivered a speech.
Mr. Paul Pang (right photo above), the Chief Security Strategist of Splunk, delivered a hands-on workshop on making use of Splunk to detect advanced attacks. He aroused all attendees’ interests in Splunk and won a burst of applause.
Last but not least, in addition to UDS tailor-made souvenirs, thank you for Splunk sponsoring the giveaways.

2016.5.9 Crypto Ransomwares Attack are wild. Use Amazon Web Services to Backup Company Data & Files

Crypto Ransomware attacks are getting
wild in Hong Kong. The Hong Kong
Computer Emergency Response Team
Coordination Centre (HKCERT) of the
Hong Kong Productivity Council alerted
the public to be vigilant to the
ransomware attacks that hold data
hostage and demand ransom from the
victim.
Hackers have launched the attacks
through globalized massive spam
campaigns and compromised many websites
to host the malicious code. Victimized
computers are infected by opening email
attachments or clicking the hyperlinks
of websites with malicious code. On the
other hand, a website injected with the
malicious code will redirect visitors to
an exploit website which hosts the
attack code. The latter will further
attack the security vulnerabilities of
the users’ computer system and
applications and install the Crypto
Ransomware. The malicious code usually
targets Web Browsers users.
To protect data from Crypto Ransomware attack, HKCERT advises the macro feature of Microsoft office should be turned off, and only re-enabled temporarily when necessary and under secure condition. In addition, users are advised to delete any suspicious emails received. The Internet users should regularly backup data and keep an offline copy of the backup, and keep security software updated, patch system and other software.
For backing up company valuable data,
UDS advises companies that you use
Amazon Web Services (AWS). AWS offsite
backup solution is high security, high
performance & can setup fast.
Companies can use a mixture of AWS
Storage-Gateway, S3 & Glacier
Services for backup data and schedule to
do the backup automatically. The AWS
Storage Gateway is a service connecting
an on-premises software appliance with
cloud-based storage to provide seamless
and secure integration between an
organization’s on-premises IT
environment and AWS’s storage
infrastructure. Usually AWS S3 is for
Mid-Term Data Storage up to 6 months
& AWS Glacier is for Long-Term Data
Storage beyond 6 months.
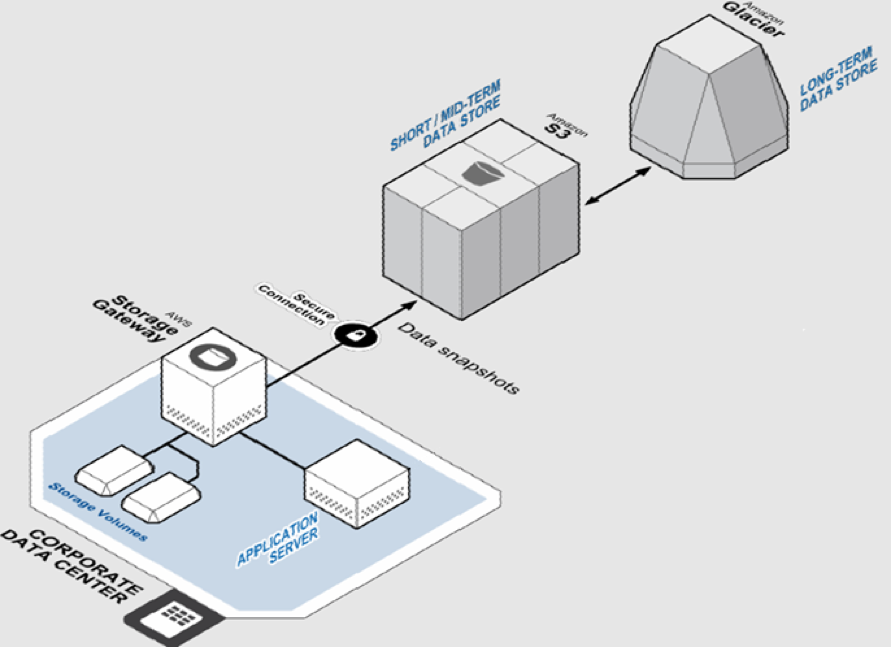
Interest to Securely Backing up your
Company Data & Files to Amazon Web
Services to protect against Crypto
Ransomware Attack, please call 2851 0271
for Eric Moy <ericmoy@udshk.com>
or
Norman Chan <normanchan@udshk.com>
for more detail.
2016.3.12 Splunk won two SC Magazine 2016 U.S. Awards, leading in Gartner reports and IT Central Station ranking
 |
Splunk, provider of the leading software
platform for real-time Operational
Intelligence, announced Splunk
Enterprise Security (ES) won the
Excellence Award for the Best SIEM
Solution at the 2016 SC Magazine
Awards. Splunk Enterprise also won the
Trust Award for the Best Fraud
Prevention Solution. This is the
fifth consecutive year Splunk solutions
have been honoured by the U.S. SC
Magazine Awards.
In latest two Gartner reports, Splunk
was named a leader for the third
straight year as depicted in the 2015
Magic Quadrant and the 2015 Critical
Capabilities for SIEM.
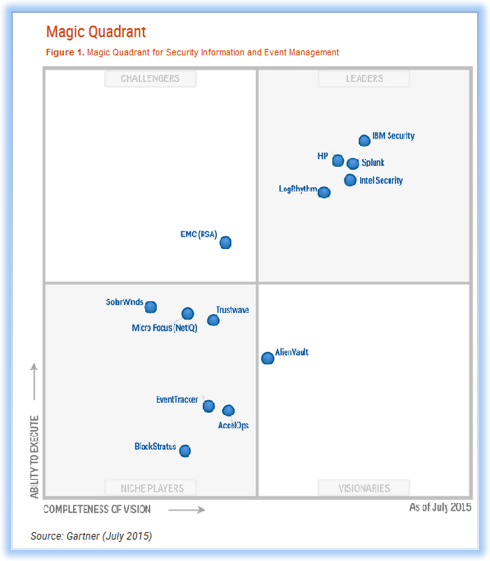 |
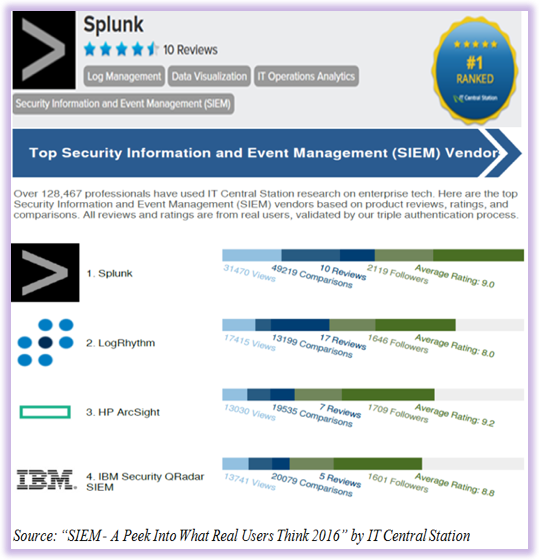 |
Splunk ranks No.1 among top SIEM
vendors shown at IT Central Station
website. IT Central Station helps tech
professionals by providing a
comprehensive list of enterprise level
Security Information and Event
Management (SIEM) vendors. IT
Central Station also compiles reports
based on product reviews, ratings, and
comparisons from over 128,467
professionals having using IT Central
Station research on enterprise tech. All
reviews and ratings are from real users,
validated by our triple authentication
process.
From now on until 24 March 2016, you
are invited to nominate leading
technology products for the
Computerworld Hong Kong Awards 2016. If
you have similar views on SIEM category
as the IT Central Station review does,
please nominate Splunk online
or download the nomination form here.
2016.3.10 We are proud to be listed as standard partner of Amazon Web Services (AWS)


Why AWS Service
The AWS Cloud provides a broad set of
infrastructure services, such as
computing power, storage options,
networking and databases, delivered as a
utility: on-demand, available in
seconds, with pay-as-you-go pricing.
Amazon Web Services (AWS) is a secure
cloud services platform, offering
compute power, database storage, content
delivery and other functionality to help
businesses scale and grow. Explore how
millions of customers are currently
leveraging AWS cloud products and
solutions to build sophisticated
applications with increased flexibility,
scalability and reliability.
UDS have five AWS Certified Solutions
Architect and will be have totally 6
soon.
2016.3.9 Splunk and UDS co-joined the itSMF Annual Conference 2016 at Cordis Hotel
With the emergence of cloud computing and Software-as-a-Service (SaaS), businesses need to accelerate the design and implementation of ITSM processes and capabilities to manage their cloud infrastructure, maintain efficient services delivery, and align both development and operations. As a cloud continues to grow, the complexity and costs of data migration and cloud integration often outweigh the benefits. Through successful cloud IT Service Management, IT professionals can ensure their cloud services - whether they are private, public or hybrid - operate with well-defined processes, best-practice management and guaranteed SLAs. This not only protects the performance, efficiency and reliability of cloud-based services, but also helps to lower the associated security risks and TCO. The annual itSMF conference fosters IT leaders and ITIL practitioners to exchange ideas, skills and experiences on how to advance clouds with the latest ITSM strategy, technology and solutions.
 |
 |
 |
 |
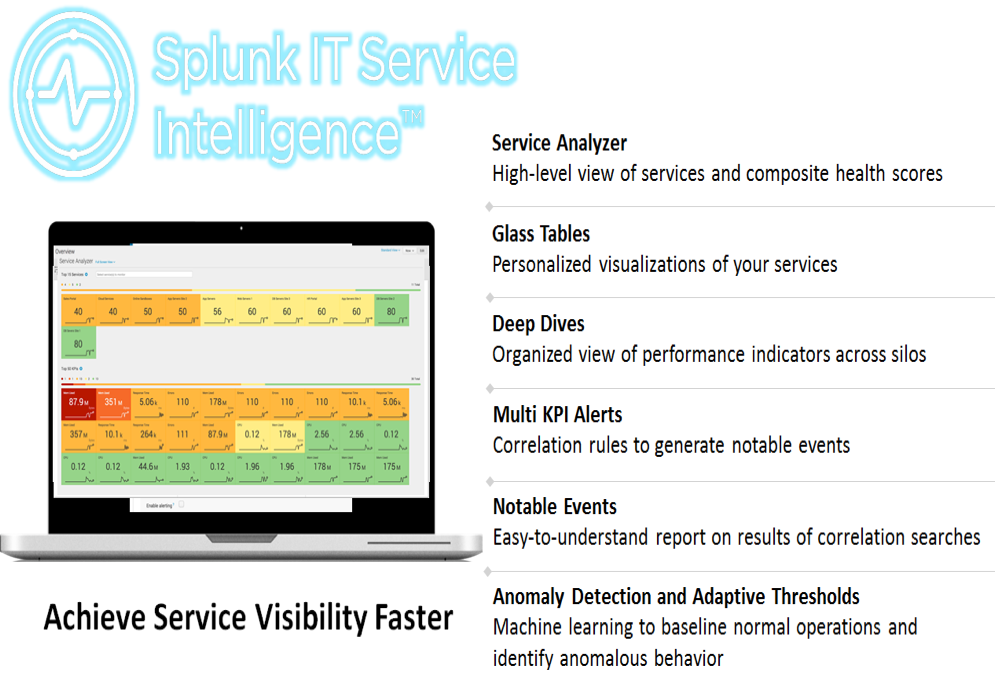
Mr Kelvin Yeung, Senior Big Data Architect of Splunk, was one the speaker who delivered a topic called “Next-generation Data-driven Monitoring and Analytics Platform with Splunk IT Service Intelligence”. UDS Splunk Architects and Sales & Marketing Team worked together with Splunk Sales Team in the conference. During the conference, they shared Splunk business, technical experience, use cases and demo with guests and partners.
2016.2.29 Centrify leads Identity-as-a-Service Market in delivering derived Credential Authentication support for mobile devices
Smartcards contain cryptographic credentials that allow users to authenticate without usernames and passwords. However, the physical cards — Typically Personal Identity Verification (PIV) or Common Access Cards (CAC) — require a dedicated reader. Many laptops include this reader as part of their hardware, and those that don’t can make use of a USB-based reader.
However, attempting to use PIV or CAC cards with mobile devices has, until recently, been a real challenge. The small form factor of today’s smart devices just isn’t compatible with a smartcard reader, and external readers (often called “sleds”) are costly, only work with certain devices, and generally don’t fit today’s employee needs.
Derived credentials can solve these issues. With derived credentials, the cryptographic credential is stored securely on mobile devices, in compliance with today’s smartcard regulations. This means no need for a dedicated reader and much more flexibility for users.
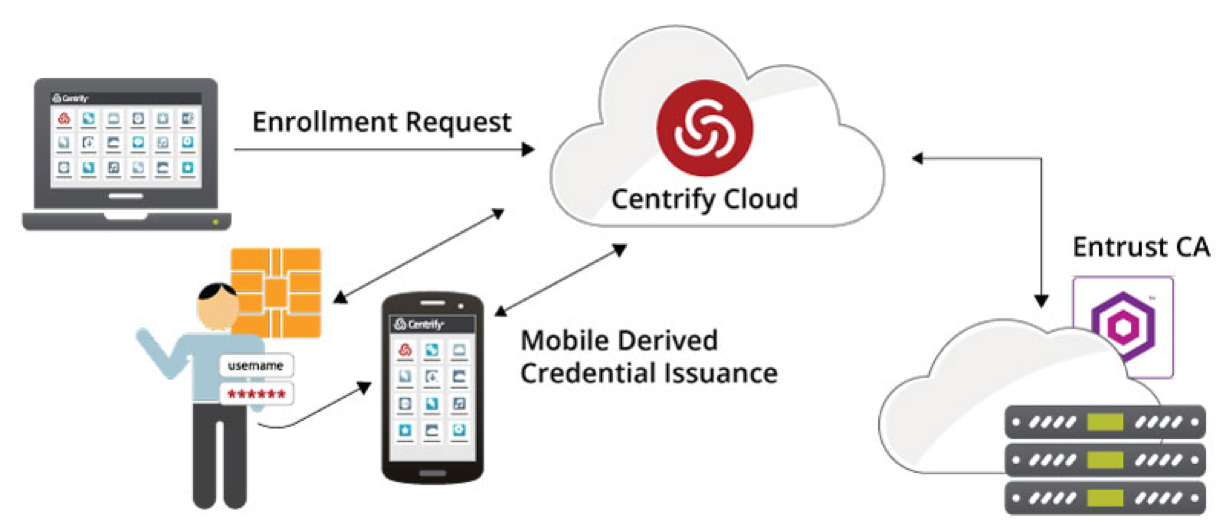
At a glance, Centrify’s derived credentials offer the following benefits:
• Secure CAC/PIV based SSO to cloud and on-premises apps
• Integrated device management to manage and lock down devices
• The ability to enroll devices and provision derived credentials to them
• Derived credential issuance from popular certificate authorities
• Compliance with FIPS 201-2 and NIST SP 800-157 to satisfy HSPD-12 and OMB-11-11, allowing mobile access to apps, websites, and services that require smart cards authentication
• App provisioning to set up user accounts within target applications
• Workflow to ensure only the right users get access
• Easy deployment into existing enrollment and issuance portals
For enterprises that need stronger authentication that eliminates passwords — or Federal agencies and other organizations who must meet Homeland Security Presidential Directive 12 (HSPD-12), NIST guidance and other security mandates for smart card authentication — Centrify’s derived credential solution provides a seamless way to provide mobile access without compromising security.
For more information, please visit https://www.centrify.com/ or send us an email to info@udshk.com.
2016.2.23 Splunk IT Service
Intelligence - The
next-generation monitoring
and analytics solution
UDS, Splunk’s authorised distributor
and co-provider for professional
services in Hong Kong and Macau, has
been realizing tremendous value across
multiple industries and use cases for
customers. From blue-chips to small
companies, retail shops, financial
enterprises, logistic service providers,
telecommunications, entertainments, NPOs
and government agencies are improving
service levels, reducing IT operations
costs, mitigating security risks and
driving new levels of operational
visibility.
Splunk IT Service Intelligence (ITSI)
is a next-generation monitoring and
analytics solution that provides new
levels of visibility into the health and
key performance indicators of IT
services.
Splunk IT Service
Intelligence
•
Data-driven service monitoring and
analytics

• Delivers a central,
unified view of critical IT services for
powerful, data-driven monitoring
• Maps critical
services with KPIs to easily pinpoint
what matters most
• Utilizes advanced
analytics powered by machine learning to
highlight anomalies, detect root cause
and pinpoint areas of impact
• Supports drill down
deep into the data for rapid issue
investigation and resolution
Why Splunk IT Service Intelligence?
Monitor business and service activity using metrics and indicators that are aligned with strategic goals and objectives
Eliminate costly false alerts, understand trends and anomalies and employ machine learning to baseline normal operations.
Simplify and speed up troubleshooting by collecting and correlating metrics and events across the service stack.
Easily consolidate data across diverse technologies and point tools for multi-dimensional analysis and simplified workflows.
Support data collection and deployment for on-premises, cloud and hybrid environments.
Install quickly, connect to any data source effortlessly and begin interacting with the data immediately.
Watch Video for more information: Data-Driven Service Intelligence
Learn more about Splunk ITSI: Watch Splunk ITSI product tour or browser Splunk ITSI page.
If you are interested in Splunk ITSI, please send a request to info@udshk.com for a product demo.
What’s new about Splunk ITSI event? Splunk will join the itSMF Annual Conference. If you feel interested, please contact us.
Date: 9 March, 2016 (Wednesday)
Time: 9:00 – 17:00
Venue: Level 7, Cordis Hong Kong (Langham Place), Mongkok
2016.1.16
Mr.
Frankie Leung acts as
President of International
Information Systems Security
Certification Consortium
(Hong Kong Chapter)
Mr. Franke Leung (CISSP, CISA, CISM,
CRISC) was elected to be the President
of (ISC)2 Hong Kong Chapter in the 2016
Annual General Meeting. He will work
closely with PISA (Professional
Information Security Association) to
promote the Information Security and
(ISC)2 Credential certification program
in Hong Kong.
 (ISC)2 Hong
Kong Chapter was set up in 2012. It aims
to provide members and other security
professionals with the opportunity to
share knowledge, grow professionally,
raise security awareness and advance
information security in Hong Kong.
(ISC)2 Hong
Kong Chapter was set up in 2012. It aims
to provide members and other security
professionals with the opportunity to
share knowledge, grow professionally,
raise security awareness and advance
information security in Hong Kong.
 (ISC)2 Hong Kong Chapter
operates as a special interest group
(SIG) of the Professional Information
Security Association (PISA). PISA
(www.pisa.org.hk) is a Hong Kong based
not-for-profit Information Security
organization. Eight officers are elected
in the (ISC)2 Hong Kong Annual General
Meeting.
(ISC)2 Hong Kong Chapter
operates as a special interest group
(SIG) of the Professional Information
Security Association (PISA). PISA
(www.pisa.org.hk) is a Hong Kong based
not-for-profit Information Security
organization. Eight officers are elected
in the (ISC)2 Hong Kong Annual General
Meeting.
2016 (ISC)2 HK Chapter Committee
Member
Frankie Leung (President)
Frank Chow (Secretary)
Frankie Wong (Treasurer)
Joyce Fan (Membership Chair)
Mike Low (Program Director)
Jim Shek (Program Director)
Vincent Ip (Professional Development)
Martin Ho (Liaison)

For more information of (ISC)2 HK
Chapter and PISA, please visit
www.pisa.org.hk
http://www.isc2chapter.hk/
https://www.facebook.com/PISAHKG?fref=ts
https://www.facebook.com/ISC2HK?fref=ts
2016.1.13 Centrify delivers industry’s first Federated Privileged Access Service to protect enterprises with outsourced IT
![]() the
leader in securing enterprise identities
against cyberthreats that target today’s
hybrid IT environment of cloud, mobile
and on-premises, is the first vendor in
the industry to support federated
privileged access across an
organization’s entire security
eco-system, including secure outsourcing
of IT and application development. The
solution is designed for an enterprise’s
hybrid IT environment of cloud, mobile
and on-premises and leverages the
Centrify Identity Platform. Coupled with
other major new features such as
application-to-application password
management (AAPM) and multi-factor
authentication (MFA) for servers,
Centrify’s Privileged Identity
Management solution reduces an
enterprise’s attack surface and enables
continuous compliance.
the
leader in securing enterprise identities
against cyberthreats that target today’s
hybrid IT environment of cloud, mobile
and on-premises, is the first vendor in
the industry to support federated
privileged access across an
organization’s entire security
eco-system, including secure outsourcing
of IT and application development. The
solution is designed for an enterprise’s
hybrid IT environment of cloud, mobile
and on-premises and leverages the
Centrify Identity Platform. Coupled with
other major new features such as
application-to-application password
management (AAPM) and multi-factor
authentication (MFA) for servers,
Centrify’s Privileged Identity
Management solution reduces an
enterprise’s attack surface and enables
continuous compliance.
The outsourcing service retains management of their employee identities, and the customer organization uses Centrify to grant web-based access and privilege for systems and applications. Privileged access is governed through request and approval workflows, monitoring with optional termination of privileged sessions and reconciliation of approved access versus actual access to critical infrastructure. The solution supports businesses outsourcing to more than one service organization while ensuring identity lifecycle management for outsourced IT administrators and developers remains with their employer, including the disabling of their enterprise identity upon employment termination.
In addition to federated privileged
access, Centrify’s products work in
tandem to offer a comprehensive,
integrated security solution built for
the modern enterprise. New capabilities
for Centrify’s identity management for
privileged user solution include the
following:
(a) Minimize
attack surface
• Local account
provisioning — Centrally manage the
lifecycle for application and service
accounts on UNIX and Linux systems, and
automatically secure and manage
credentials
and access.
•
Application-to-application password
management ― Eliminate hard-coded, plain
text account passwords from scripts and
applications. Applications and
scripts
authenticate and retrieve passwords
securely without human intervention,
enabling organizations to meet
compliance and security policies.
• Privileged access
request ― Grant temporary, time-bound
privileged access to on-premises and
cloud-based infrastructure to minimize
attack surface and reduce risk.
• Secure password
storage ― In addition to using the
secure data store of the Centrify
Identity Platform to store all user,
resource, account, and password
information,
Privilege Service now supports SafeNet
KeySecure key management appliances from
Gemalto for encrypted storage of account
passwords on-premises.
(b) Thwart
in-progress attacks
• Multifactor
authentication for servers ― Protect
against hackers using stolen passwords
and credentials by configuring
multi-factor authentication (MFA) for
IT
administrators who access Linux systems
and require elevated privileges.
(c) Govern access
and prove compliance
• Reconcile
approved and actual access ― Easily
prove access controls are working as
designed by reconciling approved access
with actual access.
• Reporting services ―
Report on who did what, where and when,
who has access to what and how they can
use that access to meet complex
regulatory requirements. Select or
schedule packaged attestation reports or
create your own.
Get Users to Log in as Themselves,
while Maximizing Control over
Privileged Accounts
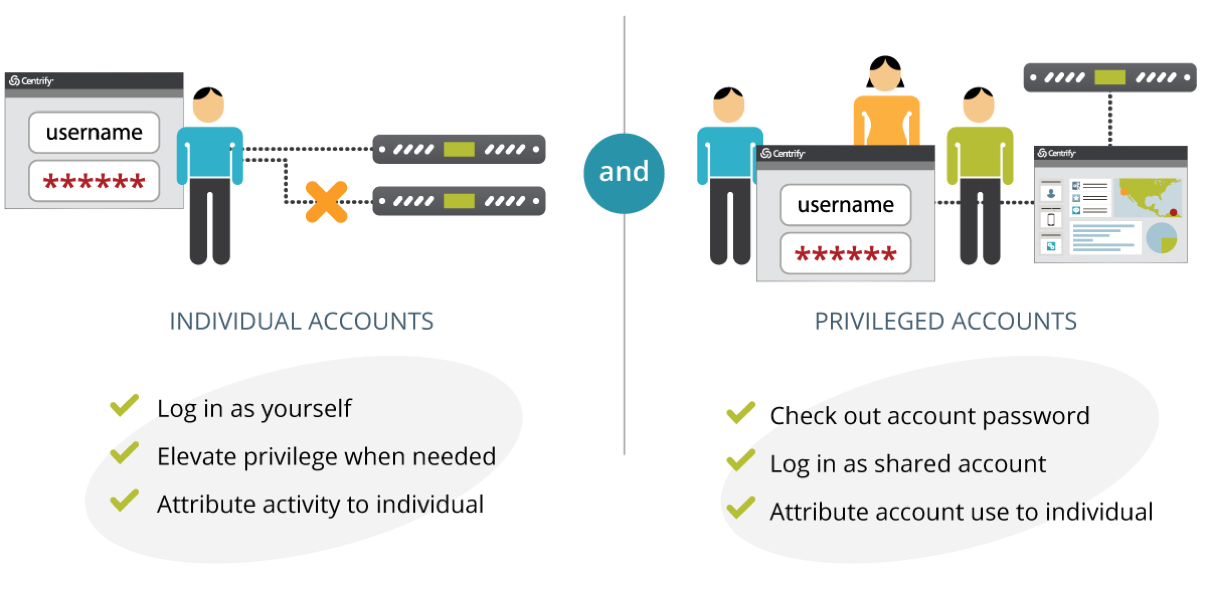
For more information, please visit
https://www.centrify.com/ or send us an
email to info@udshk.com.
2015.9.30 Splunk Workshop: Strengthening Cybersecurity to Improve APT Defense in the Financial Sector
Financial institutions face a challenging environment in which cyber threats are growing in severity and sophistication. Splunk has been working with many large finance institutions as the core SOC platform to address the APT defense requirement.
The reference architecture, in which Splunk serves as the Operational Intelligence platform, can help financial institutions reduce their risk by enhancing the visibility of assets, identifying vulnerable assets and enabling faster response to security threats.

Splunk Enterprise Splunk User Behavior Analytics Splunk Enterprise Security
Splunk User Behavior Analytics (Splunk UBA) is an out-of-the-box solution that helps organizations to find known, unknown, and hidden threats using data science, machine learning, behavior baseline, peer group analytics and advanced correlation. It presents results with risk ratings and supporting evidence so that an analyst and a hunter can quickly respond and take actions.
• Detects APTs, malware infections, and insider threats without writing signatures, rules, policies, or human analysis
• Improves threat detection and targeted response using a variety of threat indicators and supporting evidence within context of the kill chain to enable targeted
remediation
• Dramatically increases SOC efficiency with rank ordered lists showing events in the kill chain linked from summary to supporting information over time
• Seamlessly integrates threat information with Splunk Enterprise and Splunk App for Enterprise Security, to further scope, disrupt, contain and recover from the attack
Splunk Enterprise Security (ES) is a premium security solution that provides insight into machine data generated from security technologies such as network, endpoint, access, malware, vulnerability and identity information. It enables security teams to quickly detect and respond to internal and external attacks to simplify threat management while minimizing risk and safeguarding your business. Splunk Enterprise Security streamlines all aspects of security operations and is suitable for organizations of all sizes and expertise. Whether deployed for continuous real-time monitoring, rapid incident response, a security operations center (SOC), or for executives who need a view of business risk, Splunk ES delivers the flexibility to customize correlation searches, alerts, reports and dashboards to fit specific needs. ES can be deployed as software together with Splunk Enterprise or as a cloud service together with Splunk Cloud.
Please join us and register the Splunk Techinical Workshop, which will take place on 7 January 2016 (Thu) at Splunk Hong Kong Office, and learn how more than 10,000 enterprises, service providers and government agencies in 100 countries use Splunk in their cyber security projects. If you are unavailable to join but would like to have a copy of the workshop materials, please send an email to breadwong@udshk.com.
2015.7.31
2015
Asia Pacific ISLA
Honorees
2015.7.31.
Mr.
Frankie Leung recognized as
Honoree for the Category of Senior
Information Security Professional in
Asia Information Security Leadership
Achievement (ISLA).
Hong Kong July 31, 2015— (ISC)²®
the largest not-for-profit membership
body of certified information and
software security professionals with
nearly 110,000 members worldwide, today
announced the honorees for its ninth
annual Asia-Pacific Information Security
Leadership Achievements (ISLATM)
Program. Mr. Frankie Leung, Director
of UDS Data Systems Ltd ,
recognized as Honoree for the Category
of Senior Information Security
Professional.
 |
 |
 |
"It is my pleasure to be recognized by (ISC)²® of my contribution on the IT Security industry", said by Frankie Leung, Program Director of ISC2 Hong Kong Chapter
(ISC)²® recognized 30 honorees and announce four showcased workforce initiatives as well as a community service star special recognition at a Gala Dinner and Ceremony on July 29, 2015 at Sofitel Philippine Plaza Manila, Philippines. Concurrently, (ISC)² Security Congress APAC, co-organized by National Defense College of the Philippines (NDCP), National Defense College of the Philippines Alumni Association, Inc. (NDCPAAI) and (ISC)², was held July 28-29 at the same venue.
The guest of honor, Vice President of the Philippines Hon. Jejomar C. Binay, together with (ISC)² executives, celebrated the workforce achievements of top information security professionals from Asia-Pacific.
"This year, we received high-quality nominations from over 10 economies throughout the Asia-Pacific region," said David Shearer, CISSP, PMP, CEO, (ISC)²® "The ISLA program provides a unique platform to showcase information security leaders who are dedicated to advancing the industry and inspiring the next generation of cyber security professionals. One unique factor that stood out in this year's pool of nominations was that almost all of the projects involved elements of voluntary community service. These professionals not only provided their expertise while performing their daily jobs under increasing pressure to secure our systems and infrastructure, they also gave back to their communities. I look forward to celebrating the achievements of this year's honorees with distinguished guests at the ceremony in Manila later this month."

Part of (ISC)²'s global Awards Program, Asia-Pacific ISLA aims to recognize the ongoing commitment by information security leaders in Asia-Pacific who have significantly enhanced the workforce by demonstrating a leadership role in an information security workforce improvement initiative, program or project. Professionals were nominated in three distinct categories: information security practitioner, managerial professional for an information security project, and senior information security professional.
The 2015 (ISC)² Asia-Pacific ISLA Nomination Review Committee is comprised of members of the (ISC)² Asia-Pacific Advisory Council and previous Asia-Pacific ISLA honorees. For details about the members of ISLA 2015 Nomination Review Committee, please visit https://www.isc2.org/asia-pacific-isla-nomination-review-committee/default.aspx.
2015.5.02 UDS enters the cloud market and joined Amazon Web Services partner network

The AWS Partner Network (APN) is the global partner program for AWS. It is focused on helping partners build a successful AWS-based business by providing great business, technical, marketing, and GTM support.
APN Consulting Partners are
professional services firms that help
customers of all sizes design,
architect, build, migrate, and manage
their workloads and applications on AWS.
Consulting Partners include System
Integrators (SIs), Strategic
Consultancies, Agencies, Managed Service
Providers (MSPs), and Value-Added
Resellers (VARs).
As an APN Consulting Partner
(registered), UDS will gain access to a
range of resources and training to
support our customers deploy, run,
and manage applications in the AWS
Cloud.
"UDS commits on AWS Partner Network
(APN). We believed we will upgrade
to AWS Standard Partner by the Q3 of
this year. We will have at least two AWS
Certificate Architects soon. We will
provide all consulting and implement
service in AWS", Mr. Frankie Leung,
Director of UDS Data systems said.
2014.11.10 UDS Data Systems represents Blancco Data erasure solution in Hong Kong and Macau
Blancco is the proven data erasure solution for millions of users around the world. As the pioneer and global leader in data sanitization and end-of-lifecycle solutions, the company offers the most certified data erasure within the industry.
| Secure erasure Blancco permanently removes data from IT assets such as PCs, servers, data center equipment and smartphones. Data erased by Blancco cannot be recovered with any existing technology. |

|
| Detailed
reporting A detailed report is proof of successful data erasure. Blancco’s tamper-proof and verifiable reporting is an essential part of compliance, regulatory and legal auditing requirements. |
 |
| Auditable
process A comprehensive audit trail is a critical requirement for compliance with IT security standards such as ISO27001, ISO15408, PCI and FISMA.  |
 |
2014.07.09
Mr.
Daniel Lai, Government CIO,
visited Splunk and SBox
booth at Information
Security Showcase 2014
Hong Kong Productivity Council (HKPC)
organized the Information Security
Showcase 2014 with the theme "Mobile
and Cloud Security in Today's Threat
Landscape" on 9 July 2014
(Wednesday) at the Hong Kong Convention
and Exhibition Centre. UDS and Splunk is
one of the sponsor organizations for
this great event. Mr. Paul Pang, Chief
Security Strategist of Splunk Inc,
conducted a Keynote speech of the topic
of “Battle Against Malware/APTs using
the Kill Chain Method & Splunk
Software”
 |
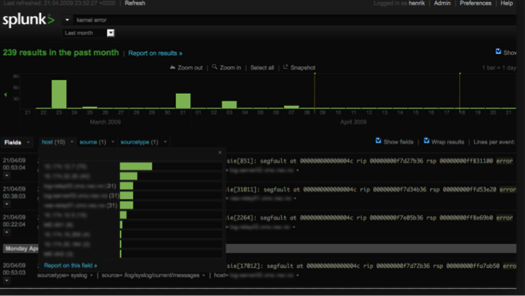 |
Mr. Daniel Lai, BBS, JP, Government
Chief Information Officer Office of the
Government Chief Information Officer ,
The Government of the Hong Kong SAR,
visit UDS managed booth at this event.
Mr. Daniel Lai discuss with our Mr. KL
To Business Consultant and Mr Steve Li
of Splunk Hong Kong for the Big Data
Software (Splunk) and Hardware (Sbox).
SBOX appliance is a converged big data computing platform that integrates high-performance storage, optimized operating system, and the Splunk machine data engine to provide enterprises with the most advanced and convenient data exploration solution. With an intuitive web user interface, SBOX appliance demonstrates fast installation and convenient management. SBOX appliance’s plug-and-play capability enables Splunk to be activated in just a few minutes, greatly reducing the time required for system setup. In addition, future upgrades or expansions with existing Splunk deployment can be completed in minimal time with the greatest simplicity.
 |
 |
2014.6.21 Public Awareness Seminar on WiFi Security

Organized by WITA Hong Kong Wireless Technology Industry Association (WTIA) and PISA (Hong Kong Professional Information Security Association), there is a Public Awareness Seminar on WiFi Security on June 21 of 2014.
Dr. Ken Fong, Immediate Past Chairman and Honorary Chairman (Life), WTIA and Mr. Alan Ho, Hon. Secretary & Treasurer , PISA are presenting the topic of “Hong Kong WiFi Security Survey 2013: Results and Implication”. They stated the past 12 years of this WiFi Security Survey in Hong Kong and set up the "Hong Kong WiFi Security Index". There are over 300 public attendances to join this event.
Mr. Frankie Leung, Program Director, PISA SIG, ISC2 Hong Kong Chapter, conducts a seminar of the topic of “The 123 of Wireless Security for Home and SOHO”. Frankie has introduced 11 methods to reduce the risk and increase the security of using Wifi in Home and SOHO environment.
Mr. Sang Young, Technical in charge, SafeWiFi Network Security Research Group do the “Onsite Demonstration: WPS (Wi-Fi Protected Setup) Cracking”. He uses a black box devices and cracks the WPS easily.
 |
 |
 |
 |
2014.5.20.
2014
Splunk APAC Summit - Break
Through at San Ya, Hainan,
China
Splunk are delighted to invite UDS Data
Systems Ltd to join her 2014 Splunk APAC
Summit, the 3rd Annual Splunk APAC
Partner event. This annual event
provided outstanding networking and
learning opportunities to enhance our
Splunk business. Mr. Frank Yip, Mr. KL
To and Mr. Ray Ho from UDS joined this
great event at San Ya, Hainan, China.
Highlights of this Summit
> Receive the latest information on Splunkproducts and solutions.
> Learn best practices, hear the latest success stories and be introduced to new sales tools to help you build a Customer Business Case for Splunk.
> Interact with Splunk's Senior Executives, Product Management and Marketing teams.
> Network with your peers in a relaxed, informal atmosphere.
> Learn about emerging trends in security, virtualization, compliance, big data, application management and more.
> Learn how to explain and demo Splunkproducts with our latest “Partner Demonstration Kit”.
> Enjoy a very special offer to re-certify your Splunk team to Splunk 6.0.
> Get in-depth, hands-on knowledge to help grow your business.
Mr. KL To, Mr. Ray Ho, Mr. Frank Yip |
Mr. Godfrey Sullivan Mr. Frank Yip and Mr. Dominic Mak |
Mr. Godfrey Sullivan: President, CEO and Chairman of Splunk |
Panel discussion on Security – Splunk ESS (Enterprise Security Suite) |
2014.4.14 SOTI joined Seminar on ‘Unleash the Money Power: e-Payment on Social Network and Mobiles’ @ICT Expo 2014
UDS joined Toppan Forms SecuWorld 2014 with Splunk, SBox, Safenet and HID Omnikey
Companies of all sizes collect and store huge volumes of confidential information while Information Security has evolved significantly and grown even more important in recent years. With the wave of new technology that is changing how you do business – cloud computing, the mobile workforce, smart devices that inevitably increase the risk of data exposed.
Toppan Forms (HK) Group announces its “SecuWorld 2014”. In this event, they show the latest advanced Information Security Solutions to the invited customers, such as Dual-Interface Card Security Solution, Digital Security Printing Solution & NFC Security Solution. The customers can explore the right enterprise security solutions for their business and help them to protect their most important asset and information.
Event Day : 16 May 2014 (Friday)
Venue : Level 7 (Ballroom), Langham Place Hotel Mongkok, 555 Shanghai St, Mongkok, Hong Kong
Event Time : 10:00am – 4:15pm
As the security valued added partner of Toppan Forms Computer, UDS teamed up our suppliers such as Splunk, Sbox Appliance, Safenet and HID Omnikey to set up a UDS booth to demonstrate their security solutions.
Splunk – Enterprise Security Suite
Sbox Appliance – The certificated appliance hardware to run the Splunk software
Safenet – OTP and PKI multi-factor authentication solution
HID Omnikey – Mifare, iClass and PKI Smart Card Reader
 |
 |
 |
 |

 |
 |
2014.5.5
Mr.
Frankie Leung was nominated
to be Fortinet Business
Partner Advisor

Over 12 years of sale experience of
Fortinet, Mr. Frankie Leung, Principal
Consultant of UDS Data Systems Ltd,
CISA, CISM, CISSP, CRISC, was nominated
as Fortinet Business Partner Advisor in
SEA and HK region.
The first Fortinet Business Partner
Advisory Council meeting was hold on 5
to 7 May of 2014 at Singapore
Top 3 topics nominated by our council
members were discussed during this
meeting
- How to increase your profitability and sales through Fortinet?
- What can Fortinet do to value add to your business?
- How can we drive greater market penetration for the other Fortinet products (excluding FortiGate)?
Fortinet Business Partner Advisory
Council is last for18 months and all the
Business Partner Advisors committed on
the participation to all related events
such as Tele-conference call,
Questionnaire, Business Partner Advisory
Council meeting and proposal the develop
a solution or the program on Fortinet
Partner.
After the meeting, Fortrinet accepted
the suggestion from the Advisory Council
that there are free trainings for the
authorized Partner and Partner just need
to purchase the exam coupon for FCNSA
& FCNSP

![]()
2014.4.14 SOTI joined Seminar on ‘Unleash the Money Power: e-Payment on Social Network and Mobiles’ @ICT Expo 2014
Mr. Calvin Chung, Managing Director,
APAC Region, SOTI, Inc was one of
the speakers of this event which was
organized by Wireless Technology
Industry Association (WTIA) Hong Kong in
ICT Expo 2014 at Hng Kong. Mr Calvin
Chung covered the topic of “Turning
Mobile Tablet into PCI Compliant mPOS”.
As the Gold Sponsor of this event, SOTI
joined with UDS Data Systems Ltd to have
an exhibition booth @ICT Expo 2014 at
Hong Kong Convention and
Exhibition Centre.
SOTI and UDS demonstrated SITO
flagship product, SOTI’s MobiControl.
With over 12,000 enterprise deployments
and millions of devices managed
globally, SOTI’s MobiControl is the
world’s most trusted Mobile Device
Management (MDM) and Bring Your Own
Device (BYOD) Management solution.
MobiControl enables organizations to
centrally manage, support, secure and
track corporate-liable and
employee-liable mobile devices,
regardless of device type, mobile
platform and location.
SOTI Inc. develops world leading
technology that solves the unique
challenges involved in managing,
securing, supporting & tracking
remote mobile & desktop computing
devices. SOTI products currently
support devices running Windows desktop
and handheld operating systems,
BlackBerry OS, Apple iOS and Google
Android.
SOTI works closely with top mobile
device manufacturers such as: Samsung,
Microsoft, Intermec, Honeywell, RIM,
Motorola, Aruba, Bluebird, Panasonic,
ZTE, LG, etc. SOTI’s world-class remote
technology is second to none & is
licensed by top mobile device hardware
& software brands.
MobiControl Key Features:
2014.4.4
UDS
Security Consultants won
Symantec Cyber Readiness
Challenge (Hong Kong)

The Symantec Cyber Readiness Challenge
is a competition designed for all levels
of technical expertise that puts
participants in the hacker's shoes to
understand their targets, technology and
thought processes so they can ultimately
better protect their company or agency.
This interactive 'capture the flag'
style competition will take place at
various locations around the globe and
participants will have the opportunity
to test their skills within a unique and
real world environment developed by
Symantec, the global leader in security.
- Expand your security awareness
- Implement theoretical knowledge
- Compete against your peers
Bringing together some of the world's
leading experts in IT security, this
innovative competition will offer a
keynote presentation on the current
security landscape by renowned security
experts and provides a fantastic
environment for networking and knowledge
sharing.
Symantec provided an assimilated real
world data center environment within
which Participants can participate and
compete in the Challenge. The Challenge
consists of a series of IT security
related challenges or tasks based on a
difficulty level according to low,
medium, and high.
During the Challenge, Participants
must use their own laptops or notebook
computers for participation in the
Challenge. Three of Security
Consultants from UDS Data Systems Ltd
joined this event and they all are
very familiar with the most popular
Vulnerability Assessment and
Penetration Testing (VAPT) tools such
as Backtrack, HP Fortify, Rapid7
Nexpose and Metasploit and Tenable
Nessus Vulnerability Scanner. UDS also
offers the VAPT, security assessment,
privacy impact analysis and security
awareness training to the enterprise,
education and government sector.




Finally, Mr. Sam Soo (Security
Consultant, UDS Data Systems Ltd) is the
1st place with total highest points. He
won a prize of a Olympus
interchangeable lens system camera
(OM-D E-M10) kit set with a
40-150mm lens (1 pc) and a 14-40mm Lens
(1 pc) and Mr. Paul Chow (Application
Developer,
UDS Data Systems Ltd) is 2nd place with
total the 2nd highest points and he won
a prize of a Mini with Retina Display (1
pc).


2014.4.9
Safenet APAC Partner
Summit at Yilan, Taiwan

“Be Extraordinary” is the frame of this year Safenet APAC Partner Summit. Mr Frankie Leung (CISA, CISM, CRISC and CISSP) was on behalf of UDS Data Systems Ltd to participate this great event in YiLan, Taiwan. Mr Frankie Leung also met the senior management of Safenet such as Mr. Phil Saunders (Executive Vice President and Chief Revenue Officer), Mr Prakash Panjwani (SVP and GM, Data Protection Solutions) and Rana Gupta, Vice President, Asia Pacific
Safenet shared its roadmap for data and application security, and new trends in cloud computing and mobility with more than 100 APAC partners.
Mr Frankie Leung also was invited to be one of the speakers in the Executive Panel Discussion happening on 10th Apr, 10:40 am – 11.55 am. The panel discussion, moderated by Phil Saunders, (EVP, Worldwide Sales & Services) gathered our fellow peers to discuss and exchange views on the following topics:
1. Market trends by each country
- Cloud, Big Data, Social, BYOD, Secure POS, Mobile Payment, new fast (or real time) fund transfer system, eGovernment, etc.
2. Opportunities finding
- In which area are you finding opportunities of your business in such market trend?
- Where are the opportunities for security vendors (especially authentication and encryption) in the mentioned market trend?
3. Demand for Security
- What are the drivers for the mentioned security needs (PCIDSS, regulation in each country, security incident report, etc.)?
- How can we work together to capture these opportunities?
4. How would you position your partnership with SafeNet for more opportunities to create a win-win situation?
Mr. Frankie Leung expressed his experience on data security and the current situations of Hong Kong market. He is fully supporting the slogan of Safenet of “The Year of Encryption”. Finally, Frankie Leung conclude in the panel discussion that Encryption is the key to protect your data and security education and awareness is main methods to enforce your security policies.


The theme of this year InfoSecurity Summit is "Threats and Opportunities Growing in Cybersecurity". UDS Data Systems Ltd teamed up with Splunk and Vormetric to participate this great event.
Mr Paul Pang, Chief Security Strategist of Spunk, Inc is a speaker of the topic of “Using Big Data Analytics To Improve Security And Compliance”. Many heads of Security Services struggled with an underperforming traditional SIEM to keep the organization both secure and compliant. Learn how Splunk turned to a big data analytical approach to SIEM to more effectively perform incident investigations, uncover known and unknown threats, and create the reports and evidence required by auditors.
UDS also shows the Vormetric solution in this summit. Vormetric addresses industry compliance mandates and government regulations globally by securing data in physical, virtual and cloud infrastructures, through: Data Encryption, Key Management, Access Policies, Privileged User Control, and Security Intelligence.
 |
 |
 |
 |
Vormetric solutions put the safeguards and access controls for your critical data with your data. A data firewall for protected information is the result - wherever it resides in the technology stack – across physical, virtual, big data and cloud environments. Core capabilities protect structured data in databases as well as unstructured file system data with encryption and access controls that meet and exceed regulatory requirements and help to prevent data breaches.
Vormetric Cloud Security capabilities enable your organization to safely and securely protect data in cloud environments with appropriate security policies and control
Vormetric Data Protection Compliance Solutions provide the controls required to meet regulatory requirements for safeguarding data under PCI DSS, SOX, Gramm Leach Bliley, HIPAA HITECH and other industry and government compliance and data privacy initiatives.
Vormetric Application Solutions address the unique data security and compliance challenges specific to Network Attach Storage (NAS) devices, SAP implementations and virtual environments
Vormetric Industry specific solutions specifically address the data protection needs of organizations in education, federal and local government, financial services, healthcare, outsourcing, managed service providers and cloud services
Vormetric products provide the underpinnings of these compelling solutions - securing the data inside your organization, enabling regulatory compliance, and providing simple, effective solution management as well as security intelligence.
Vormetric Encryption – A single, manageable and scalable solution to encrypt any file, any database, any application’s data, anywhere it resides— without sacrificing application performance or creating key management complexity. And with access control that protects from root, administrative, DBA or rogue applications.
Vormetric Key Management – Focused on critical encryption key management – Transparent Data Encryption (TDE) – for Oracle and Microsoft SQL Server databases
Vormetric Vault – Provides a simple, secure solution to the problem of managing certificates, and protecting encryption keys as well as other security objects with expiration alerts, reports and secure storage and inventory.
2014.3.20
UDS
launches its SG ProtectedDisk
To provide the continuous support for existing users in Greater China region, UDS entered an agreement with Sophos to develop UDS version of SG ProtectedDisk in September of 2013, which is based on Sophos SafeGuard PrivateDisk technology.
UDS SG ProtectedDisk was launched in Sophos 2014 partner dinner in Hong Kong. Mr Frankie Leung, (Director of UDS, CISA, CISM, CRISC, CISSP) did a short presentation of the new features and functions of UDS SG ProtectedDisk and its road map.
UDS is taking up all supports for any valid Sophos SGPD software maintenance contracts after April 1 of 2014 for HK, China and Taiwan users
For technical support on SG ProtectedDisk and Sophos PrivateDisk, you can send an email to sophos-sgpd@udshk.com, including your product name, software version, operation system(s) and patch level(s), and the text of any error message, or contact UDS support hotline
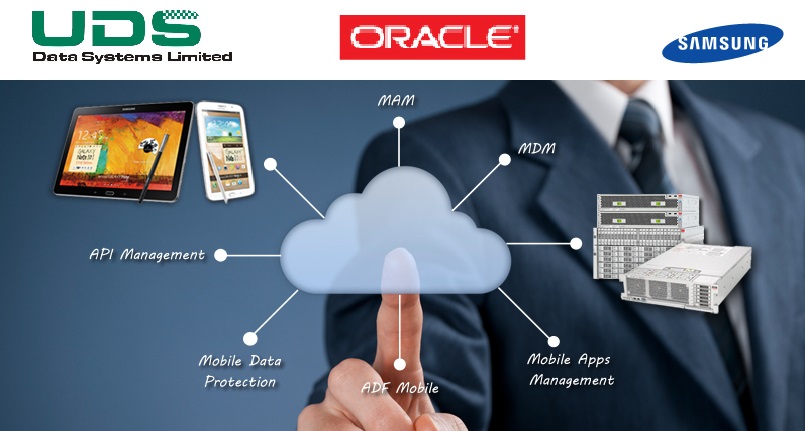
 |
2014.1.15 UDS shows Splunk at “Big Data Analytics - A New Way To Enhance Data Analysis in Your Business' Seminar” at OGCIO
As the Splunk distributor in Hong Kong, UDS submitted the request for proposal to OGCIO and partnered with Splunk for this event. Our presentation title is “Turn Machine-generated Data into Real-time Business Insights – Splunk for Big Data”
OGCIO (Office of Government CIO) were delighted to inform us that UDS Dafa Systems Ltd has been selected to participate in the captioned event on 9 Jan 2014 (Friday) at OGCIO Cyberport office: Level 5, Cyberport 1, 100 Cyberport Road, Hong Kong.
There were totally 76 registrations from 21 B/Ds in this event including Hong Kong Police Force, OGCIO, Water Supplies Department, Fire Services Department, and other B/Ds. (AFCD, SWD, PLAND, SB, LCSD, Audit, DEVB, FHB, etc)
 |
 |
 |
 |
 |
 |
2013.12.23 Splunk 6 Meets Splunkers and Partners at Xperience
Don't forget the Splunk is now the 6th generation. Introduction event of Splunk 6 was hold on December 10th at Xperience! Splunks’ users, Splunks’ sfaff, Splunks’ architects and Splunks’ partners were together to share ideas and learn from one other.
It was the first official event for Splunk 6. Whether you were getting started, creating intelligent searches and alerts or building complex dashboards, this group is for you. Meet other Splunkers and get tips you own need to be more successful.
VENUE
Xperience
G/F., Asia Orient Tower, 33 Lockhart Road, Wanchai
WHEN
Tuesday, December 10th 4:30pm - 6:30pm
AGENDA
What's New inSplunk 6.0? Paul Pang, Technical Director
Open Forum All Splunkers
 |
 |
 |
 |
2013.12.13 (ISC)2 Hong Kong Chapter 2013/2014 Committee Members were elected
(ISC)2 Hong Kong Chapter was found in Nov of 2012 and it is running under the SIG of PISA Hong Kong. PISA (Professional Information Security Association) is a not-for-profit organization for local information security professionals. We focus on developing the local information security market with a global presence in the industry.
The new committee members are
Andy Ho (President)
Alan Ho (Treasurer)
Billy Pang (Professional Development)
Frank Chow (Liaison)
Frankie Leung (Program Director)
Jim Shek (Program Director)
Joyce Fan (Secretary)
Otto Lee (Membership Chair)
Mr. Frankie Leung (CISSP, CISA, CISM, CRIS), Our Business Manager, was elected as Program Director of (ISC)2 Hong Kong Chapter 2013/2014. In the past 10 years, Mr. Frankie Leung was invited by different parties as the speaker to conduct the information security related topics for public in different events. Those organizations are including OGCIO, WTIA, The Hong Kong Council of Social Service, SafeWiFi, Keep Hong Society, Tung Wah Group, some primary schools. Mr. Frankie Leung is also a Hong Kong Safe & Secure Online Volunteers which is organized by ISC2 to promote the internet security awareness to the public.

2013.10.30 UDS and Splunk joined The Information Security Summit 2013
The frame of this year The Information Security Summit 2013 is "Trust and Privacy in the Cyber Era 2.0 - Securing and Protecting Borderless Data"

The Information Security Summit 2013 is a Regional Event with the aim to give participants from the Asia Pacific region an update on the latest development, trends and status in information security. Following the success of the event organized in the previous ten years, this year’s Summit includes a one-day conference and a number of workshops demonstrating management and technology knowledge, applications and practical experiences on all aspects of information security relating to securing and protecting data in borderless cloud and mobile environment.
Mr. Paul Pang, Technical Director, Asia Pacific & Japan of Splunk Inc. presented the topic of Security Intelligence with Big Data.


Analysis of machine-generated data can play an important role in a sophisticated layered defense for your data and systems, but getting there can be challenging even with advanced intelligence platforms. Data is flowing from all sources within your organization and from outside the organization. But finding ways to harness, monitor and extract key insight real time from that data has always proved a massive challenge. In this session, you'll learn how Splunk can make it easy to collect, index, search, correlate and report on all security-related events across your entire infrastructure in real time.
As the distributor of Splunk in Hong Kong and Macau, UDS demonstrated Splunk software and SBOX in this great event. SBOX is an appliance to provide state of the art turnkey solution to your analytics needs as it is integrated and pre-configured with the lightweight OS and other management tools and Splunk application.

2013.10.15 UDS and Splunk joined Asia Digital Analytics Summit at InterContinental Grand Stanford on 11th October 2013
This year Asia Digital Analytics Summit 2013 (http://www.digitalanalytics.asia) once again brought all the professionals together in Hong Kong on the 11th October 2013. There were 2 tracks this year in order to cover both technology as well as the business side of data analytics.


2013.6.4 UDS met Sophos mangement team at Sopho Partner Connections on May 9 of 2013
Kris Hagerman, Chief Executive Officer, Gerhard Eschelbeck, Chief Technology Officer and Guenter Junk, Senior Vice President and General Manager, Network Security Group invited Frankie Leung (UDS Data Systems Ltd, Director) to Sophos Partner Connections – An Exclusive invite to Asia Executive Panel Luncheon at Movenpick Hotel. The Executive Panel Session is an open forum and our invited partners can express their concerns and ask the questions in this meeting.
Beside on the The Executive Panel Session, this year Sopho Partner Connect also covers
• Sophos company and channel strategy
• Selling against the competition and cross-selling techniques
• Making the most of the Sophos Partner Program
• Many opportunities to connect Sophos sales and your peers
• Technical demonstrations and workshops
In the award dinner, Timothy Liu (Regional Director of Sophos) announced that UDS Data Systems Ltd is the winner of the "Partner of the Year" award. Mr Frankie Leung said that "It is the best conference I have never been. It is not because we get the award. We see a good team, good products and good hospitalization here. Sophos is our top ranking vendor."
2013.3.25 UDS participated the Splunk APAC Best Apps Contest in Splunk APAC Partner Kick Off 2013 at Bali Conrad

USD has prepared a Splunk Apps “
Firewall Optimizer” based on
Fortinet Fortigate UTM appliance
with the following functionality.
· Correlation with Active Directory to
identify the user activities i.e.
Internet web sites visiting
· Fund out most active Firewall policies
· Fund out Least active Firewall
policies
· Identify never use Firewall policy
with zero hit rate
· Prioritize Firewall policy
There will be 2 rounds in the selection
process:
· Round 1 – Open Voting by all
conference delegate
· Round 2 – Scoring by Splunk
Selection Committee
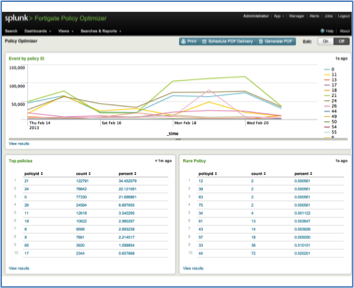
- Splunk Firewall Application Architecture - Splunk Firewall Application Report.
 Mr. Godfrey R. Sullivan (Chairman and Chief Executive Officer of Splunk) visited our booth and took a photo with Mr. Frankie Leung. Godfrey is one of the Splunk Selection Committee in the Splunk APAC Best Apps Contest. We also shared the functionality of these “Firewall Optimizer” apps to Godfrey and got his feedback. |


 Duration
the 6 days Splunk Partner Kick
Off (PKO) in Bali, UDS Data
Systems Ltd has passed the
following Splunks' "It Pays to
be Certified!" program
including Splunk Certificated
Sales (4 persons),
Splunk Certificated
Sales Engineer (3 persons) and
Splunk
Certificated Architect (3
persons),
Splunk
Certificated Architect
is a 24 hours Lab exam that
who must pass "Splunk
Certificated Sales" first.
Right now, UDS has three
Splunk
Certificated Architect
and will be have totally 6
soon.
|
2013.2.25 IBM InfoSphere Guardium Database Security solutions
IBM InfoSphere Guardium Database Security solutions
Monitor Data Activity in Real Time
Identify unauthorized or suspicious activities by continuously monitoring access to databases, data warehouses, Hadoop systems and file share platforms in real-time.
Audit and Validate Compliance
Simplify SOX, PCI-DSS, and Data Privacy processes with pre-configured reports and automated oversight workflows (electronic sign-offs, escalations, etc.) to satisfy mandates.
Secure and Protect Big Data Environments
Build security into big data environments to prevent breaches, ensure data integrity and satisfy compliance.
Protect Data Privacy
Develop a holistic approach to data protection to ensure compliance and reduce costs.
Assess Vulnerabilities
Scan the entire data infrastructure for vulnerabilities and receive an ongoing evaluation of your data security posture, using both real-time and historical data.
Safeguard both Structured and Unstructured Data
Ensure structured and unstructured data is identified, transformed and audited.
Protect and Secure Data in the Cloud and Virtual environments
Providing comprehensive data protection for cloud, virtual and physical infrastructures.
UDS Data Systems Ltd is now carrying IBM InfoSphere Guardium solutions and we offer pre-sale, post-sale and implementation services for the customers in Hong Kong and Macau.
2013.2.25 Splunk launches Splunk App for VMware
Comprehensive cross-tier
operational visibility across your
virtualized environment


Real-time Operational Insights
.Browse ESX/i hosts and VC logs with intelligent filtering using a built-in log browser. Alert on abnormalities to proactively manage issues
Topology Maps for Comprehensive Visibility
Monitor health of individual nodes based on pre-defined thresholds. Use interactive topology views to find and fix problems. Get detailed reports based on the 20-second granular metrics for deep-dive diagnostics and long-term trending and analytics.
Security Insights on Virtual Assets
Actively manage suspicious user activity, potential attacks and changes to users and ESX/i hosts with an out-of-the-box security report. Ensure appropriate controls are implemented with insights into user access and activity within the virtual infrastructure
Change Tracking and Asset Reporting
Audit changes to the environment, users and roles and ascertain the scope and impact of changes that could negatively impact availability, performance, security and capacity. Keep up to date on virtual assets and track the status of assets within the dynamic VMware environment in real time.
UDS Data Systems Ltd is the first Splunk Service provider in Hong Kong. With our splunk certificated consultant, we provides the customization service for any systems, network devices and security appliance and co-related all the logs into a real time alerts and dashboard for you to drill down to find the real cause.
2013.1.2 UDS carries Netwrix
UDS carries Netwrix
NetWrix Corporation’s core competency is in unifying change and configuration auditing of critical systems across the entire IT infrastructure. With the broadest platform coverage available in the industry, innovative technology and strategic roadmap aiming to support different platforms, devices and applications, NetWrix offers award-winning auditing solutions and superior customer service at affordable prices. Founded in 2006, NetWrix has evolved as #1 for Change Auditing as evidenced by thousands of satisfied customers worldwide. The company is headquartered in Irvine, CA, and has regional offices in Paramus, Boston, Tampa and the UK. NetWrix is #33 among the fastest growing software companies in America according to Inc. 500 list published by Inc. Magazine in 2012.

Vulnerability Management
Solution Integrates Configuration
Assessment, Enhances Reporting and
Introduces Virtual Appliance
Deployment
Know your security
risk of your entire IT environment including
networks, operating systems, web
applications and databases.
Expose security
threats including
vulnerabilities,
misconfigurations
and malware.
Prioritize threats and get specific
remediation guidance for each issue.
Integrates with
Metasploit to validate security
risk in your environment
“As organizations
go forward in an ever more dangerous IT
environment, it is imperative that they
have knowledge of the threats,
vulnerabilities, and overall risk to
their environment. Vulnerability
assessment is a critical step in this
and not only improves an organization’s
overall security, but can reduce costs
and make a company more competitive,”
said Charles Kolodgy, vice president of
research for Secure Products at IDC.
“Capabilities such as integrated
configuration assessment and enhanced
reporting make security smarter and
helps prioritize action and investment.”
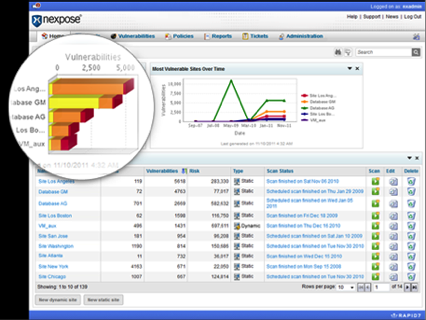
The new enhancements
to Nexpose 5.5 include:
Configuration
Assessment
Organizations need to
ensure they are complying with various
policy standards, whether they are
internal best practice standards, or
from external regulatory bodies such as
the National Institute of Standards and
Technology (NIST). A part of this is
ensuring their IT assets are configured
in the right way. Traditionally, policy
and compliance evaluation are done
separately from vulnerability
assessments, decreasing productivity for
organizations that have to go through
similar processes more than once.
Version 5.5 extends Nexpose’s existing
integrated configuration assessment
capabilities by adding CIS Benchmarks,
enabling security professionals to
benefit from the increased efficiency of
unified discovery, scanning, reporting
and management.
Enhanced Reporting
Identifying areas of
potential risk is crucial, and it is
equally vital that the information
around risk is presented in a way that
is easy to understand and actionable, so
the organization can move forward and
act to minimize risk. This has
traditionally resulted in security
professionals spending a large amount of
time on reporting, frequently without
the real desired outcome of identifying
whether the organization’s security
posture is improving. Nexpose 5.5
addresses this, providing a simplified
reporting workflow that enables users to
create customized reports that put the
information they need in their hands.
Users can also benefit from pre-made
templates out-of-the-box, as well as
community-driven reports distributed
through Rapid7’s community site.
Deployment as a
Virtual Appliance
Rapid7 is committed
to providing flexibility so customers
can deploy Nexpose in whatever means
best suits their environment and needs.
The solution is already available on a
physical appliance, a hosted SaaS
solution, or as downloaded software.
With the release of the latest version,
users will also be able to deploy it as
a virtual appliance later this month.
This enables security professionals to
quickly and easily deploy Nexpose in
their virtual environment.
About Rapid7
Rapid7 is the leading
provider of security risk intelligence.
Its integrated vulnerability management
and penetration testing products,
Nexpose and Metasploit, and mobile risk
management solution, Mobilisafe, empower
organizations to obtain accurate,
actionable and contextual intelligence
into their threat and risk posture.
Rapid7's solutions are used by more than
2,000 enterprises and government
agencies in more than 65 countries,
while the Company's free products are
downloaded more than one million times
per year and enhanced by the more than
175,000 members of its open source
security community. Rapid7 has been
recognized as one of the fastest growing
security companies by Inc. Magazine and
as a "Top Place to Work" by the Boston
Globe. Its products are top rated by
Gartner®, Forrester® and SC Magazine.
The Company is backed by Bain Capital
Ventures and Technology Crossover
Ventures. For more information about
Rapid7, please visit
http://www.rapid7.com.
- 2012.11 5-9 Fortinet’s Global Partner Conference 2012

 Mr.
Frankie
Leung and Mr. Vinton Yau represented UDS
to join this great event. Fortinet
Strategy & Vision was presented by
Fortinet CEO and founder, Mr. Ken Xie.
And the most Powerful Security Operating
System: FortiOS 5 was also covered. “It
is a fantastic event that I have never
been among all the partnert confernece.
It is the third times we met Mr. Ken Xie
and shared our experience and
expectations on selling Fortinet
products “. Frankie Leung said.
Mr.
Frankie
Leung and Mr. Vinton Yau represented UDS
to join this great event. Fortinet
Strategy & Vision was presented by
Fortinet CEO and founder, Mr. Ken Xie.
And the most Powerful Security Operating
System: FortiOS 5 was also covered. “It
is a fantastic event that I have never
been among all the partnert confernece.
It is the third times we met Mr. Ken Xie
and shared our experience and
expectations on selling Fortinet
products “. Frankie Leung said.
2012.8.10 BlueCat IPAM and IPv6 migration studies


On 8th of August 2012, Mr. Richard
Hyatt, CTO and Co-Founder of BlueCat
Networks, have a meeting with
JUCC/NTF (Join University Computer
Centre/Network Task Force) members to
share IPAM and IPv6 migration strategies
and methodologies in the meeting.
His visionary approach to leading the
company’s product development efforts
has made him a globally recognized
expert in IP Address Management (IPAM),
IPv6 and DNS security extensions
(DNSSEC), key network technologies that
are critical to BYOD, virtualization and
cloud. As a testament to Richard’s
innovative designs and customer-centric
approach, BlueCat Networks has routinely
been recognized as a market leader by
Gartner and Forrester Research and has
achieved double and triple-figure
growth.
During the meeting, Richard had shared
IPAM, IPv6 migration strategies and
methodologies as well as real cases
regarding IPAM and IPv6 migration in the
globe.
UDS
IPv6 expert team, provides service on
University scope.
Teaming up with BlueCat local
distributor - Data World Computer &
Communication Ltd, UDS Data Systems Ltd
is the authorised BlueCat partner to
serve the high education section as well
as large enterprises.
Joint Universities Computer Centre
(JUCC) is a cooperative effort of the
Computer Centres of the eight
government-funded tertiary institutions
in Hong Kong.
 The
member
institutions are:
The
member
institutions are:
• The University of Hong Kong-
• The
Chinese University of Hong Kong
• The Hong Kong Polytechnic University -
• City
University of Hong Kong
• Hong Kong Baptist University - • The Hong Kong University of Science and Technology
- • Lingnan University
• The Open University of Hong Kong
• Vocational Training Council
Mr. Richard Hyatt, CTO and Co-Founder of BlueCat Networks (right)
and Mr. Vinton Yin, Sales Director of UDS (left).
BlueCat Networks provides businesses with the most feature-rich and future-ready DNS, DHCP and IP Address Management (IPAM) software solutions available on the market. Through fearless product innovation and a maniacal focus on providing the industry's best services and technical support, we deliver smart, simple, scalable DNS, DHCP and IPAM solutions that empower businesses to reduce IT costs, launch new IP-dependent services faster and manage network growth and change.
- 2012.7 - 2012 Sophos AP Partner Conference

 The conference
theme this year is Leading with Complete
Security. Sophos Complete Security Suites
offerings give our partners a competitive
edge in the industry—one vendor, one
license, ease of management and
deployment. And the array of
market-leading solutions creates even more
secure environments for our customers at a
greater value.
The conference
theme this year is Leading with Complete
Security. Sophos Complete Security Suites
offerings give our partners a competitive
edge in the industry—one vendor, one
license, ease of management and
deployment. And the array of
market-leading solutions creates even more
secure environments for our customers at a
greater value.Sophos APAC Partner Conference 2012 provided insight into:
- - Selling against the competition and cross-selling techniques
- - Making the most of the Sophos Partner Program
- - Many opportunities to connect Sophos sales and peers
Chief Executive Officer of Sophos Ltd at 2012 Sophos AP
Partner Conference at Pattaya, Thailand.
Sophos is focused on delivering the best IT security and data protection for businesses. They produced our first encryption and antivirus products back in the 1980s. And today our products protect over 100,000 businesses and 100 million users, in more than 150 countries. Both Sophos and UDS understand what it takes to keep your business secure — that’s why we’re recognized by analysts and customers alike as leaders in what we do.
2012.3 - SOTI MobiControl for Samsung Android Device
SOTI MobiControl enables enterprise mobility! With the most comprehensive feature set on the market, MobiControl ensures both corporate and personally owned Samsung Android devices are secured, tracked, configured, and supported over the air in one multiplatform solution. Optimize ROI and confidently welcome the latest Samsung Android smartphones and tablets into the workplace.
SOTI MobiControl has the following two unique features for Samsung Android devices:
Device Feature Control MobiControl features the ability to selectively enable or disable native Samsung Android device features.
-
- Android Market
- Camera
- Data Usage while Roaming
- WiFi
- Bluetooth
- Microphone
- Access Point
- MS Exchange Email
Configurable LockDown Policies allow administrators to block use of the operating system and replace the device home screen with a customizable screen that limits users to select applications only. The lockdown feature decreases downtime and minimizes unauthorized use of corporate devices.
About SOTI Inc.
SOTI Inc. develops industry-leading technology that solves the unique challenges involved in managing, securing, supporting, and tracking remote mobile and desktop computing devices. Today, over 80,000 customers around the world in retail, manufacturing, health care, government, logistics and other industries rely on SOTI products to reduce the total cost of ownership associated with their mobile devices.
- 2012.2 - Aerohive Networks Receives 2011 Cloud Computing Excellence Award
Aerohive
BR100
Router Honored for Innovation
-

▪ Layer 3 IPSec VPN
▪ Wired/Wireless Access and Control
▪ Cloud Proxy
▪ Network Flow-based Stateful Firewall
▪ Network-as-a-Service Offering
▪ 1x1 Single Band 802.11b/g/n
▪ 2x embedded antenna with diversity function
Sunnyvale, Calif. — February 7, 2012
— Aerohive Networks, the
pioneer in cloud-enabled enterprise
networking
infrastructure, announced today
that TMC, a global, integrated
media company, has named
Aerohive’s BR100 Router as a
2011 Cloud Computing Excellence Award
winner presented by Cloud Computing
Magazine in January, 2012.

News
Facts
- Cloud Computing Magazine is the industry’s definitive source for all things cloud – from public, community, hybrid and private cloud to security and business continuity, and everything in between. The term cloud computing goes beyond VoIP, software-as-a-service (SaaS) or Unified Communications – it’s an entirely new way to build, deploy and scale enterprise communications systems.
The Cloud Computing Excellence Awards recognized the companies that have most effectively leveraged cloud computing in their efforts to bring new, differentiated offerings to market.
Winners of the Cloud Computing Excellence Award are published in the January 2012 issue of Cloud Computing Magazine.
Aerohive’s Branch on Demand™ - a Network-as-a-Service (NaaS) solution purpose-built for small branches, teleworkers and temporary enterprise networks, was introduced on November 15, 2011.
Ideal for mid-market and commercial enterprises with highly distributed employees,Branch on Demand™ is the first branch office solution to offer wired/wireless access, performance and security management, 3G/4G WAN connectivity options,as well as routing and VPN as an on-demand service starting at $99 US list per branch per year.
Comments
“Aerohive Networks has been recognized
for their achievement in bringing
innovation and excellence in the market
while leveraging the latest technology
trends to create an enriched user
experience,” said Erik Linask,
Group Editorial Director, TMC.
“We are honored to have received a Cloud
Computing Magazine’s Excellence Award,
for our innovative Branch on Demand
solution,” said Stephen Philip, VP of
Marketing, Aerohive Networks. “Our
cloud-enabled approach for distributed
enterprises has been well received by
the marketplace with many organizations
seeking secure, affordable networking
alternatives for small branches,
teleworkers or temporary networks.”
- 2012.1 - RSA Channel partner

- We are pleased to announce that UDS
Data Systems Ltd is accredited as a
RSA Channel partner. We are pleased to
offer to our clients security solution
from RSA with particular focus in the
solution evolve around RSA NetWitness.
RSA NetWitness is a unique solution that allows you to capture, store and analysis network data traffic and be able to see exactly what comes in and goes of the network, in real time and as they happen. In simple term, RSA offers to you a Network CCTV. Not only that, NetWitness allows you to see the traffic in action as it reconstructs the data that flow through the network into its original format according to its own type or application. So you can further strengthening your security measures by taking appropriate action. On top of that, since all traffic is captured and stored, you will be able to go back to a particular period of time and conduct historical data analysis. Nothing could escape undetected.
NetWitness, Knows Everything, Answers Anything! 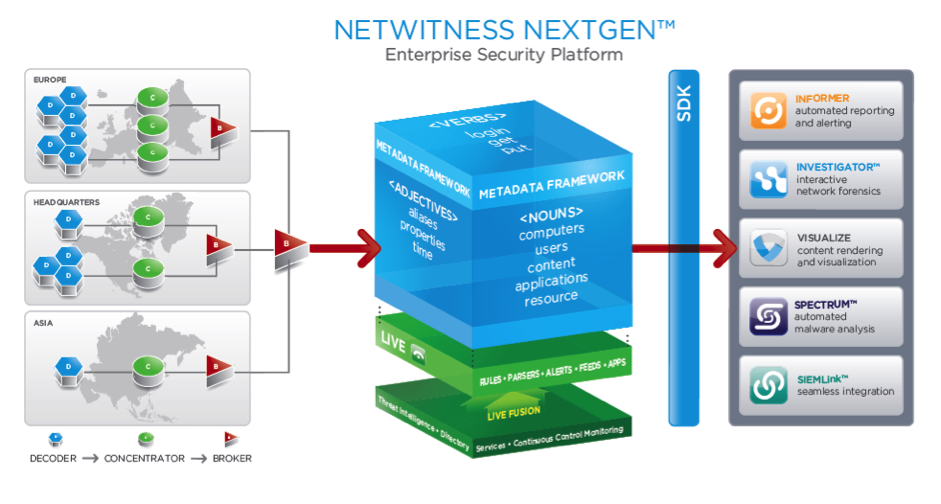
- RSA NetWitness Panorama delivers an
innovative fusion of hundreds of log
data sources with external threat
intelligence to enterprises enabling
extraordinarily broad and high-speed
visibility into the critical
information needed to help detect
targeted, dynamic and stealthy attack
techniques.
Panorama enables comprehensive security event collection as an integrated component of the award-winning NetWitness platform. Panorama offers correlation and analysis of the large volumes of network and system data needed for effective threat detection.
For more information how NetWitNess to help you to deal with the challenges, please feel free to contact us, our security consultants are more than happy to serve you.
- 2011.11 - "Novell Best of BrainShare" in Yangshuo.


On behalf of UDS Data Systems Ltd, Mr Frankie Leung (Business Manager, CISSP, CISA, CISM, CRISC) was invited by Novell to their "Brainshare" event in Guilin, Guang Xi, China. On November 17, 2011, Novell hold the annual “Novell Best of BrainShare” in Yangshuo Resort Hotel known as a land of idyllic beauty. By then, Novell shared the most effective and stable Cloud architecture along with the latest cloud safety technology and its global cases . And Novell also shared the remarkable results of Novell in 2011, also the development tendency and new policies of channels in 2012 with us.
-
In this April, Novell, the leading enterprise software provider in the world, joined Attachmate Group. As one of the top ten software manufacturers, Attachmate devotes itself to continuous exploration and persistent development and innovation, and provides clients with high-performance, high-applicability and high-safety enterprise solutions, so as to expand, manage and guard the more complex IT environment. Being a member of Attachmate Group, Novell will start its new journey with the strong support of Attachmate. From now on, Novell will pay more attention to assisting the enterprises in safely providing and managing the computing services in physical, virtual and cloud environment. The clients can reduce their cost, complexity and risk of IT system through Novell’s solutions including identity authentication, system management, cooperation and service platform based on Linux. Also, Novell will place emphasis on the demands of clients and interest of partners and create more value for more enterprises with the win-win and multi-win principle.
- 2011.06 - Aerohive Cloud-Enabled, Distributed-Intelligence Wi-Fi.

UDS is proudly introducing the next generation Wi-Fi Solution from US – the Aerohive Cloud-Enabled, Distributed-Intelligence Wi-Fi.
Aerohive Networks reduces the cost and complexity of today’s networks with cloud-enabled, distributed Wi-Fi and routing solutions for enterprises and medium sized companies including branch offices and teleworkers. Aerohive’s award-winning cooperative control Wi-Fi architecture, public or private cloud-enabled network management, routing and VPN solutions eliminate costly controllers and single points of failure. This gives its customers mission critical reliability with granular security and policy enforcement and the ability to start small and expand without limitations.-
Enterprise Network Access Points and Cloud-enabled Management
Today’s enterprises are looking to increase productivity, reduce capital and operational costs, and streamline their wireless infrastructures. Aerohive helps simplify complex networking by reducing the cost and complexity of today’s networks with cloud-enabled, distributed intelligence-based, Wi-Fi solutions.
Access Points without requiring a Controller
Aerohive’s 802.11n enterprise wireless LAN access points, HiveAPs, are an innovative class of wireless infrastructure equipment with cooperative control technology that provides the benefits of a controller-based wireless LAN solution, without requiring a controller or an overlay network.
Software & Management
Aerohive’s HiveOS is the operating system that powers the Aerohive access points, while HiveManager is the wireless network management system for configuration and monitoring. Together, with Aerohive access points, these comprise a complete controller-less Wi-Fi solution.
- 2011.03 - LANDesk Greater China Channel Partner at Xiamen, China.

Mr. Frankie Leung represented UDS Data Systems Ltd to join this great event. More than 50 LANDesk ESP from Mainland China, Taiwan and Hong Kong attend this event.
Mr. Frankie Leung also meet the Mr. Andy Ruse, VP of Asia Operation, and senior management of LANDesk Greater China team to discuss the product development, marketing and technical support issues.
- 2011.01 - SafeNet APAC Channel Partners Conference 2011 in Macau.

Mr. Leo Fu (Security Consultant) and Mr. Keith Lam (Security Consultant) participated in the SafeNet APAC Channel Partners Conference 2011 in Macau.
In this conference, Safenet covered the state-of-art security solutions on Cloud computing, HSM, Tokenizatio, DataSecure platform. Also, the new renamed TMS, Safenet Authentication Manager 8.0 (SAM) and Safenet Authentication Client (SAC 8.0) were released. SAC is the current version certification base client software which can manage both Aladdin eToken Pro and Safenet iKey security devices. SAC combined the features of Aladdin PKI Client and Safenet boarderless Security software.
- 2011.01 - (ISC)2 Safe & Secure Online program - Infosec awareness seminar.

Mr. Frankie Leung (CISA, CISM, CRISC, CISSP) joined Volunteers for (ISC)2 Safe & Secure Online program - Infosec awareness seminar. This seminar was targeting to educate students in the primary and secondary schools how to use internet resources securely. The online safety tips were introduced Some Cyber-crime cases were introduced to those students to let them understand the serious of misusage of Internet and not to perform any hacking behavior.
On Jan 11 of 2011, more than 400 P3 to P6 students are attended this seminar at S.K.H. Ho Chak Wan Primary School (http://www.skhhcw.edu.hk/).
The Video of this event can be reviewed at http://www.youtube.com/watch?v=_x8R4HdxWFY
- 2010.07 - “Data Leakage and Protection” at Information Security Seminar 2010.

Mr. Frankie Leung (Principal Consultant & Business Manger, USD Data Systems Ltd) made a public speech on the topic of “Data Leakage and Protection” at “Information Security Seminar 2010”. This seminar is join-organized by Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT), the Office of the Government Chief Information Officer (OGCIO) and Hong Kong Police Force (HKPF).
Mr. Frankie Leung (CISA, CISM, CISSP) represented UDS to conduct this seminar to educate the public the importance of Data Protection and the common scenarios on Data Leakage at Tuen Mun Town Hall on May 28 of 2010. More than 200 general public (Schools, businesses and individuals) attended this event.
- 2010.07 - UDS carries ScriptLogic solutions for Hong Kong Region.

ScriptLogic Corporation, a wholly owned subsidiary of Quest Software (Nasdaq: QSFT), is a recognized leader in the management, monitoring and support of desktops, servers and networks. ScriptLogic’s award winning solutions benefit 28,000 customers worldwide in the areas of desktop, help desk, active directory, server and network management. IT professionals and organizations of all sizes rely on ScriptLogic to streamline administrative tasks and improve productivity through “Point, Click, Done” solutions.
ScriptLogic provides software solutions to help organizations accomplish their strategic business goals by offering affordable, yet enterprise quality products that focus on these key areas of Windows Management: indows Desktop Management Solutions, Network Management Solutions, Server and Active Directory solutions, Help Desk Solutions .
- 2010.06 - UDS is appointed by Centrify (www.centrify.com) as their Regional Value Added Distributor for Hong Kong, China, India, Singapore, Malaysia, Macau and Taiwan.
Centrify offers Active Directory Solutions for Securing Heterogeneous Systems and Applications. It enables organizations to strengthen security, enhance compliance efforts, and reduce operational costs by centrally managing their heterogeneous systems and applications using Active Directory. More than 2000 enterprise customers, including over 40% of the Fortune 50, have selected the Centrify Suite for its quick-to-deploy and easy-to-manage approach for securing their heterogeneous computing environment.
Centrify's solutions address the needs of IT organizations for: IT Security & Compliance, UNIX & Linux Identity Management, Mac OS Desktop Management, SAP & Web Single Sign-On,
Centrify Suite of solutions enables organizations to reduce IT expense and complexity, improve end-user productivity through single sign-on, strengthen security and enhance regulatory compliance initiatives.
- 2010.04 - UDS is selected as FortiNet FortiDB database security solution partner

UDS Data Systems Limited, a gold solution partner of Fortinet, is pleased to announce that UDS is the selected solution provider of the mark leading database security system Fortinet FortiDB in Hong Kong and Macau region.
FortiDB is the most comprehensive solution to secure databases and applications such as ERP, CRM, SCM and custom applications. It supports varies database systems such as Oracle, Sybase, SQL Server, DB2 and MySQL. FortiDB enhances database security by providing vulnerability assessment, database activity monitoring, auditing and compliance, attack alerting functions.
By providing FortiDB with other encryption, and database log analysis solution, UDS now offers the most completed database security solutions to address every aspect of database security such as database encryption, database vulnerability assessment, auditing and compliance, activity monitoring, log analysis and data leakage alerting and prevention.
FortiDB is a very cost-effective database security solution. The entry price for FortiDB 400B (for 10 databases) is starting from only HK$98,000 including installation service. To know more information about database security, please contact us at hotline (852) 28510271 or email info@udshk.com
- 2010.03 - UDS is selected as HID On The Desktop solution partner

HID Global, the trusted worldwide leader in providing solutions for the delivery of security identity, is pleased to announce that UDS Data Systems Ltd has been recognized as HID on the Desktop authorized resellers in Hong Kong since its launch in 2009. HID on the Desktop channel partners are customer-focused resellers who benefit from the exclusive sale of HID on the Desktop solutions and extensive HID Academy training, enabling them to enhance customer value by delivering quality Genuine HID solutions and superior end-user support to their customers.
HID on the Desktop™ makes log-in fully convenient for all users, and painless for IT to install and implement, by delivering the same afordable, user-friendly elements to logical access control that support our physical access control platforms. HID on the Desktop solutions are: Simple and convenient to use; Able to improve risk management; Easy to install and maintain; Reliable and secure.
- 2010.03 - UDS was invited to FortiNet APAC conference in Macau

Mr. Frankie Leung, Director of UDS Data Systems Ltd met Mr. Ken Xie (Founder, CEO and President) of Fortinet Inc in Fortinet International Conference at Macau on March 09 2010. More that 60 countries and 300 persons were in this 3 days conference.
A video was played to show the Fortinet being listed in NASDAQ which in 4 quarter of 2009. FortiDB, FortiMail and FortiOS 4.2 were heavily introduced in this conference. SIS International Ltd was awarded as the Best Support Distributor in the event
Fortinet (NASDAQ: FTNT) is a worldwide provider of network security appliances and the market leader in unified threat management (UTM). In Feb of 2010, Fortinet has shipped its consolidated network security appliances have surpassed 500,000 units.
- 2010.01 - UDS Data Systems Ltd enters SIEM (Security Incidents and Events Management) market with Splunk Software.
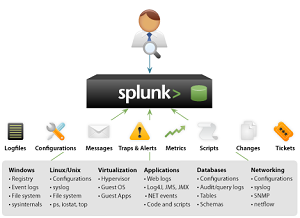
Splunk is software that provides unique visibility across your entire IT infrastructure from one place in real time. Only Splunk enables you to search, report, monitor and analyze all your real-time streaming and historical IT data from the same interface. Now you can troubleshoot application problems and investigate security incidents in minutes instead of hours or days, monitor to avoid service degradation or outages, deliver compliance at lower cost and gain new business insights from your IT data.
Splunk indexes any kind of IT data from any source in real time. Point your servers’ or network devices’ syslog at Splunk, set up WMI polling, monitor live logfiles, enable change monitoring on your filesystem or the Windows registry, or schedule a script to grab system metrics. Splunk indexes all your IT data without the need for any specific parsers or adapters to purchase, write or maintain. Both the raw data and the rich index are stored in an efficient, compressed, filesystem-based datastore with optional data signing and auditing for data integrity. The more data you index, the more insight you'll gain from your IT infrastructure.
The attached figure are extracted from www.splunk.com
- 2009.12 - CMS (Confidential Mail System) seminar to Hong Kong Government

UDS and SecureAge’s Confidential SecureEmail was approved by OCCIO for as CMS plug-in solution
UDS and SecureAge co-developed Confidential SecureEmail for Lotus Notes 8.5 was approved by OGCIO as one of standard Confidential Email Systems (CMS) plug in solution in Dec of 2009.
OCGCO also arranged a seminar for Lotus Domino 8.5 and CMS plug-in on Dec 8 209 at OGCIO Training room at Level 5, CyberPort One, Cyberport. There are around 100 persons from various departments from LAN administrators and ITMU Officers attended this seminar.
Mr. Keith Lam, Consultant and CMS PM of UDS Data Systems demonstrated the new feature of SecureAge’s Confidential SecureEmail and Mr. Frankie Leung, Business Manager of UDS Data Systems also presented the current technology on Smartcard, security etoken and SmartCard Reader which are working with SecureAge’s Confidential SecureEmail and other CMS plug-in solutions.
- 2009.08 - Sophos APAC conference in Manila and UDS become Sophos platinum partner
-

It was the first partner event after Sophos completed the acquisition of Utimaco Safeware. This partner conference was called “One Sophos” at .Dusit Thani Hotel Metro Manila, Philippines
UDS Data Systems has carried Utimaco Safeware (now Sophos) encryption solutions since 2002. Started in 2008, UDS also helped Utimaco Hong Kong for both pre-sales and post-sales service in both government and commercial sector. Before the Sophos acquisition, UDS was very active in Sophos solution. UDS won the largest Anti-spam tender from a Hong Kong List Company using Sophos Pure Message solution to protecting over 20000 email user accounts from spam.
More, UDS is now the Sophos platinum partner to deliver both Sophos solutions and services in the region.
- 2009.06 - "RFID and Its Related Application" Seminar and Trial” at Government
-

UDS participated in the "RFID and Its Related Application" Seminar and Trial” at Government. There are more than 80 attendances from the multiple departments.
UDS was invited by by the IT Innovation Section of the Office of the Government Chief Information Officer (OGCIO) to participate this seminar and show case at OGCIO office at Level 5, CyberPort One, CyberPort in June of 2009.
Mr Craig Sandness, Managing Director, HID Global, Asia Pacific, made an opening speech on the topic of “HID on the Desktop: RFID Cards that Open Doors and Windows”. Mr. Frankie Leung, Business Manager, UDS Data Systems Ltd, presented the HID HOTD solution with the Omnikey 5321 Contactless Reader, HID naviGo software, HID Crescendo contactless card to demonstrate how to use the same door access iClass contactless card to open the door and to authenticate the Windows OS.
- 2009.06 - UDS is awarded government contract on multi factors authentication system tender
- UDS is awarded a government contract on multi factor authentication solution. In this project, UDS provide a unique approach to enhance the original window authentication to a multi factor authentication approach. The authentication factors include fingerprint, contact based smartcard, PIN and Digital Certificate. The authentication solution also provides single sign on function to automatically sign on the day to day use windows application.
- 2009.03 - UDS establish partnership with i-Sprint Innovation
- UDS is partnered with i-Sprint Innovation to provide enterprise class unified authentication solution to our customers. i-Sprint Innovation’s integrated enterprise-class solutions provide centralize administration, authorization, authentication, single sign-on and provide audit trails of access to their business applications. I-Sprint unique Security Consolidation methodology helps organizations of all sizes to address their authentication management needs by using an incremental, evolutionary and strategic approach based on a common security infrastructure philosophy.
- 2008.10 - UDS upgraded to the first PGP® Silver Partner in Asia.

In Oct of 2008, UDS Data Systems Ltd is upgraded from PGP Brown Partner to first PGP Silver Partner in Asia. UDS has carried PGP Since 2002. Now UDS has one PGP Universal certification engineer and two PGP Universal certification technicians to support all PGP products including PGP Desktop Profession, PGP NetShare, PGP Whole Disk Encryption, PGP Email, PGP Command Line and PGP Universal Server.
The PGP® Silver Partner level is for integrators, solution providers, and resellers with experience in delivering PGP encryption solutions with a high level of customer satisfaction. PGP Silver Partners have the ability to sell and support PGP® encryption solutions. This partnership level enjoys an enhanced benefits portfolio plus access to PGP internal resources that complement sales and marketing tools and support.
The PGP® Global Partner Program delivers clarity, consistency, and focus for resellers and systems integrators to successfully sell and support PGP® solutions.
- 2008.03 - UDS attended Aladdin conference in Bangkok

UDS, the key partner of Aladdin in Hong Kong was invited by Aladdin to attend the Asia Pacific Partner Conference. The conference was held on March 2008 in Bangkok, Thailand.
Mr Frankie Leung and Mr Frank Yip participated in this conference. During the conference we shared our Aladdin eToken business and technical experience, success storied with Aladdin and its other partners in APAC.
UDS has provided Aladdin eToken solution since 2005. In the past few years, Aladdin eToken solution has been successfully adopted by Hong Kong government, large enterprises and finance institutes.
- 2008.02 - UDS attended Fortinet APAC conference in Sanya
-

As the Fortinet Gold Partner in Hong Kong, UDS was invited by Mr. Ken Xie (CEO, Fortinet, Inc) for the Fortinet APAC Partner Conference. The conference was held on Feb 27 to 28th of 2008 at Sanya, Hainan Island, China.
Mr Vinton Yau (Sales Manager) and Mr Frankie Leung (Business Manager) took part in this event. They met Mr Ken Xie and the other senior management of Fortinet and shared the business experience on selling the UTM appliance in this region. UDS was the only Gold Partner being invited by Fortinet for this event. UDS has provided Fortinet solution since 2002. Our Major customers are Universities, Large Enterprise, Finance Institutes and Telecomm operators.



